Cisco StealthWatchは、分散ネットワーク全体の包括的な脅威監視を提供する情報セキュリティ分析ソリューションです。 StealthWatchは、ルーター、スイッチ、その他のネットワークデバイスからのNetFlowおよびIPFIXの収集に基づいています。その結果、ネットワークは敏感なセンサーになり、管理者は次世代ファイアウォールなどの従来のネットワークセキュリティ方法が到達できない場所を探すことができます。
以前の記事ですでにStealthWatchについて書いています:最初の洞察と機能、およびデプロイメントと構成。次に進んで、アラームに対処する方法と、ソリューションが生成するセキュリティインシデントを調査する方法について説明します。6つの例があり、私は製品の有用性の良いアイデアを提供したいと思います。
まず、StealthWatchには、アルゴリズムとフィード用のトリガーがいくらか分散されていると言う必要があります。1つ目はあらゆる種類のアラーム(通知)であり、トリガーされると、ネットワーク上の疑わしいものを検出できます。2つ目はセキュリティインシデントです。この記事では、アルゴリズムトリガーの4つの例とフィードの2つの例について説明します。
1.ネットワーク内の最も大量の相互作用の分析
StealthWatchを構成する最初のステップは、グループごとにホストとネットワークを定義することです。ウェブインターフェースの[ 設定 ] > [ホストグループ管理 ]タブで、ネットワーク、ホスト、サーバーを適切なグループに分けます。独自のグループを作成することもできます。ところで、Cisco StealthWatchでのホスト間の相互作用の分析は、ストリームごとの検索フィルターだけでなく結果自体も保存できるため、非常に便利です。
まず、ウェブインターフェースで[ 分析 ] > [フロー検索 ]タブに移動します。次に、次のパラメータを設定する必要があります。
- 検索タイプ-上位の会話(最も人気のある相互作用)
- 時間範囲-24時間(期間、別の期間を使用できます)
- 検索名-内側から内側の上位の会話(わかりやすい名前)
- Subject — Host Groups → Inside Hosts ( — )
- Connection ( , )
- Peer — Host Groups → Inside Hosts ( — )
- Advanced Options , , ( , ). .
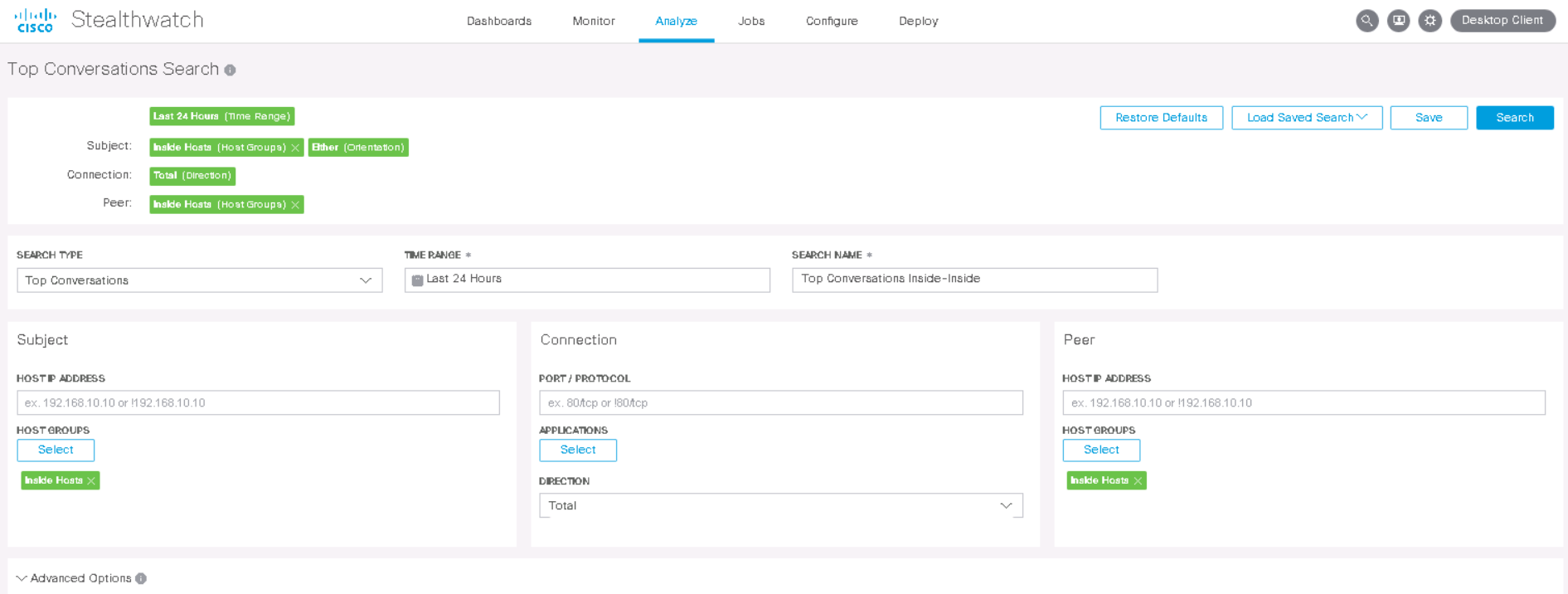
[ 検索 ]ボタンをクリックすると、インタラクションのリストが表示され、転送されたデータの量ですでにソートされています。
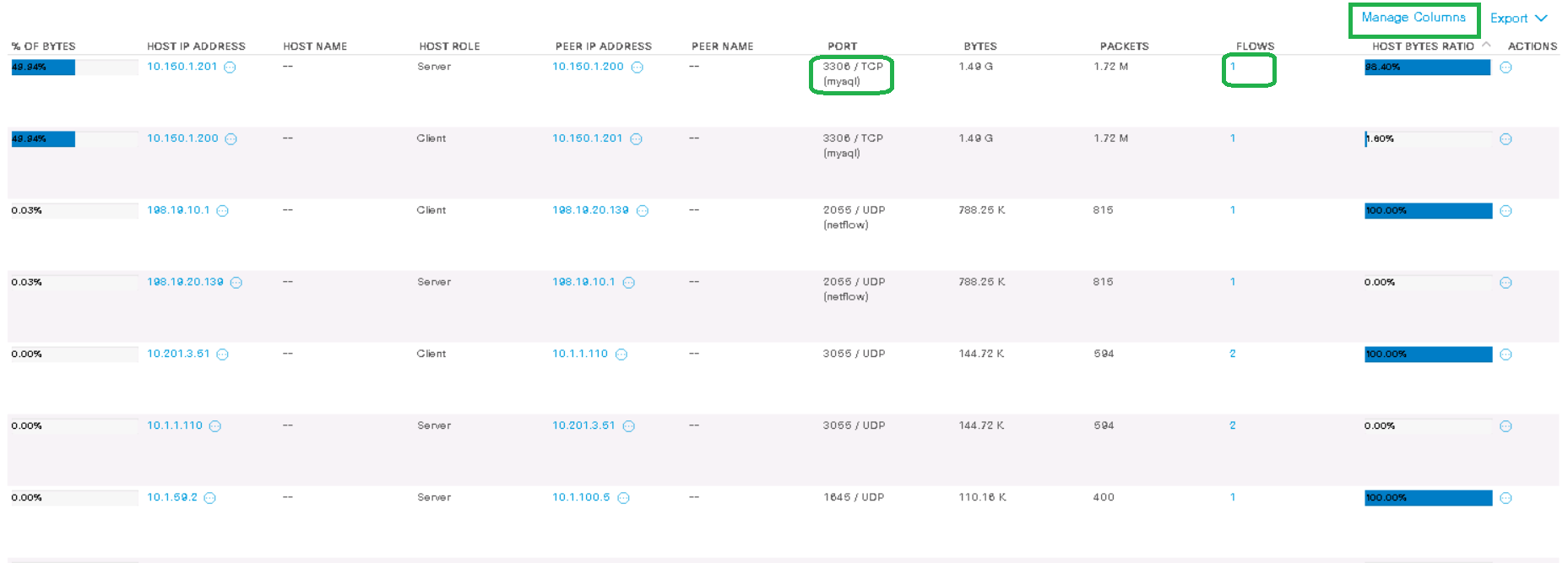
私の例では、ホスト10.150.1.201(サーバー)が1つのストリーム内で、mysqlプロトコルを使用して1.5 GBのトラフィックをホスト10.150.1.200(クライアント)に転送しました。[列の管理 ]ボタンを使用すると、出力にさらに列を追加できます。 さらに、管理者の裁量で、この種のやり取りに対して常にトリガーされ、SNMP、電子メール、またはSyslogを介して通知するカスタムルールを作成できます。
2.ネットワーク内で最も遅いクライアントとサーバーの相互作用の遅延の分析
SRT(サーバー応答時間)、RTT(往復時間) タグを使用すると、サーバーの待ち時間とネットワーク全体の待ち時間を確認できます。このツールは、遅いアプリケーションに関するユーザーの苦情の原因をすばやく見つける必要がある場合に特に役立ちます。
注:ほとんどすべてのNetflowエクスポーターは SRT、RTTタグを送信できないため、FlowSensorでそのようなデータを表示するには、ネットワークデバイスからのトラフィックのコピーの送信を構成する必要があります。次にFlowSensorは、拡張IPFIXをFlowCollectorに提供します。
管理者のコンピューターにインストールされているJavaアプリケーションStealtWatchでこの分析を実行する方が便利です。Inside Hostsを
右クリックし、タブに移動しますフローテーブル。
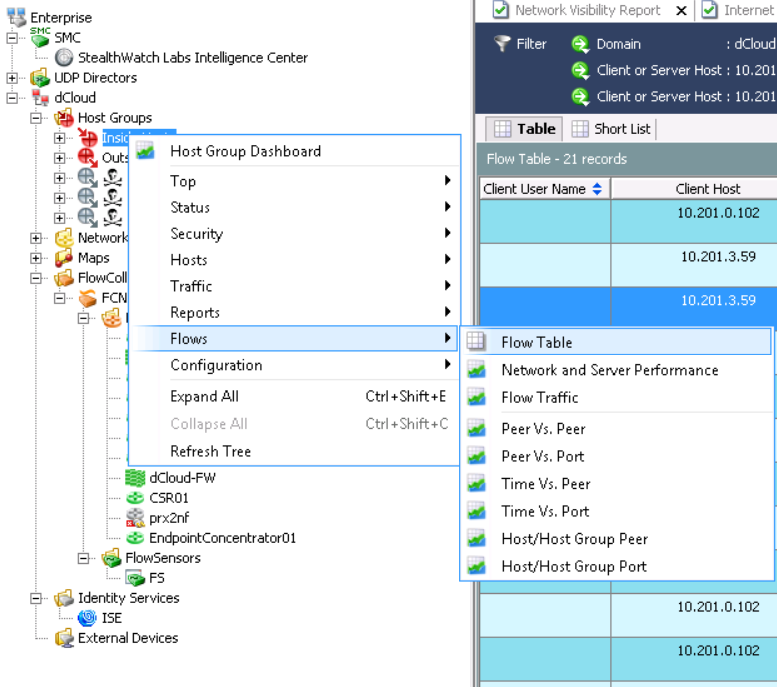
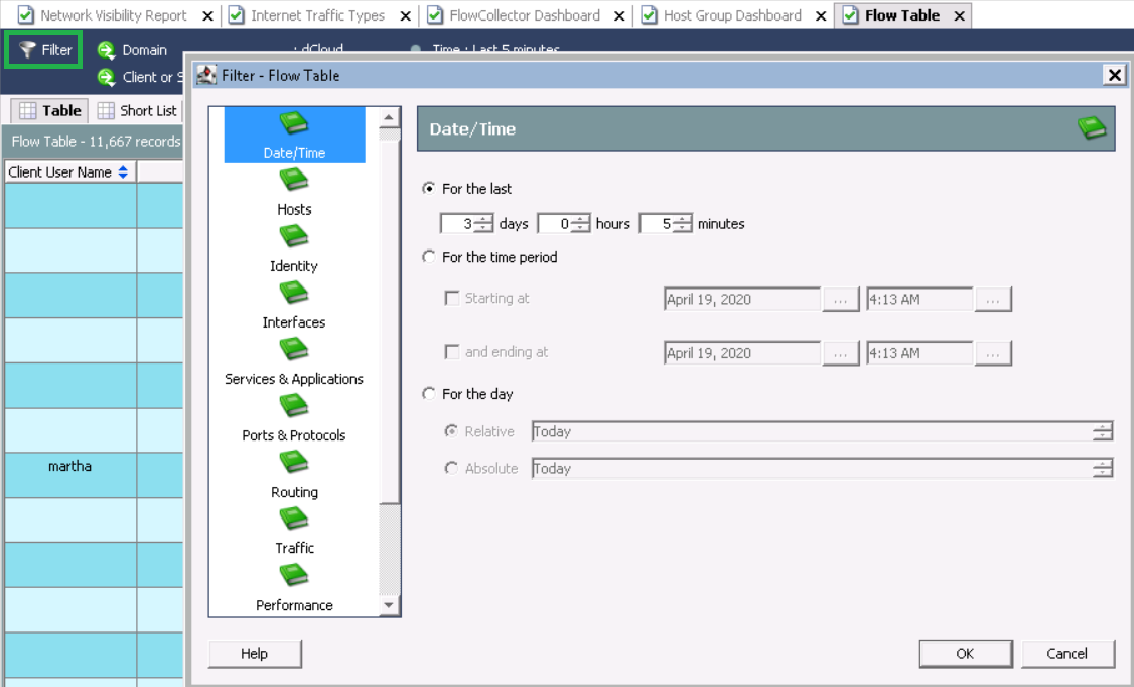
[ フィルター]をクリックして、必要なパラメーターを設定します。例として:
- 日付/時間-過去3日間
- パフォーマンス-平均往復時間> = 50ms
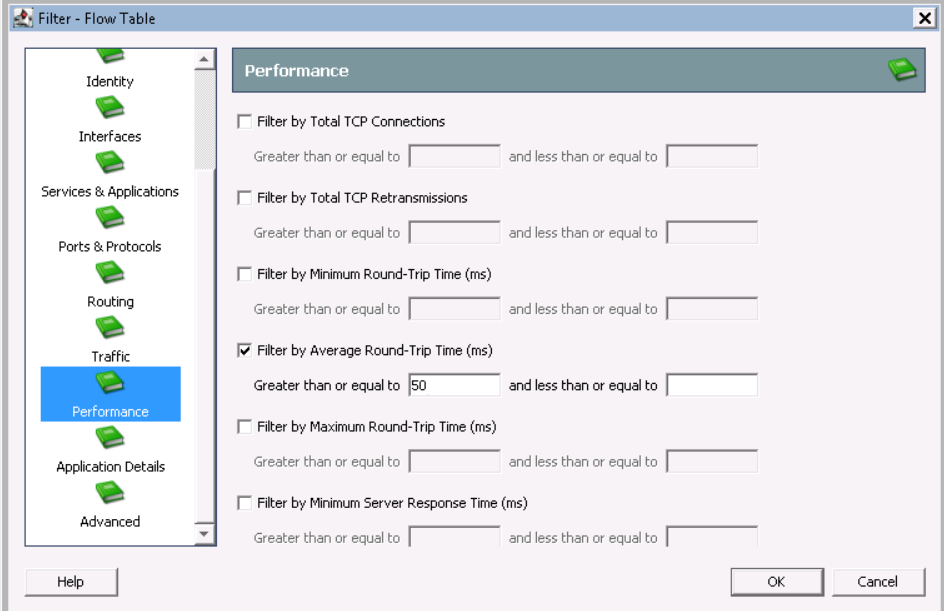
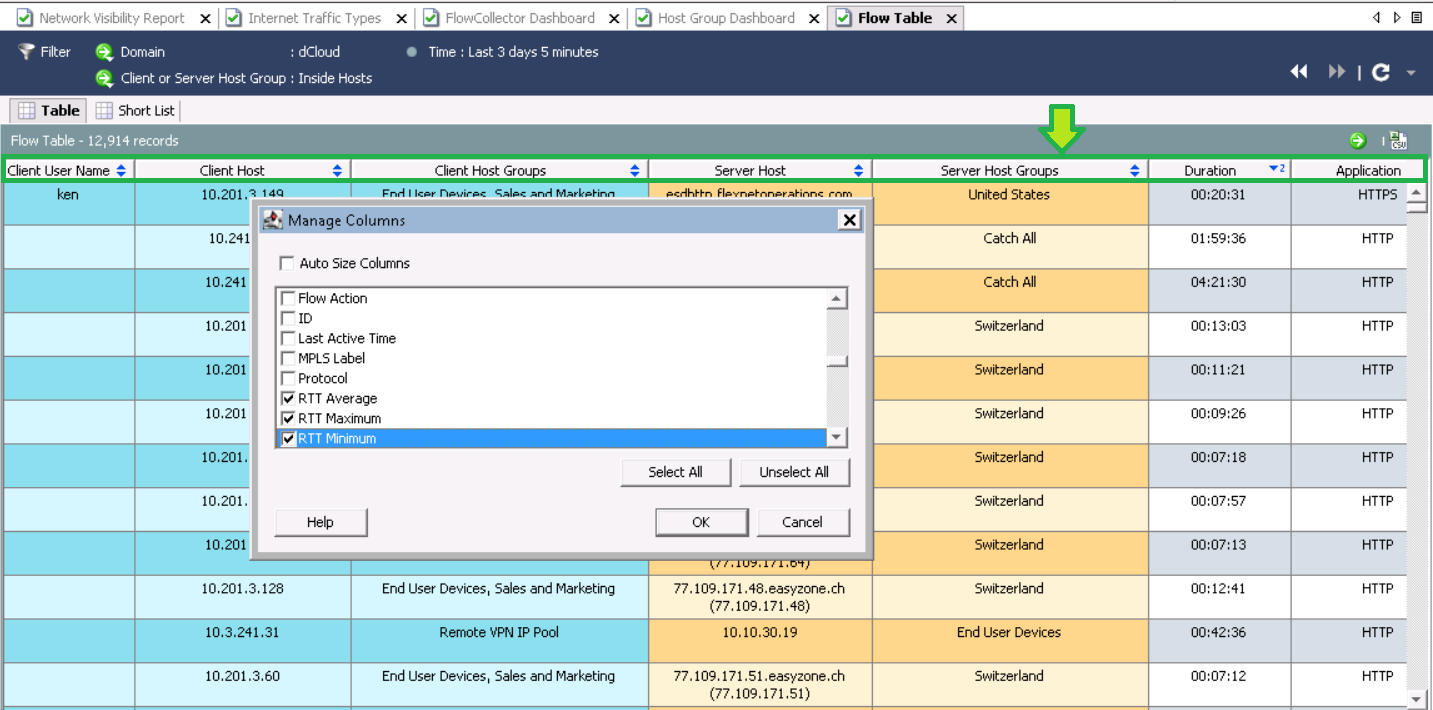
データを表示した後、関心のあるフィールドをRTT、SRTに追加します。これを行うには、スクリーンショットの列をクリックし、[列の管理 ]を右クリックします。次に、RTT、SRTパラメータをクリックします。
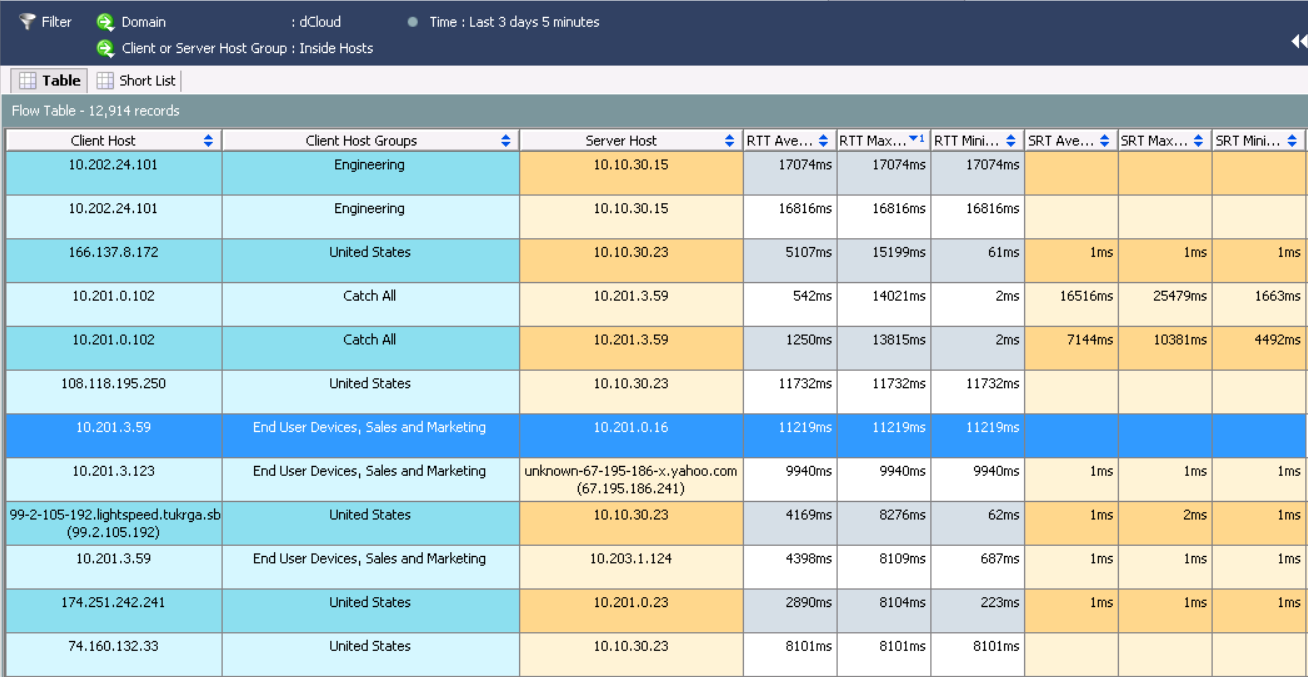
リクエストを処理した後、RTTの平均で並べ替え、最も遅い対話を確認しました。
詳細情報に分類するには、フローを右クリックして、[ フローのクイックビュー]を選択します。
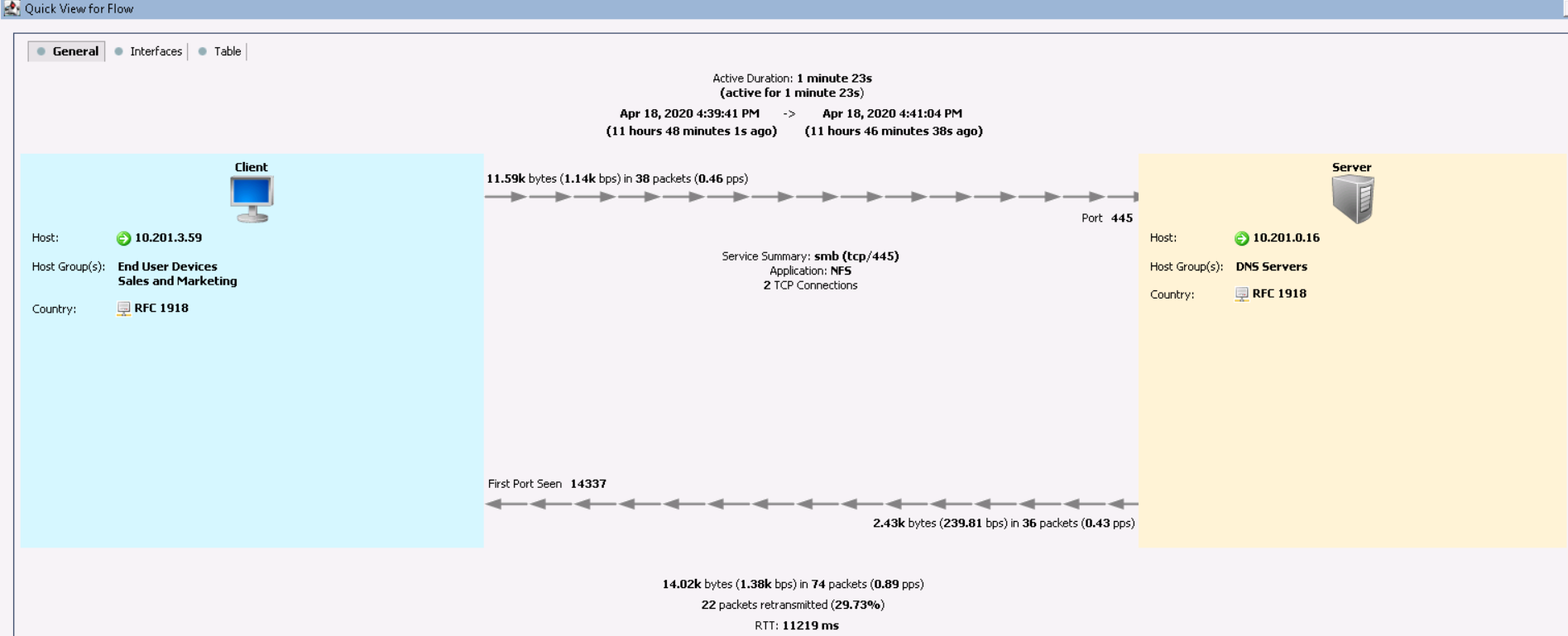
この情報は、ホストことを示唆している10.201.3.59グループからの販売およびマーケティングのプロトコルNFSはを参照するDNSサーバ 1分23秒とひどい遅延を持っています。 [ インターフェース ]タブどのNetflowデータエクスポーターから情報が受信されたかを確認できます。[ テーブル ]タブには、相互作用に関する詳細情報が表示されます。
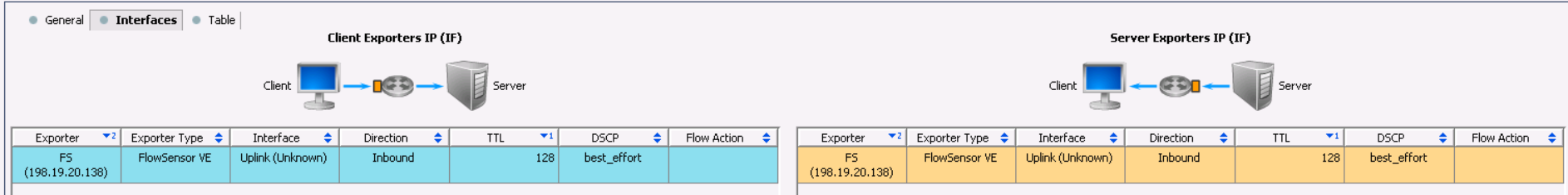
次に、FlowSensorにトラフィックを送信しているデバイスを見つける必要があります。問題はおそらくそこにあります。
さらに、StealthWatchは、データの重複排除を実行する(同じストリームを組み合わせる)点で独特です。したがって、ほとんどすべてのNetflowデバイスから収集でき、重複したデータが大量にあることを心配する必要はありません。まったく逆ですが、このスキームでは、どのホップが最大の遅延を持っているかを理解するのに役立ちます。
3.暗号プロトコルHTTPSの監査
ETA(暗号化トラフィック分析)は、暗号化されたトラフィックの悪意のある接続を復号化せずに検出する、シスコが開発したテクノロジーです。さらに、このテクノロジーにより、HTTPSをTLSバージョンと接続に使用される暗号化プロトコルに「解析」できます。この機能は、弱い暗号規格を使用するネットワークノードを検出する必要がある場合に特に役立ちます。
注:最初にStealthWatch- ETA暗号化監査にネットワークアプリをインストールする必要があります。
[ ダッシュボード ]タブ→ [ ETA暗号化監査 ]に移動し、分析するホストグループを選択します。全体像を把握するには、[ Inside Hosts]を選択します。
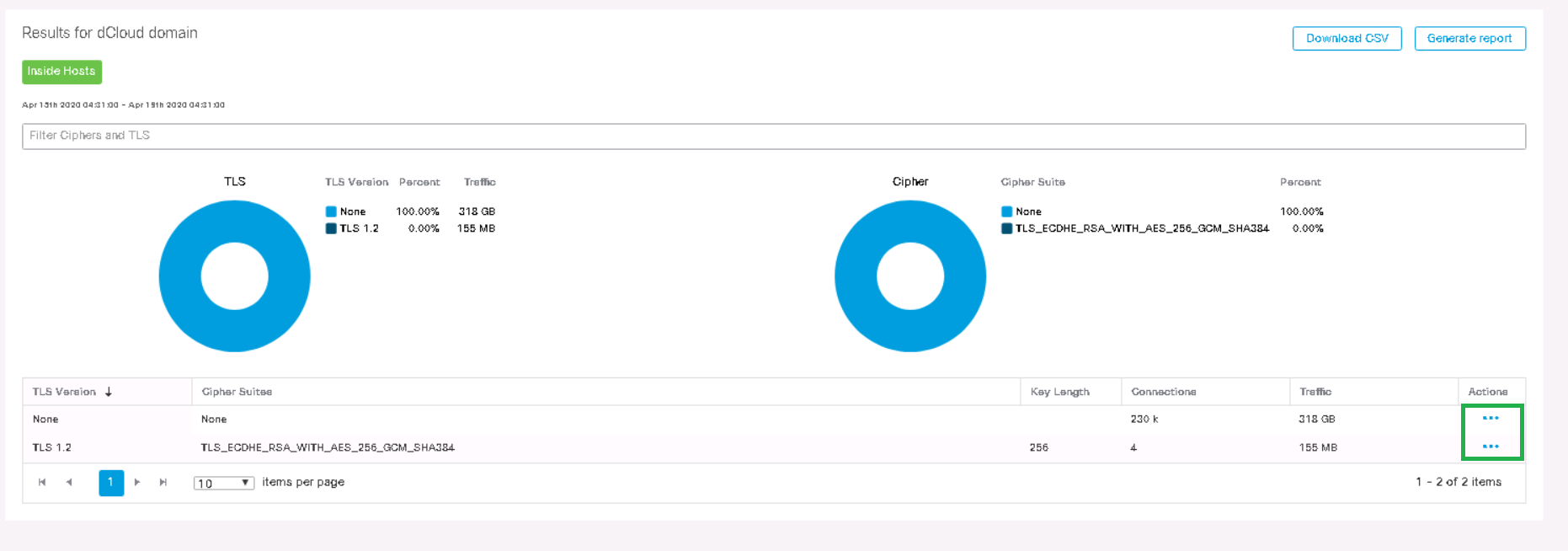
TLSバージョンと対応する暗号規格が表示されていることを確認できます。[ アクション ]列の通常のスキームに従って、[フローの表示]に移動し、新しいタブで検索を開始します。
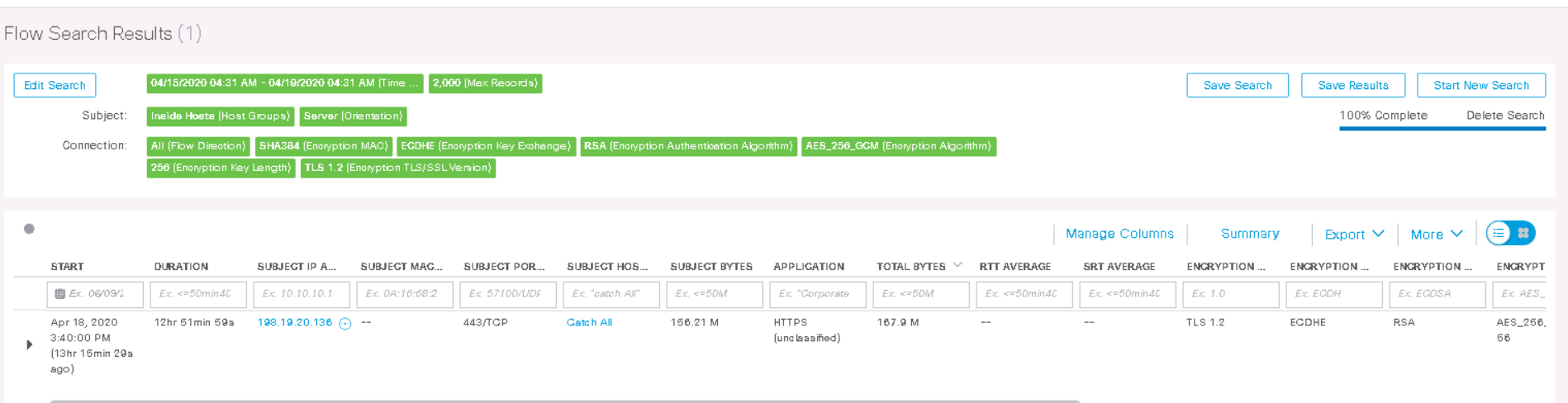
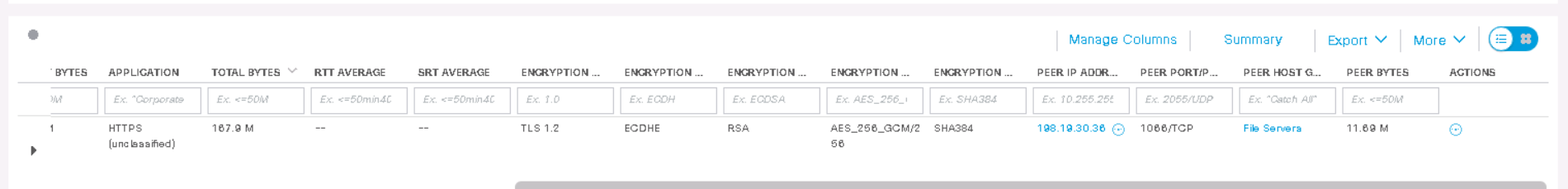
出力から、ホスト198.19.20.136がTLS 1.2 でHTTPSを12時間使用しており、暗号化アルゴリズムがAES-256で、ハッシュ関数がSHA-384であることがわかります。したがって、ETAを使用すると、ネットワーク内の弱いアルゴリズムを見つけることができます。
4.ネットワーク異常の分析
Cisco StealthWatchは、コアイベント(セキュリティイベント)、関係イベント(セグメント、ネットワークのノード間の相互作用のイベント)、および動作分析の 3つのツールを使用して、ネットワーク内のトラフィック異常を認識できます。
次に、行動分析を使用すると、特定のホストまたはホストのグループの経時的な行動のモデルを構築できます。この分析により、StealthWatchを通過するトラフィックが増えるほど、トリガーがより正確になります。最初は、システムが多くの誤ったトリガーをトリガーするため、ルールを手動で「ねじる」必要があります。システムは自動的に調整されるか、例外に追加されるため、最初の数週間はこのようなイベントに注意を払わないことをお勧めします。
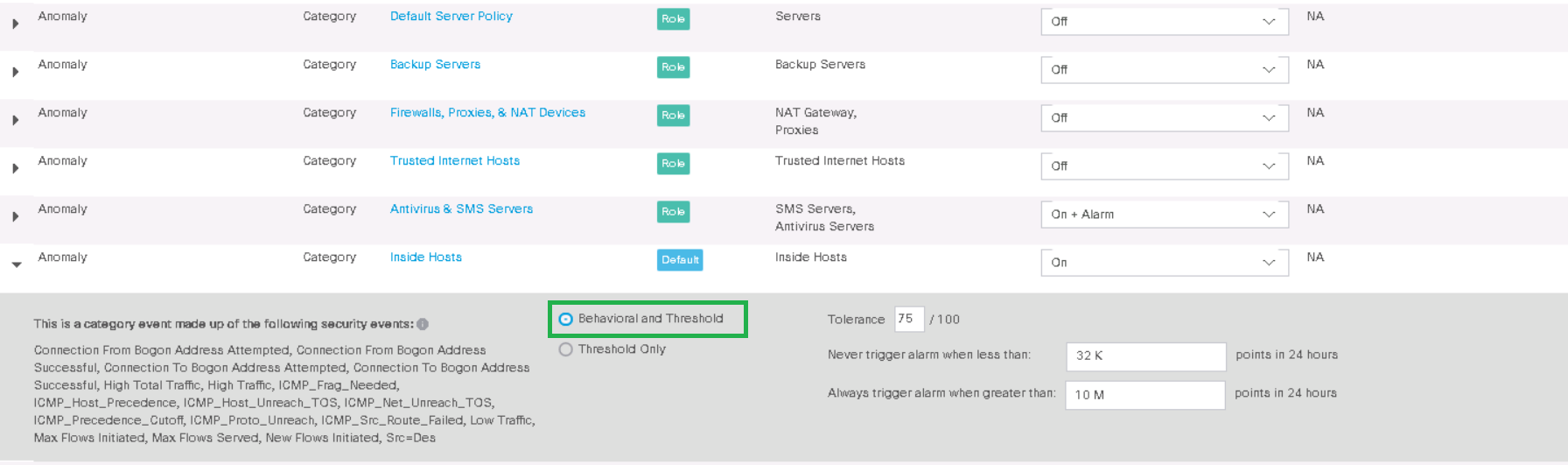
以下は、事前設定されたルールの例です異常。これは、Inside HostsグループのホストがInside Hostsグループと対話し、トラフィックが24時間で10メガバイトを超えると、イベントがアラームなしで発生することを示しています。
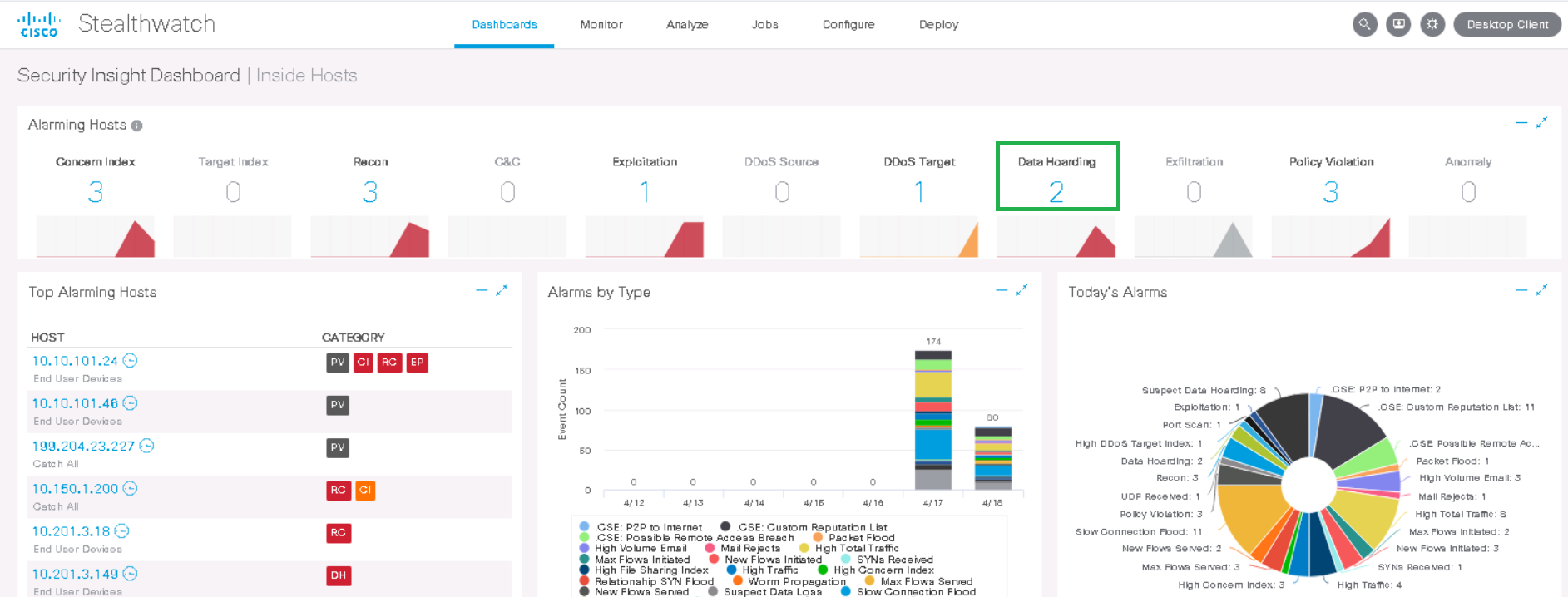
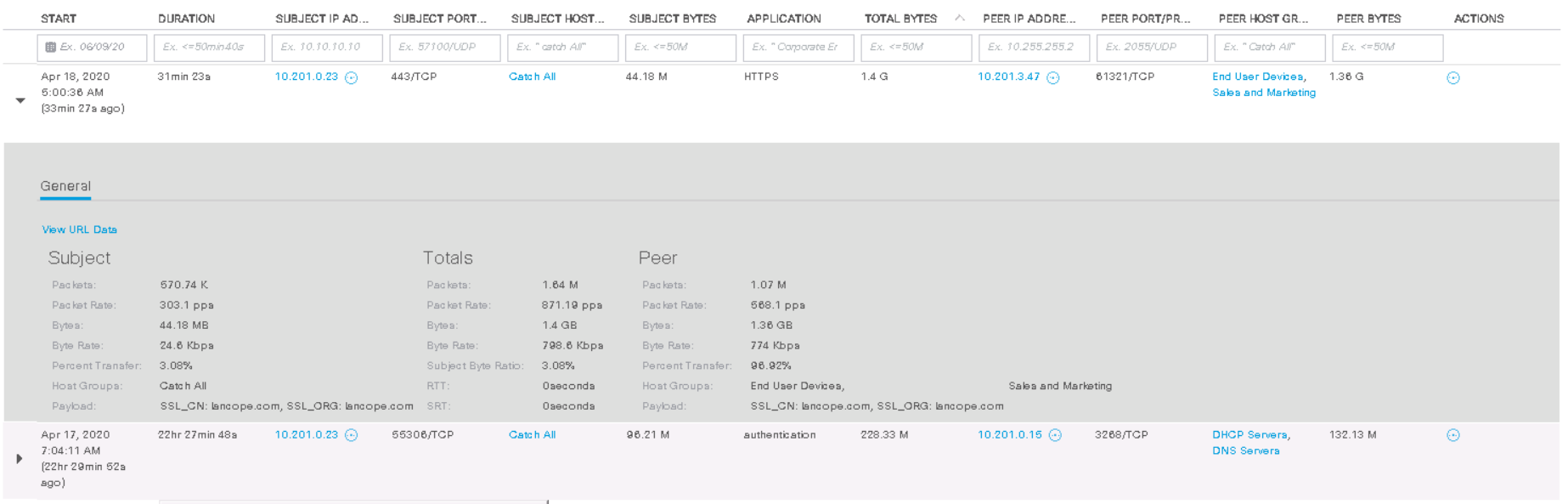
たとえば、Data Hoardingアラームを受け取ります。これは、一部のソース/宛先ホストがホストグループまたはホストから異常に大量のデータをダウンロード/ダウンロードしたことを意味します。イベントをクリックして、トリガーするホストが示されているテーブルに移動します。次に、Data Hoarding列で対象のホストを選択します。
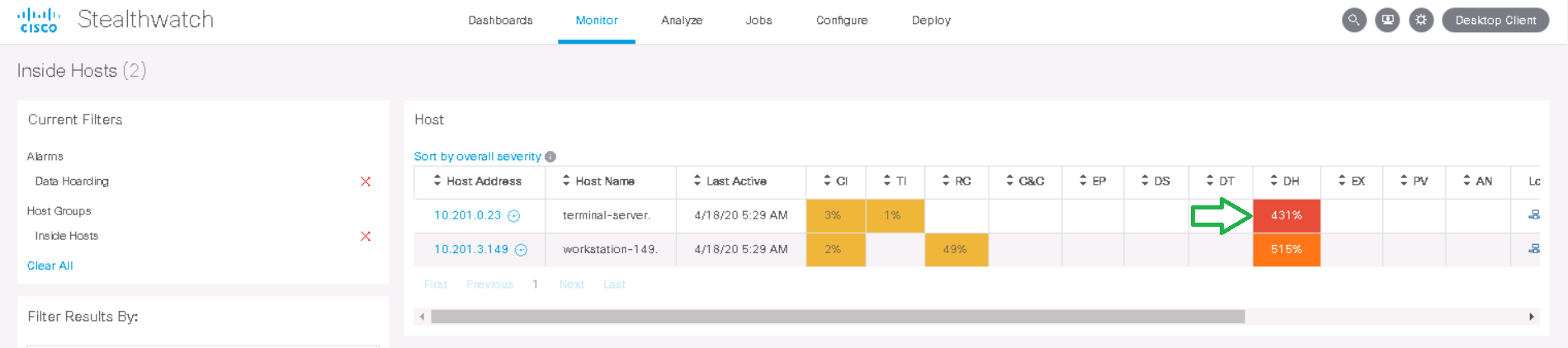
162kの「ポイント」が見つかり、ポリシーによって100kの「ポイント」が許可されていることを示すイベントが表示されます。これらは内部のStealthWatchメトリックです。[ Actions ]列で、[ View Flows ]をクリックします。

我々はことを観察することができます。このホストは、ホストと夜に相互作用し10.201.3.47からのセールス&マーケティング部門を経て、HTTPSプロトコルと、ダウンロード1.4ギガバイトを。この例は完全には成功しないかもしれませんが、数百ギガバイトの相互作用の検出はまったく同じ方法で実行されます。その結果、異常のさらなる調査は興味深い結果につながる可能性があります。
注:SMC Webインターフェースでは、[ ダッシュボード]タブのデータは先週と[ モニター ]タブにのみ表示されます過去2週間。古いイベントを分析してレポートを生成するには、管理者のコンピューターでJavaコンソールを使用する必要があります。
5.内部ネットワークスキャンを見つける
次に、フィードのいくつかの例-情報セキュリティインシデントを見てみましょう。この機能は、セキュリティの専門家にとってより興味深いものです。
StealthWatchには、いくつかの事前設定タイプのスキャンイベントがあります。
- ポートスキャン-ソースは宛先ホストの複数のポートをスキャンします。
- Addr tcp scan-ソースは同じTCPポートを介してネットワーク全体をスキャンし、宛先IPアドレスを変更します。この場合、ソースはTCPリセットパケットを受信するか、まったく応答を受信しません。
- Addr udp scan-ソースは、宛先IPアドレスを変更しながら、同じUDPポートでネットワーク全体をスキャンします。同時に、送信元はICMPポート到達不能パケットを受信するか、応答を受信しません。
- Pingスキャン-ソースは、回答を見つけるためにネットワーク全体にICMP要求を送信します。
- Stealth Scan tp/udp — .
すべての内部スキャナーを同時により便利に配置するために、StealthWatch-可視性評価用のネットワークアプリがあります。ダッシュボード→可視性評価→内部ネットワークスキャナータブに移動すると、過去2週間のスキャン関連のセキュリティインシデントが表示されます。
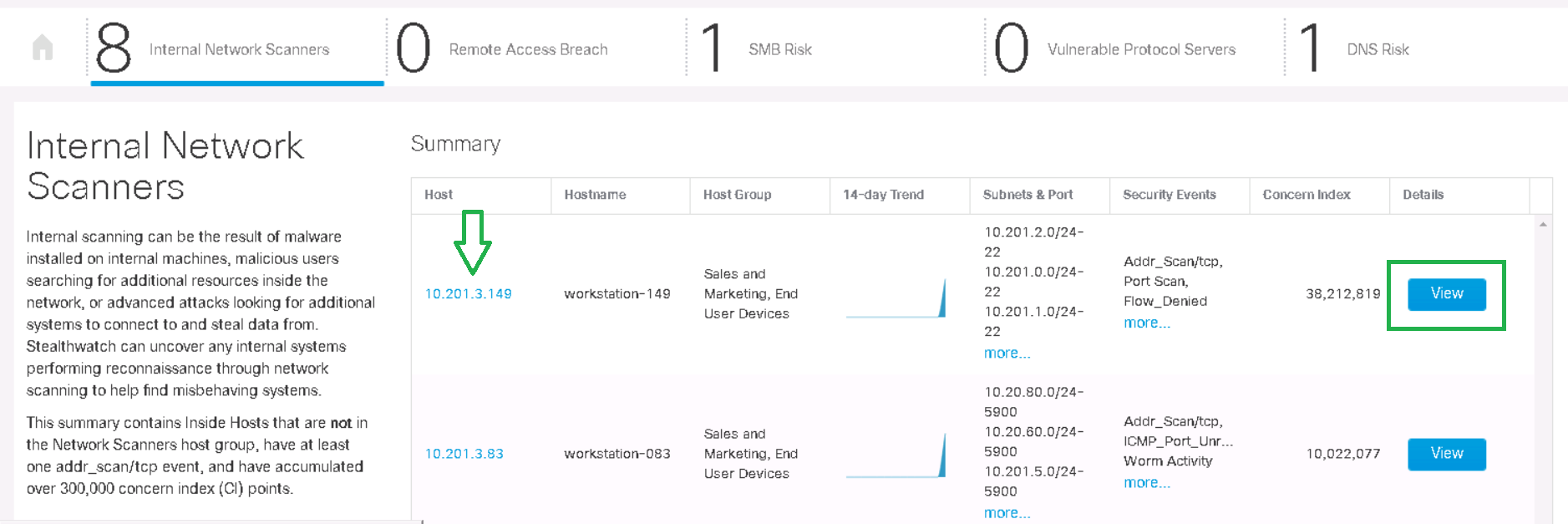
[ 詳細 ]ボタンをクリックすると、各ネットワークのスキャンの開始、トラフィックの傾向、対応するアラームが表示されます。
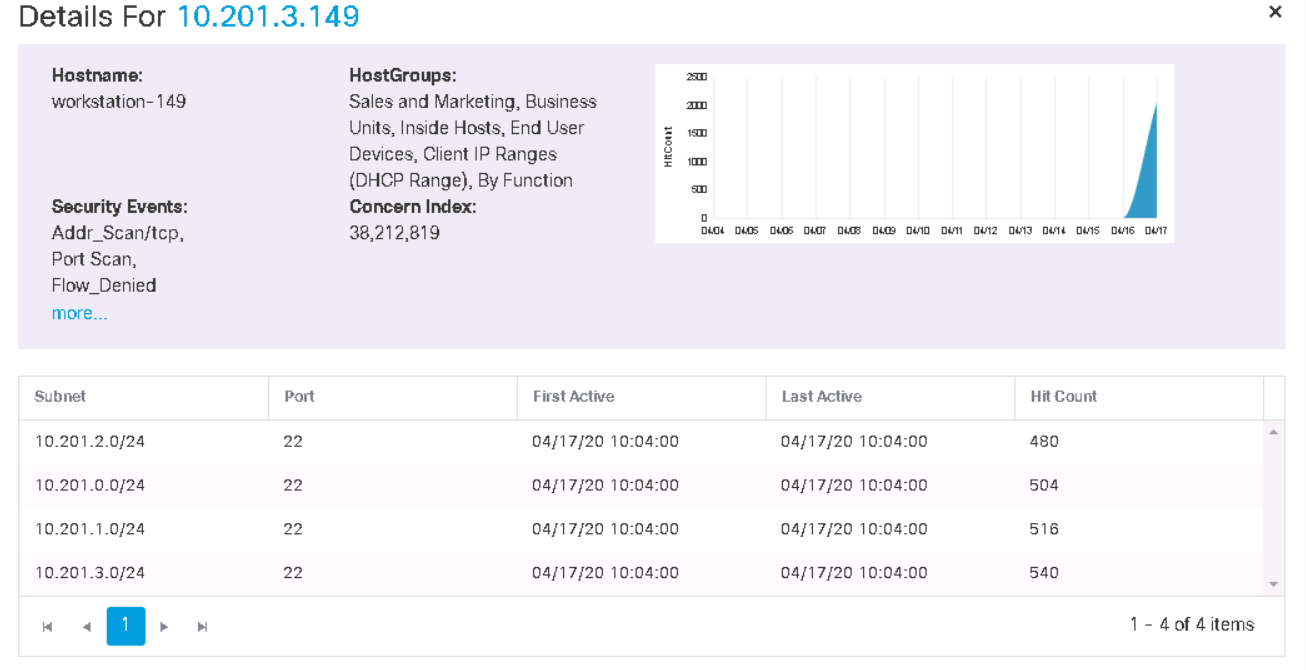
次に、前のスクリーンショットのタブからホストに「失敗」し、このホストの先週のセキュリティイベントとアクティビティを確認できます。
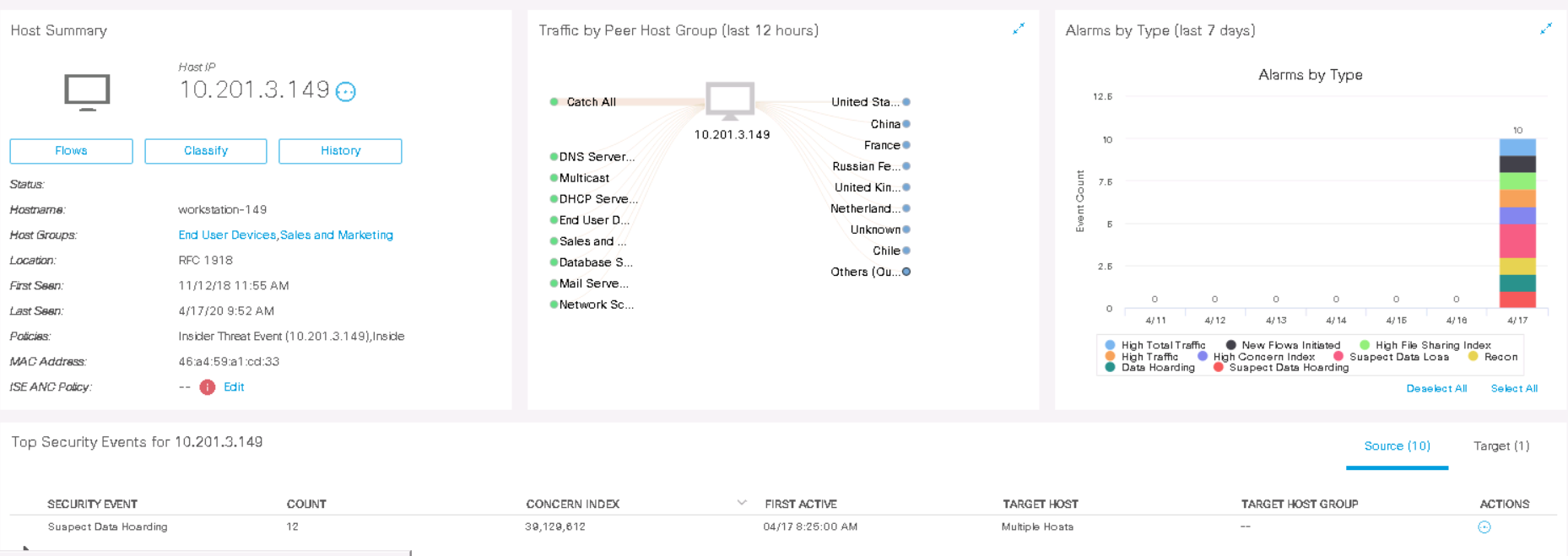
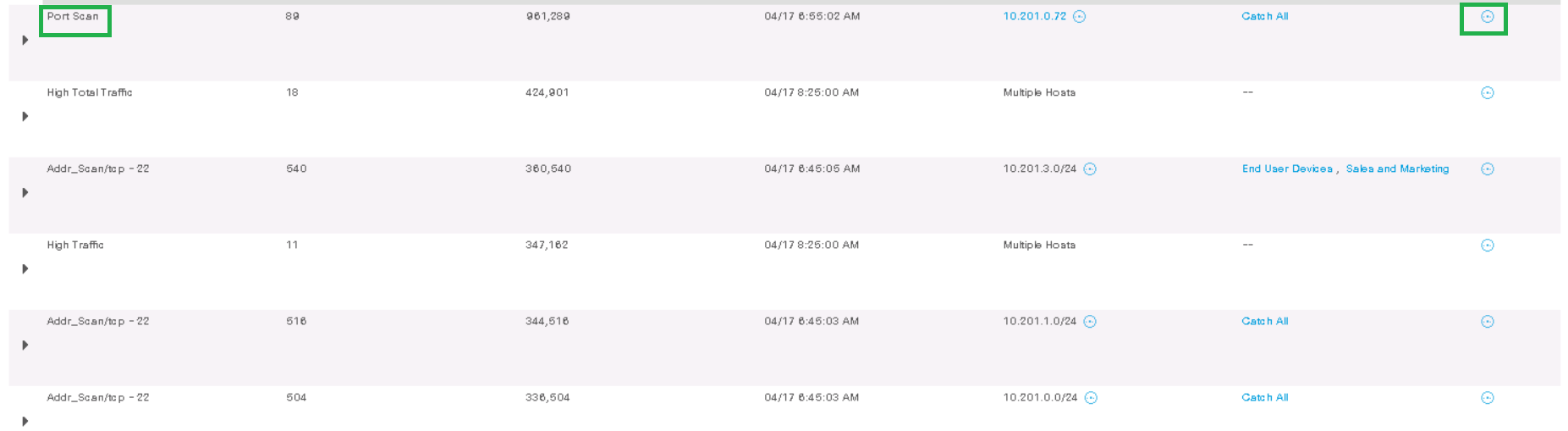
例として、ホスト10.201.3.149から10.201.0.72へのポートスキャンイベントを分析してみましょう。[ Actions ] > [Associated Flows ]をクリックします。ストリーム検索が開始され、関連情報が表示されます。
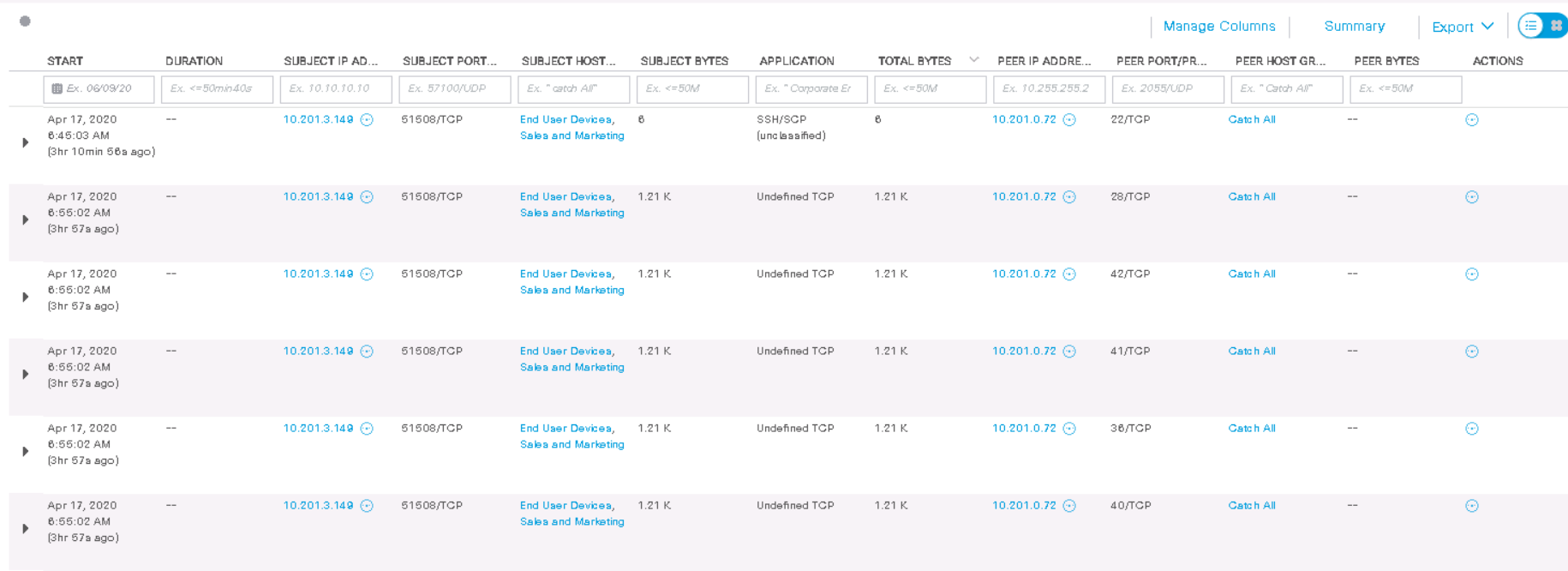
ご覧のとおり、ポート51508 / TCPの 1 つからのこのホストは、ポート22、28、42、41、36、40 (TCP)で 3時間前に宛先ホストをスキャンしました。すべてのNetflowフィールドがNetflowエクスポーターでサポートされているわけではないため、一部のフィールドは情報も表示しません。
6. CTAを使用したダウンロードされたマルウェアの分析
CTA(Cognitive Threat Analytics)は、Cisco StealthWatchと完全に統合され、シグネチャのない分析をシグネチャ分析で補完できるようにするシスコのクラウド分析です。これにより、トロイの木馬、ネットワークワーム、ゼロデイマルウェア、その他のマルウェアを検出し、ネットワーク内に拡散させることができます。また、前述のETAテクノロジーにより、暗号化されたトラフィックでこのような悪意のある通信を分析できます。
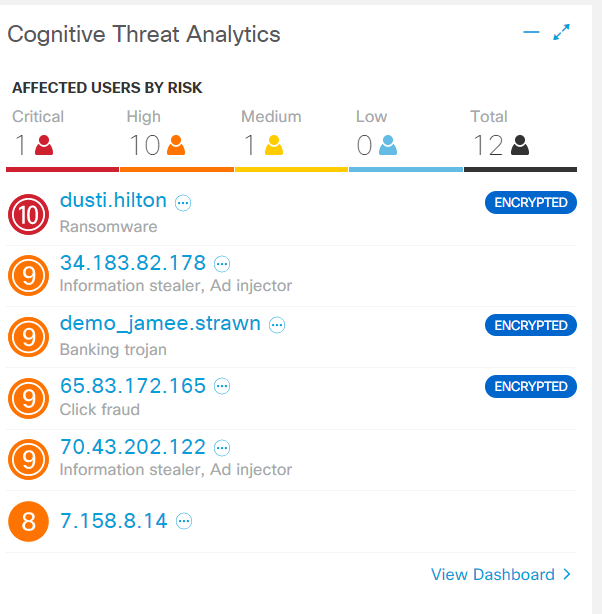
文字通り、Webインターフェースの最初のタブには、特別なCognitive Threat Analyticsウィジェットがあります。。短い要約は、ユーザーホストで検出された脅威について説明します:トロイの木馬、不正なソフトウェア、迷惑なアドウェア。 「暗号化された」という言葉は、まさにETAの仕事の証拠です。ホストをクリックすると、すべての情報、CTAログを含むセキュリティイベントがドロップアウトします。
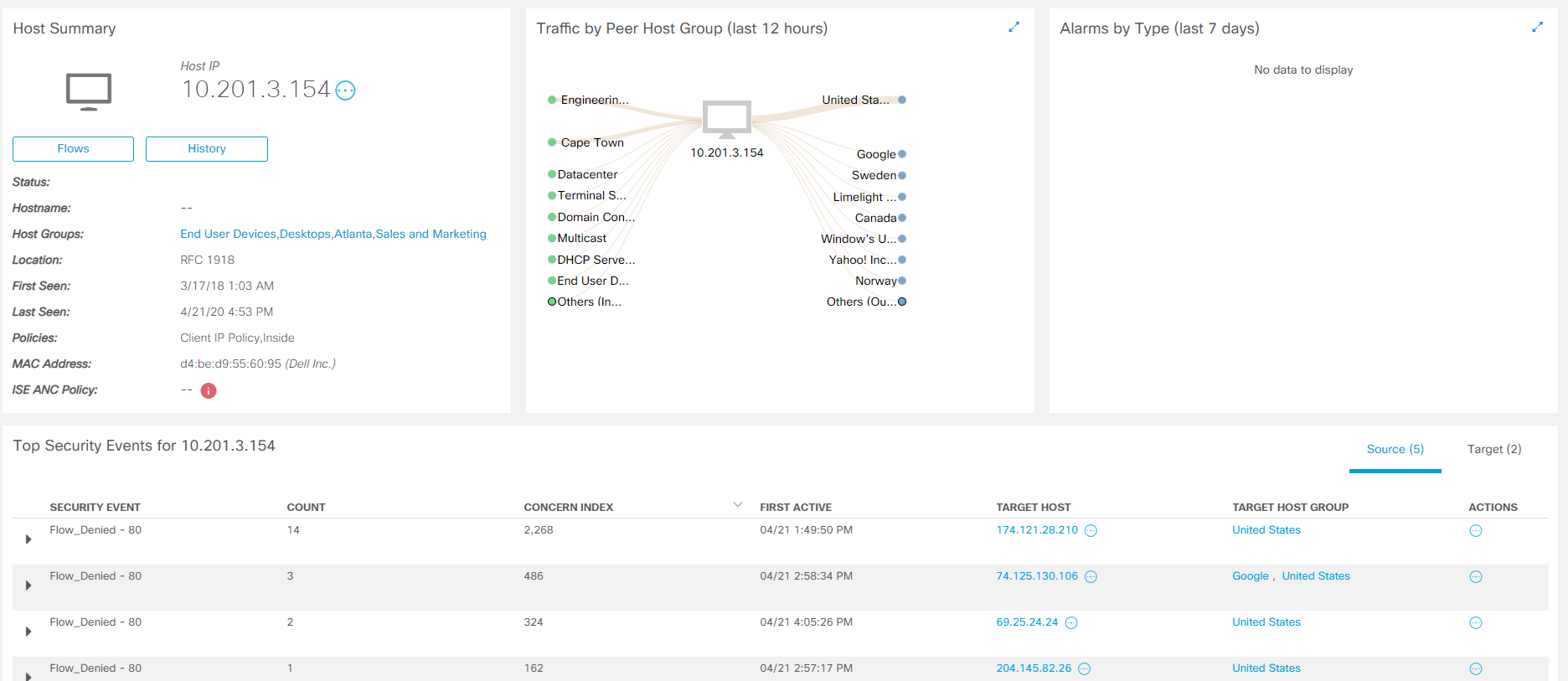
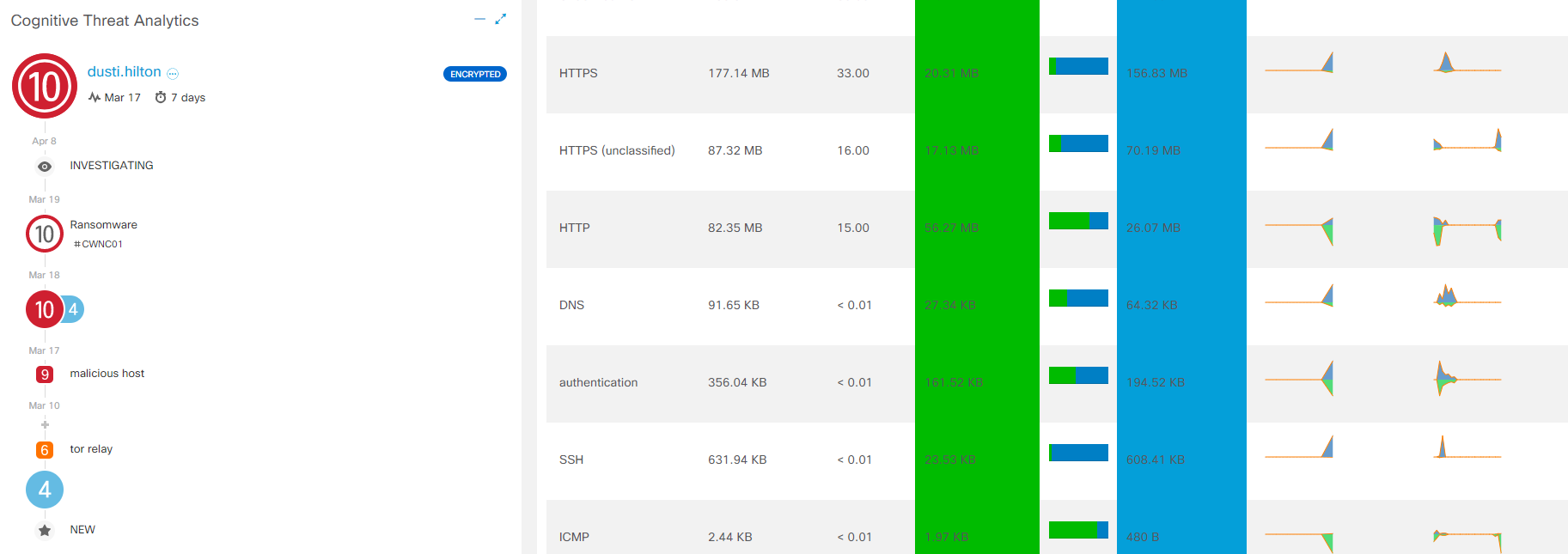
CTAの各段階に向けて、対話に関する詳細情報が表示されます。完全な分析を行うには、[ インシデントの詳細の表示 ]をクリックすると、別のCognitive Threat Analyticsコンソールが表示されます。
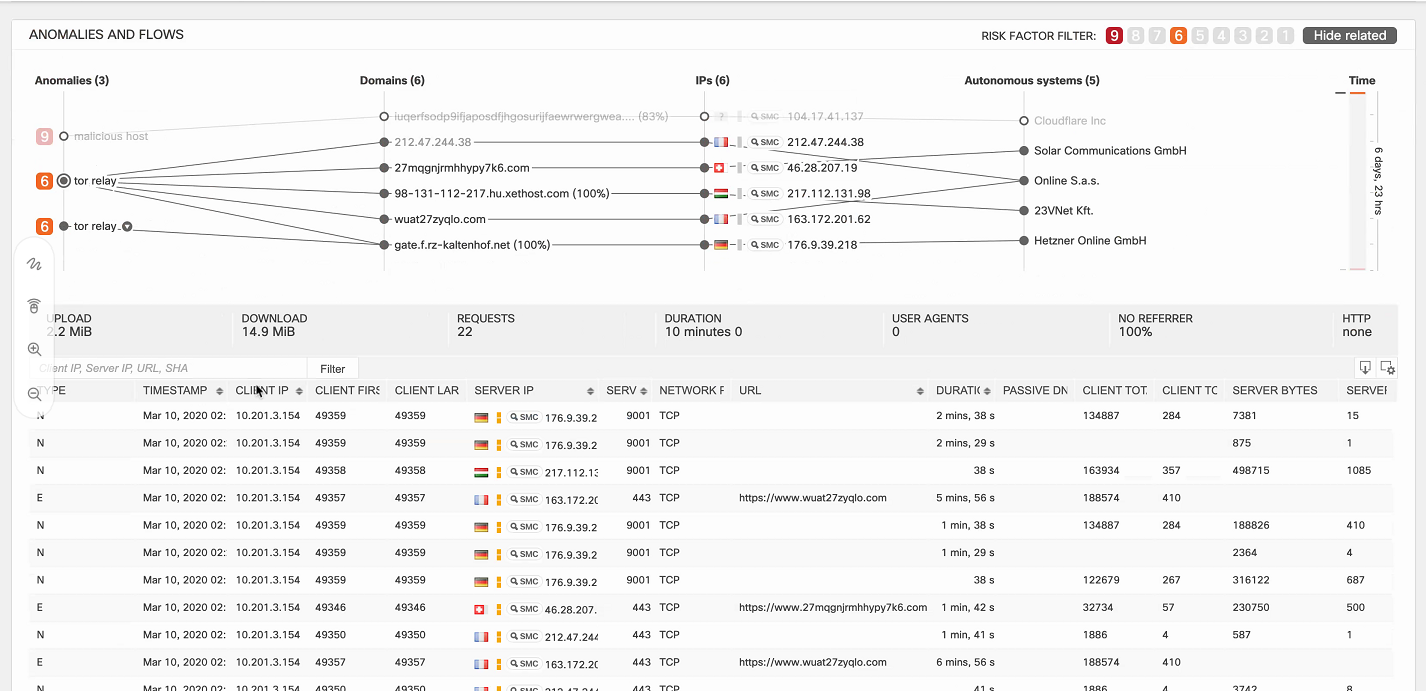
右上隅にあるフィルターを使用すると、重大度レベルごとにイベントを表示できます。特定の異常をポイントすると、画面の下部にログが表示され、対応するタイムラインが右側に表示されます。したがって、情報セキュリティ部門のスペシャリストは、どの感染ホストがどのアクションを実行した後、どのアクションを実行し始めたかを明確に理解します。
以下は別の例です-ホスト198.19.30.36に感染したバンキング型トロイの木馬。このホストは悪意のあるドメインと相互作用し始め、ログはこれらの相互作用のフローに関する情報を示します。
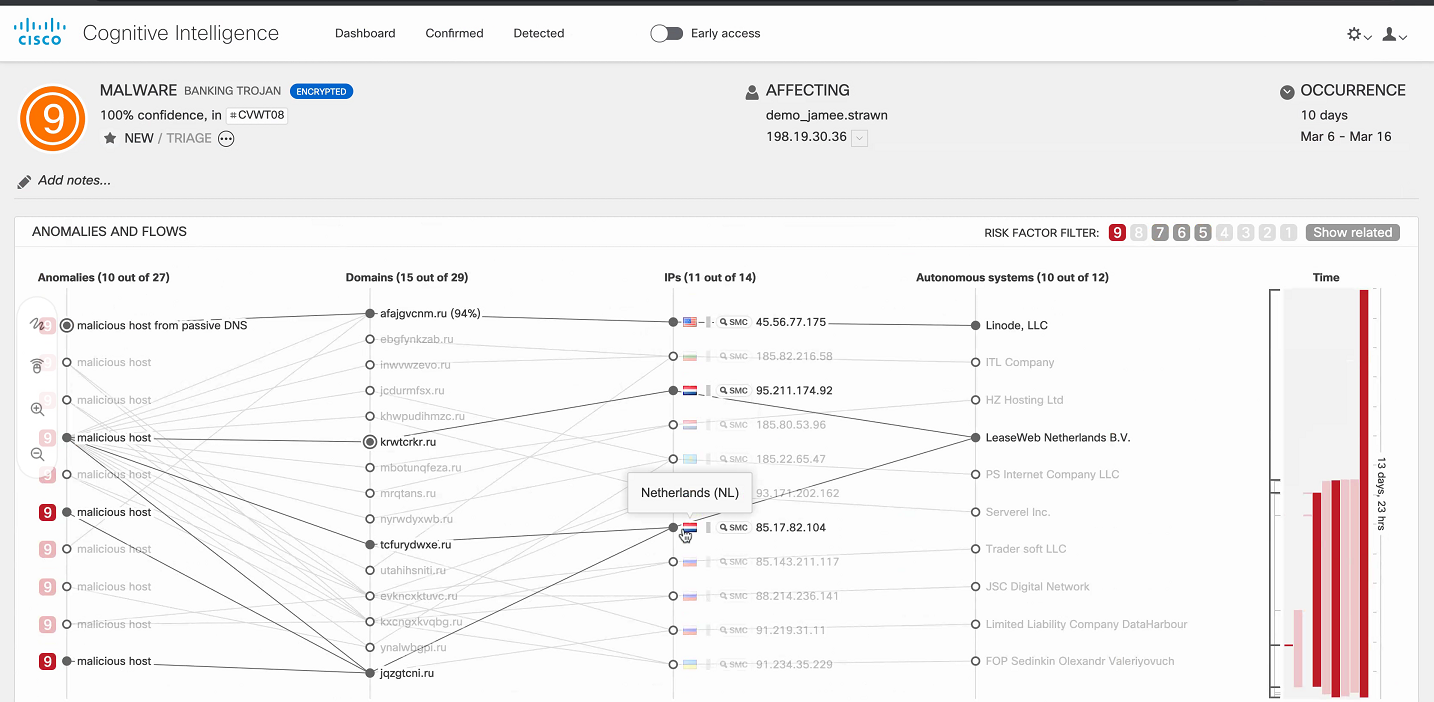
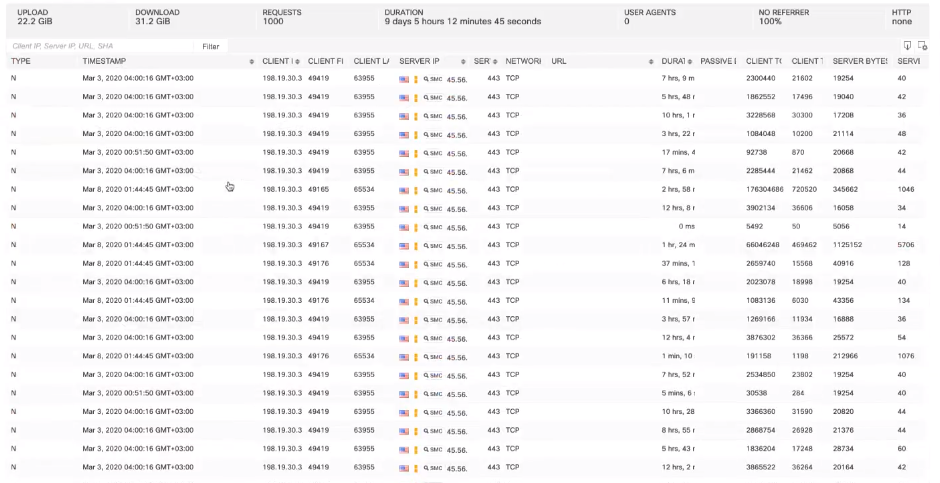
次に、最善の解決策の1つは、さらなる処理と分析のためにCisco ISEとネイティブに統合されているため、ホストを隔離することです。
結論
Cisco StealthWatchソリューションは、ネットワーク分析と情報セキュリティの両面で、主要なネットワーク監視製品の1つです。そのおかげで、ネットワーク内の不正な相互作用、アプリケーションの遅延、最もアクティブなユーザー、異常、マルウェア、APTを検出できます。さらに、スキャン、侵入テスター、HTTPSトラフィックの暗号監査の実施を見つけることができます。ここでは、さらに多くのユースケースを見つけることができます。
ネットワークですべてがスムーズかつ効率的に機能していることを確認したい場合は、リクエストを送信してください。
近い将来、さまざまな情報セキュリティ製品に関するいくつかの技術出版物を計画しています。このトピックに興味がある場合は、私たちのチャンネル(Telegram、Facebook、VK、TSソリューションブログ)!