LinuxセキュリティモジュールとSELinuxの背景
Security Enhanced Linuxは、Linuxシステムを潜在的な脅威から保護し、従来のUnixセキュリティシステムであるDiscretionary Access Control(DAC)の欠陥を修正するための、必須の役割ベースのアクセスモデルに基づく一連のルールとアクセスメカニズムです。このプロジェクトは、主に請負業者であるSecure Computing CorporationとMITRE、および多くの研究所が開発に直接関与した、米国国家安全保障局の腸から始まりました。
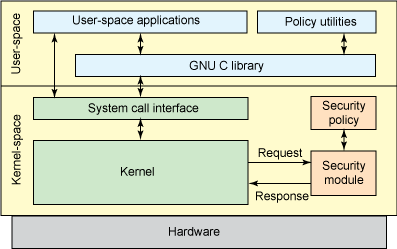
Linuxセキュリティモジュール
Linus Torvaldsは、アップストリームLinuxカーネルに含めることができるように、新しいNSA開発について多くのコメントをしました。彼は、オブジェクトを使用した操作を管理するための一連のインターセプターと、対応する属性を格納するためのカーネルデータ構造内の一連の保護フィールドを備えた一般的な環境について説明しました。次に、この環境をロード可能なカーネルモジュールで使用して、任意のセキュリティモデルを実装できます。 LSMは、2003年にLinuxv2.6カーネルに完全に組み込まれました。
LSMフレームワークには、データ構造内のガードフィールドと、カーネルコードの重要なポイントで関数をインターセプトしてそれらを管理し、アクセス制御を実行するための呼び出しが含まれています。また、セキュリティモジュールを登録するための機能も追加されます。/ sys / kernel / security / lsmインターフェースには、システム上のアクティブなモジュールのリストが含まれています。LSMフックはリストに格納され、CONFIG_LSMで指定された順序で呼び出されます。詳細なフックドキュメントは、include / linux /lsm_hooks.hヘッダーファイルに含まれています。
LSMサブシステムにより、同じ安定したLinuxカーネルv2.6の完全なSELinux統合が可能になりました。ほぼすぐに、SELinuxは安全なLinux環境の事実上の標準となり、最も人気のあるディストリビューションの一部になりました:RedHat Enterprise Linux、Fedora、Debian、Ubuntu。
SELinux用語集
- — SELinux , Unix/Linux user id, , . Linux SELinux. SELinux , , — .
- — SELinux , . . . , . — , . : sysadm_t , user_t, . init init_t, named named_t.
- — , SELinux. , . . Role Based Access Control (RBAC), SELinux.
- — Type Enforcement, , . , , , , , , . .
- — , . : , , ., , , — .
- SELinux — SELinux . SELinux , — — . , . .
LSM SELinux
名前にもかかわらず、LSMは一般的にLinuxロード可能モジュールではありません。ただし、SELinuxと同様に、カーネルに直接統合されています。 LSMソースコードを変更するには、新しいカーネルのコンパイルが必要です。対応するオプションをカーネル設定で有効にする必要があります。有効にしないと、起動後にLSMコードがアクティブ化されません。それでも、OSブートローダーオプションで有効にすることができます。
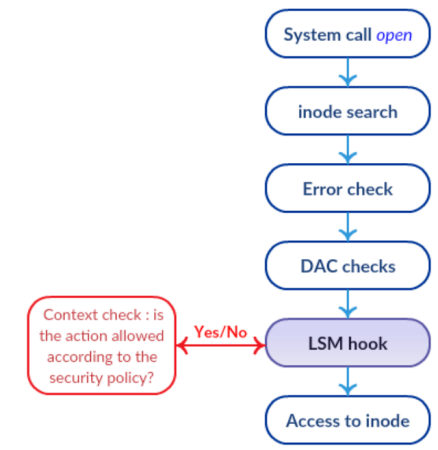
LSMチェックスタック
LSMには、チェックに関連する可能性のあるコアコア機能のフックが装備されています。 LSMの主な機能の1つは、それらがスタックされていることです。したがって、標準のチェックは引き続き実行され、各LSMレイヤーは追加のコントロールとコントロールのみを追加します。これは、禁止をロールバックできないことを意味します。これを図に示します。定期的なDACチェックの結果が失敗した場合、LSMフックにも到達しません。
SELinuxは、FlukeリサーチオペレーティングシステムのFlaskセキュリティアーキテクチャ、特に最小特権の原則を採用しています。この概念の本質は、その名前が示すように、意図したアクションを実行するために必要な権限のみをユーザーに付与するか、処理することです。この原則は、アクセスの強制型付けを使用して実装されるため、SELinuxアドミッション制御はドメイン=>型モデルに基づいています。
アクセスの強制入力により、SELinuxには、Unix / LinuxOSで使用される従来のDACモデルよりもはるかに重要なアクセス制御機能があります。たとえば、ftpサーバーで発生するネットワークポート番号を制限したり、特定のフォルダー内のファイルの書き込みと変更を許可したり、削除したりすることはできません。
SELinuxの主なコンポーネントは次のとおりです。
- Policy EnforcementServer-アクセス制御を整理するための主要なメカニズム。
- システムセキュリティポリシーのデータベース。
- LSMイベントインターセプターとの相互作用。
- Selinuxfs -Pseudo-FS、/ procと同じで、/ sys / fs / selinuxにマウントされます。実行時にLinuxカーネルによって動的に入力され、SELinuxステータス情報を含むファイルが含まれます。
- アクセスベクターキャッシュ-パフォーマンスヘルパー。
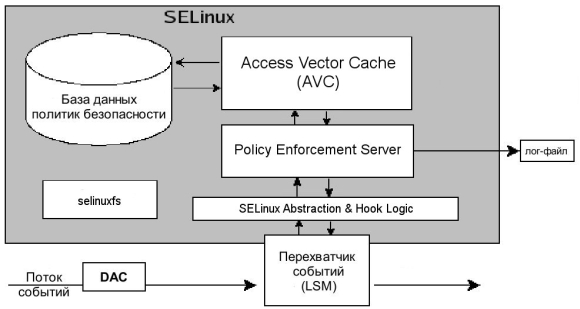
SELinuxのしくみ
これはすべて次のように機能します。
- 上の図に示すように、特定のサブジェクトは、SELinuxの用語では、DACチェック後にオブジェクトに対して許可されたアクションを実行します。操作を実行するこの要求は、LSMイベントインターセプターに送信されます。
- そこから、サブジェクトおよびオブジェクトのセキュリティコンテキストとともに、要求は、LSMとの対話を担当するSELinux抽象化およびフックロジックモジュールに渡されます。
- Policy Enforcement Serverは、オブジェクトへのサブジェクトのアクセスを決定するためのインスタンスであり、SELinuxAnHLからのデータがそこに届きます。
- アクセスまたは拒否について決定を下すために、Policy Enforcement Serverは、最も使用されているAccess Vector Cache(AVC)ルールのキャッシングサブシステムを参照します。
- 対応するルールの解決策がキャッシュに見つからない場合、要求はセキュリティポリシーデータベースに渡されます。
- DBおよびAVCからの検索結果は、ポリシー実施サーバーに返されます。
- 見つかったポリシーが要求されたアクションと一致する場合、操作は許可されます。それ以外の場合、操作は禁止されています。
SELinux設定の管理
SELinuxは、次の3つのモードのいずれかで動作します。
- 施行-セキュリティポリシーの厳格な順守。
- 許容-制限の違反は許可され、対応するマークがログに記録されます。
- 無効-セキュリティポリシーは有効ではありません。
次のコマンドを使用して、SELinuxがどのモードにあるかを確認できます。
[admin@server ~]$ getenforce
Permissive再起動する前にモードを変更する、たとえば、強制または1に設定します。permissiveパラメータは数値コード0に対応します。
[admin@server ~]$ setenfoce enforcing
[admin@server ~]$ setenfoce 1 #
ファイルを編集してモードを変更することもできます。
[admin@server ~]$ cat /etc/selinux/config# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
SELINUX=enforcing
# SELINUXTYPE= can take one of three values:
# targeted - Targeted processes are protected,
# minimum - Modification of targeted policy. Only selected processes are protected.
# mls - Multi Level Security protection.
SELINUXTYPE = targete setenfoceと
の違いは、オペレーティングシステムの起動時に、構成ファイルのSELINUXパラメーターの値に従ってSELinuxモードが設定されることです。さらに、<=>を無効にする変更は、/ etc / selinux / configファイルを編集して再起動した後にのみ有効になります。
簡単なステータスレポートを表示します。
[admin@server ~]$ sestatusSELinux status: enabled
SELinuxfs mount: /sys/fs/selinux
SELinux root directory: /etc/selinux
Loaded policy name: targeted
Current mode: permissive
Mode from config file: enforcing
Policy MLS status: enabled
Policy deny_unknown status: allowed
Max kernel policy version: 31
一部のネイティブユーティリティは、-Zパラメータを使用してSELinux属性を表示します。
[admin@server ~]$ ls -lZ /var/log/httpd/
-rw-r--r--. root root system_u:object_r:httpd_log_t:s0 access_log
-rw-r--r--. root root system_u:object_r:httpd_log_t:s0 access_log-20200920
-rw-r--r--. root root system_u:object_r:httpd_log_t:s0 access_log-20200927
-rw-r--r--. root root system_u:object_r:httpd_log_t:s0 access_log-20201004
-rw-r--r--. root root system_u:object_r:httpd_log_t:s0 access_log-20201011
[admin@server ~]$ ps -u apache -Z
LABEL PID TTY TIME CMD
system_u:system_r:httpd_t:s0 2914 ? 00:00:04 httpd
system_u:system_r:httpd_t:s0 2915 ? 00:00:00 httpd
system_u:system_r:httpd_t:s0 2916 ? 00:00:00 httpd
system_u:system_r:httpd_t:s0 2917 ? 00:00:00 httpd
...
system_u:system_r:httpd_t:s0 2918 ? 00:00:00 httpd通常のls-l出力と比較すると、次の形式の追加フィールドがいくつかあります。
<user>:<role>:<type>:<level>
最後のフィールドは、秘密スタンプのようなものを示し、2つの要素の組み合わせで構成されます。
- s0-重要度、低レベル-高レベル間隔とも表記
- c0、c1…c1023-カテゴリ。
アクセス構成の変更
semoduleを使用してSELinuxモジュールをロードし、それらを追加および削除します。
[admin@server ~]$ semodule -l |wc -l #
408
[admin@server ~]$ semodule -e abrt #enable -
[admin@server ~]$ semodule -d accountsd #disable -
[admin@server ~]$ semodule -r avahi #remove - 最初のコマンドsemanageloginは、SELinuxユーザーをオペレーティングシステムユーザーにバインドし、2番目のコマンドはそれをリストします。最後に、-rスイッチを指定した最後のコマンドは、SELinuxユーザーからOSアカウントへのマッピングを削除します。MLS / MCS範囲値の構文の説明は前のセクションにあります。
[admin@server ~]$ semanage login -a -s user_u karol
[admin@server ~]$ semanage login -lLogin Name SELinux User MLS/MCS Range Service
__default__ unconfined_u s0-s0:c0.c1023 *
root unconfined_u s0-s0:c0.c1023 *
system_u system_u s0-s0:c0.c1023 *
[admin@server ~]$ semanage login -d karol
semanage userコマンドをさSELinuxのユーザーとロール間のマッピングを管理するために使用されます。
[admin@server ~]$ semanage user -l
Labeling MLS/ MLS/
SELinux User Prefix MCS Level MCS Range SELinux Roles
guest_u user s0 s0 guest_r
staff_u staff s0 s0-s0:c0.c1023 staff_r sysadm_r
...
user_u user s0 s0 user_r
xguest_u user s0 s0 xguest_r
[admin@server ~]$ semanage user -a -R 'staff_r user_r'
[admin@server ~]$ semanage user -d test_uコマンドパラメータ:
- -カスタムロールマッピングエントリを追加します。
- -lユーザーと役割の間の対応のリスト。
- -dユーザー定義の役割マッピングエントリを削除します。
- -Rユーザーに割り当てられた役割のリスト。
ファイル、ポート、ブール
各SELinuxモジュールには、ファイルをマークするための一連のルールが用意されていますが、必要に応じて独自のルールを追加することもできます。たとえば、Webサーバーに/ srv / wwwフォルダーへのアクセス権を持たせたいとします。
[admin@server ~]$ semanage fcontext -a -t httpd_sys_content_t "/srv/www(/.*)?
[admin@server ~]$ restorecon -R /srv/www/最初のコマンドは新しいマーキングルールを登録し、2番目のコマンドは現在のルールに従ってファイルタイプをリセットまたは設定します。
同様に、TCP / UDPポートは、対応するサービスのみがリッスンできるようにマークされています。たとえば、Webサーバーがポート8080でリッスンするには、コマンドを実行する必要があります。
[admin@server ~]$ semanage port -m -t http_port_t -p tcp 8080かなりの数のSELinuxモジュールには、ブール値をとることができるパラメーターがあります。このようなパラメータの全リストは、getsebool-aで確認できます。あなたはsetseboolでブール値を変更することができます。
[admin@server ~]$ getsebool httpd_enable_cgi
httpd_enable_cgi --> on
[admin@server ~]$ setsebool -P httpd_enable_cgi off
[admin@server ~]$ getsebool httpd_enable_cgi
httpd_enable_homedirs --> off
ワークショップ、Pgadmin-webインターフェースにアクセス
実際の例を考えてみましょう。PostgreSQLデータベース管理用にRHEL7.6pgadmin4-webにインストールしました。pg_hba.conf、postgresql.conf、およびconfig_local.pyを構成し、フォルダーへの権限を設定し、pipから欠落しているPythonモジュールをインストールするという小さな探求を行いました。すべての準備が整いました。実行すると、500 InternalServerエラーが発生します。
典型的な容疑者から始めて、/ var / log / httpd / error_logをチェックします。そこにはいくつかの興味深いエントリがあります。 この時点で、ほとんどのLinux管理者はsetencorce0を実行したくなるでしょう。それだけです。率直に言って、私が初めてそれをしたとき。もちろん、これも解決策ですが、最善とは言えません。
[timestamp] [core:notice] [pid 23689] SELinux policy enabled; httpd running as context system_u:system_r:httpd_t:s0
...
[timestamp] [wsgi:error] [pid 23690] [Errno 13] Permission denied: '/var/lib/pgadmin'
[timestamp] [wsgi:error] [pid 23690]
[timestamp] [wsgi:error] [pid 23690] HINT : You may need to manually set the permissions on
[timestamp] [wsgi:error] [pid 23690] /var/lib/pgadmin to allow apache to write to it.
構成がかさばるにもかかわらず、SELinuxはユーザーフレンドリーです。setroubleshootパッケージをインストールし、システムログを表示するだけで十分です。 OSにsystemdが存在する場合でも、systemctlを使用せずに、この方法でauditdサービスを再起動する必要があることに注意してください。システムログには、ブロックの事実だけでなく、禁止を克服する理由と方法も示されます。 次のコマンドを実行します 。pgadmin4-webWebページへのアクセスを確認し、すべてが機能します。
[admin@server ~]$ yum install setroubleshoot
[admin@server ~]$ journalctl -b -0
[admin@server ~]$ service restart auditd
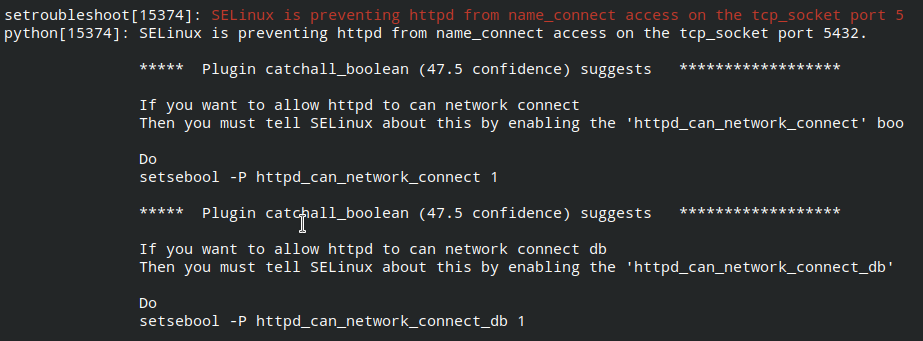
[admin@server ~]$ setsebool -P httpd_can_network_connect 1
[admin@server ~]$ setsebool -P httpd_can_network_connect_db 1

