
こんにちは、Habr!
現代の現実では、開発プロセスにおけるコンテナ化の役割が増大しているため、コンテナに関連するさまざまな段階やエンティティのセキュリティを確保するという問題は最後の場所ではありません。手動モードでチェックを実行するには時間がかかるため、少なくとも最初の手順を実行してこのプロセスを自動化するとよいでしょう。
この記事では、いくつかのDockerセキュリティユーティリティを実装するための既製のスクリプトと、このプロセスをテストするための小さなデモスタンドを展開する方法について説明します。リソースを使用して、イメージとDockerfile命令のセキュリティテストプロセスを整理する方法を試すことができます。開発と実装のインフラストラクチャは人によって異なることは明らかなので、以下にいくつかの可能なオプションを示します。
セキュリティチェックユーティリティ
Dockerインフラストラクチャのさまざまな側面をテストするさまざまなヘルパーアプリケーションとスクリプトがあります。それらのいくつかは、前の記事(https://habr.com/ru/company/swordfish_security/blog/518758/#docker-security)ですでに説明されています。この資料では、メインをカバーする3つに焦点を当てたいと思います。開発中に構築されるDockerイメージのセキュリティ要件の一部。さらに、セキュリティチェックを実行するためにこれら3つのユーティリティを1つのパイプラインに接続する方法の例も示します。
ハドリント
https://github.com/hadolint/hadolint
最初の概算として、Dockerfile命令の正確性とセキュリティを評価するのに役立つ非常に単純なコンソールユーティリティ(たとえば、許可されたイメージレジストリのみを使用するか、sudoを使用する)。

Dockle
https://github.com/goodwithtech/dockle
特定の画像自体の正確性とセキュリティをチェックし、そのレイヤーと構成(作成されたユーザー、手順)を分析する、画像(または画像の保存されたtarアーカイブ)を操作するコンソールユーティリティマウントされているボリューム、空のパスワードの存在などを使用しました。チェックの数はそれほど多くはなく、DockerのCIS(Center for Internet Security)ベンチマークの独自のチェックと推奨事項のいくつかに基づいています。
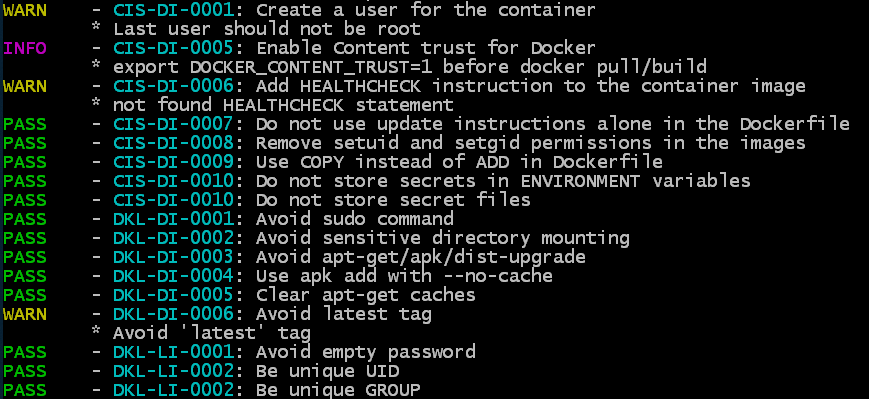
トリビー
https://github.com/aquasecurity/trivy
このユーティリティは、OSビルドの問題(Alpine、RedHat(EL)、CentOS、Debian GNU、Ubuntuでサポート)と依存関係の問題(Gemfile.lock、Pipfile)の2種類の脆弱性を見つけることを目的としています。 lock、composer.lock、package-lock.json、yarn.lock、Cargo.lock)。Trivyは、リポジトリ内のイメージとローカルイメージの両方をスキャンできるだけでなく、Dockerイメージを使用して転送された.tarファイルに基づいてスキャンすることもできます。
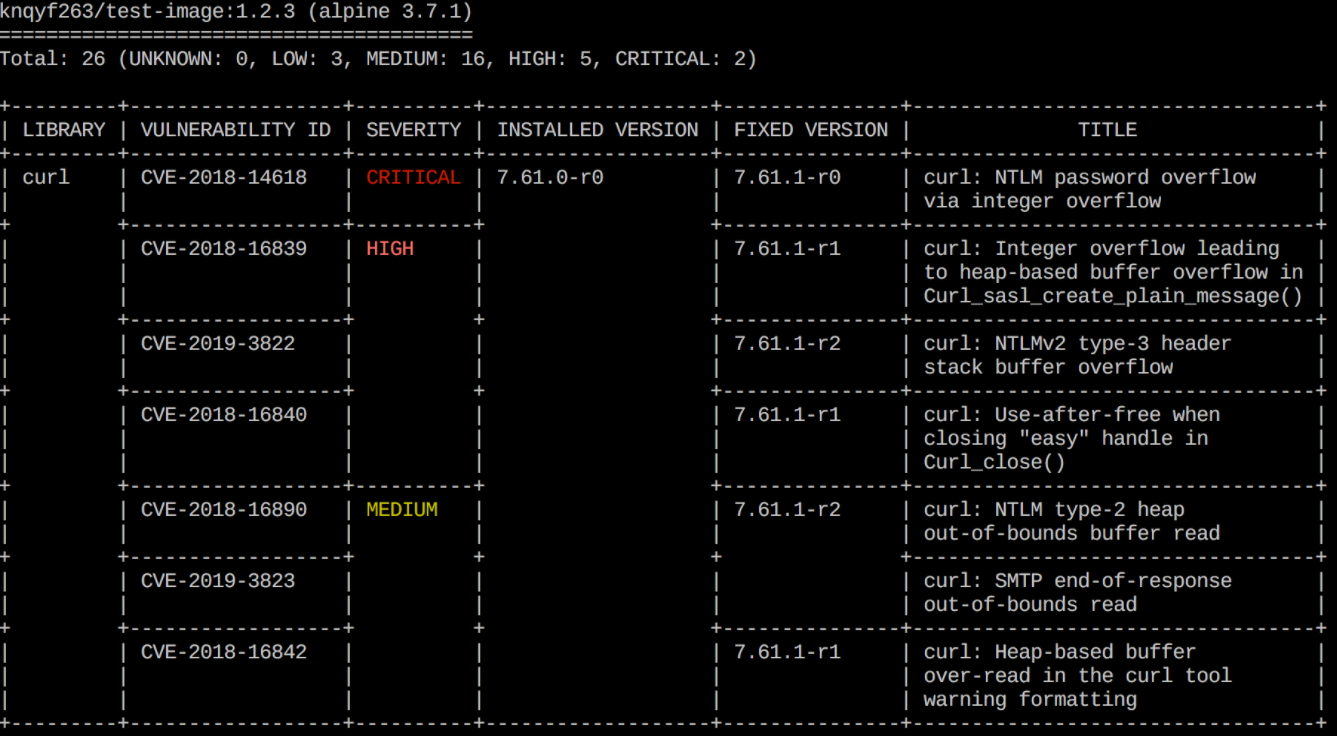
ユーティリティの実装オプション
説明したアプリケーションを分離した状態で試すために、すべてのユーティリティを簡単なプロセスでインストールするための手順を説明します。
主なアイデアは、開発中に作成されたDockerfileおよびDockerイメージの自動コンテンツ検証を実装する方法を示すことです。
チェック自体は、次の手順で構成されています。
- Dockerfile命令の正確性と安全性の確認-Hadolintリンターを使用
- Dockleユーティリティを使用してターゲットイメージと中間イメージの正確性とセキュリティを確認する
- Trivyユーティリティを使用して、ベースイメージの既知の脆弱性(CVE)と多数の依存関係を確認します。
この記事の後半で、これらの手順を実装するための3つのオプションを示します。
最初に、GitLabの例を使用してCI / CDパイプラインを構成します(テストインスタンスを発生させるプロセスの説明付き)。
2つ目は、シェルスクリプトを使用することです。
3つ目は、DockerイメージをスキャンするためのDockerイメージを構築することです。
自分に最適なオプションを選択し、それをインフラストラクチャに転送して、ニーズに適合させることができます。
必要なすべてのファイルと追加の手順もリポジトリにあります:https://github.com/Swordfish-Security/docker_cicd
GitLab CI / CDへの統合
最初のオプションでは、GitLabリポジトリシステムの例を使用してセキュリティチェックを実装する方法を見ていきます。ここでは、手順を実行し、GitLabを使用してテスト環境を最初からセットアップする方法を分析し、スキャンプロセスを作成し、ユーティリティを実行して、テストDockerfileとランダムイメージ(JuiceShopアプリケーション)をチェックします。
GitLabのインストール1.Dockerをインストールします
。
sudo apt-get update && sudo apt-get install docker.io2.現在のユーザーをdockerグループに追加して、sudoを介さずにdockerを操作できるようにします。
sudo addgroup <username> docker3. IPを見つけます:
ip addr4. GitLabをコンテナにインストールして実行し、ホスト名のIPアドレスを独自のものに置き換えます。
docker run --detach \
--hostname 192.168.1.112 \
--publish 443:443 --publish 80:80 \
--name gitlab \
--restart always \
--volume /srv/gitlab/config:/etc/gitlab \
--volume /srv/gitlab/logs:/var/log/gitlab \
--volume /srv/gitlab/data:/var/opt/gitlab \
gitlab/gitlab-ce:latestGitLabが必要なすべてのインストール手順を完了するのを待っています(ログファイルの出力を介してプロセスに従うことができます:docker logs -fgitlab)。
5.ブラウザでローカルIPを開き、rootユーザーのパスワードを変更する提案のあるページを表示します。
新しいパスワードを設定してGitLabに移動します。
6.新しいプロジェクト、例えばCICDテストを作成し、起動ファイルで初期化README.md:
要求に応じて、必要なすべての操作を起動するエージェント:7.今、私たちはGitLabランナーをインストールする必要があります。
最新バージョンをダウンロードします(この場合、Linux 64ビットの場合)。
sudo curl -L --output /usr/local/bin/gitlab-runner https://gitlab-runner-downloads.s3.amazonaws.com/latest/binaries/gitlab-runner-linux-amd648.実行可能にします。
sudo chmod +x /usr/local/bin/gitlab-runner9.ランナーのOSユーザーを追加し、サービスを開始します。
sudo useradd --comment 'GitLab Runner' --create-home gitlab-runner --shell /bin/bash
sudo gitlab-runner install --user=gitlab-runner --working-directory=/home/gitlab-runner
sudo gitlab-runner start次のようになります。
local@osboxes:~$ sudo gitlab-runner install --user=gitlab-runner --working-directory=/home/gitlab-runner
Runtime platform arch=amd64 os=linux pid=8438 revision=0e5417a3 version=12.0.1
local@osboxes:~$ sudo gitlab-runner start
Runtime platform arch=amd64 os=linux pid=8518 revision=0e5417a3 version=12.0.110.次に、ランナーを登録して、GitLabインスタンスと対話できるようにします。
これを行うには、[設定] -CI / CDページ(http:// OUR_ IP_ADDRESS / root / cicd-test /-/ settings / ci_cd)を開き、[ランナー]タブでURLと登録トークンを見つけます。11。URLと登録トークン
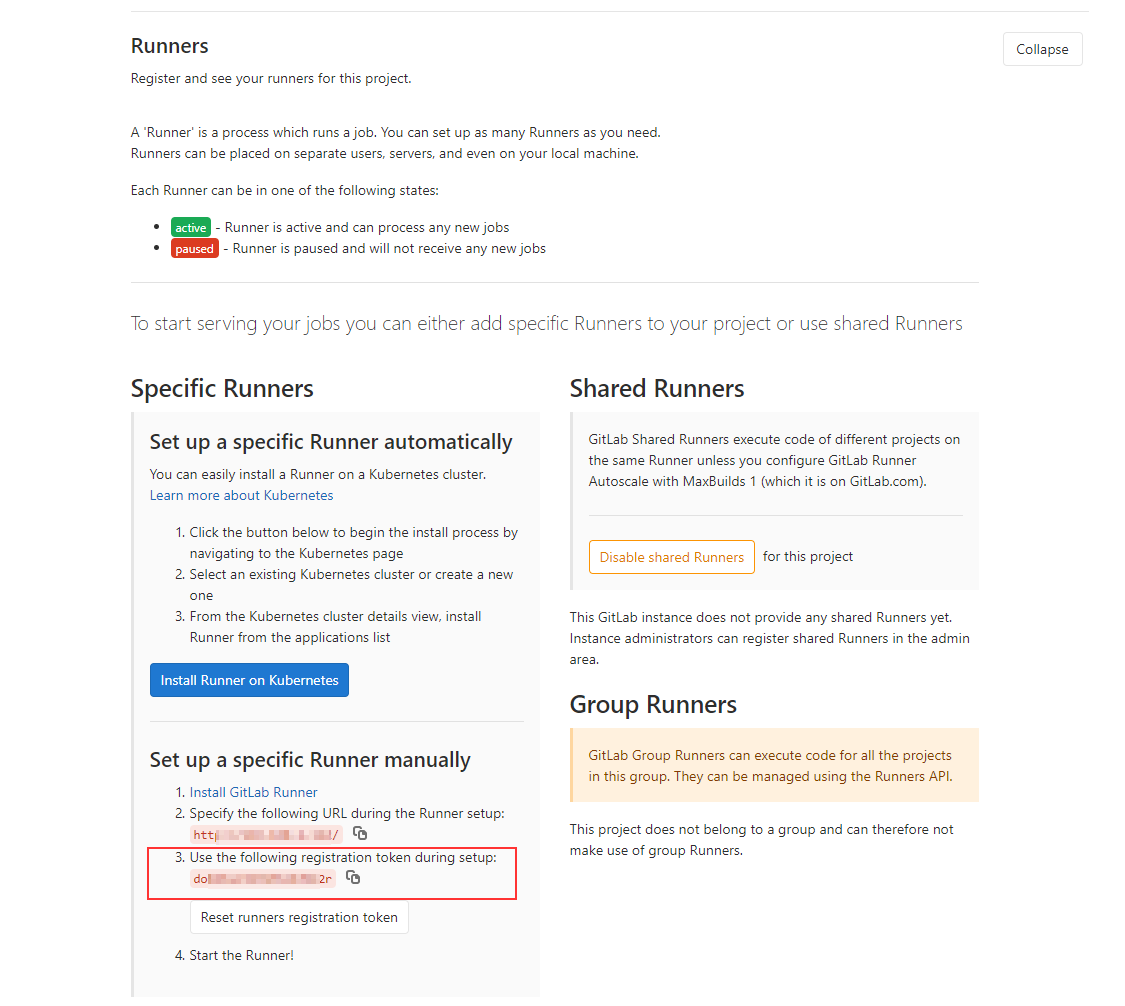
を置き換えてランナーを登録します。
sudo gitlab-runner register \
--non-interactive \
--url "http://<URL>/" \
--registration-token "<Registration Token>" \
--executor "docker" \
--docker-privileged \
--docker-image alpine:latest \
--description "docker-runner" \
--tag-list "docker,privileged" \
--run-untagged="true" \
--locked="false" \
--access-level="not_protected"その結果、既製の動作するGitLabが得られ、ユーティリティを起動するための手順を追加する必要があります。このデモの場合、アプリケーションとそのコンテナ化を構築するための手順はありませんが、実際の環境では、スキャン手順の前に実行され、分析用のイメージとDockerfileが生成されます。
パイプラインの構成
1.リポジトリにファイルmydockerfile.df(これはチェックするテストDockerfileです)とGitLab CI / CDプロセス構成ファイル.gitlab-cicd.ymlを追加します。これには、スキャナーの手順がリストされています(ファイル名のドットに注意してください)。 )。
YAML構成ファイルには、選択したDockerfileとDOCKERFILE変数で指定されたイメージを解析する3つのユーティリティ(Hadolint、Docle、およびTrivy)を実行するための命令が含まれています。必要なすべてのファイルは、リポジトリから取得できます。https://github.com/Swordfish-Security/docker_cicd/ mydockerfile.df
からの抜粋(これは、ユーティリティの動作を示すための任意の命令のセットを含む抽象ファイルです)。ファイルへの直接リンク:mydockerfile.df
mydockerfile.dfの内容
FROM amd64/node:10.16.0-alpine@sha256:f59303fb3248e5d992586c76cc83e1d3700f641cbcd7c0067bc7ad5bb2e5b489 AS tsbuild
COPY package.json .
COPY yarn.lock .
RUN yarn install
COPY lib lib
COPY tsconfig.json tsconfig.json
COPY tsconfig.app.json tsconfig.app.json
RUN yarn build
FROM amd64/ubuntu:18.04@sha256:eb70667a801686f914408558660da753cde27192cd036148e58258819b927395
LABEL maintainer="Rhys Arkins <rhys@arkins.net>"
LABEL name="renovate"
...
COPY php.ini /usr/local/etc/php/php.ini
RUN cp -a /tmp/piik/* /var/www/html/
RUN rm -rf /tmp/piwik
RUN chown -R www-data /var/www/html
ADD piwik-cli-setup /piwik-cli-setup
ADD reset.php /var/www/html/
## ENTRYPOINT ##
ADD entrypoint.sh /entrypoint.sh
ENTRYPOINT ["/entrypoint.sh"]
USER root構成YAMLは次のようになります(ファイル自体は、次の直接リンクから取得できます:.gitlab-ci.yml):
.Gitlab-ci.ymlコンテンツ
variables:
DOCKER_HOST: "tcp://docker:2375/"
DOCKERFILE: "mydockerfile.df" # name of the Dockerfile to analyse
DOCKERIMAGE: "bkimminich/juice-shop" # name of the Docker image to analyse
# DOCKERIMAGE: "knqyf263/cve-2018-11235" # test Docker image with several CRITICAL CVE
SHOWSTOPPER_PRIORITY: "CRITICAL" # what level of criticality will fail Trivy job
TRIVYCACHE: "$CI_PROJECT_DIR/.cache" # where to cache Trivy database of vulnerabilities for faster reuse
ARTIFACT_FOLDER: "$CI_PROJECT_DIR"
services:
- docker:dind # to be able to build docker images inside the Runner
stages:
- scan
- report
- publish
HadoLint:
# Basic lint analysis of Dockerfile instructions
stage: scan
image: docker:git
after_script:
- cat $ARTIFACT_FOLDER/hadolint_results.json
script:
- export VERSION=$(wget -q -O - https://api.github.com/repos/hadolint/hadolint/releases/latest | grep '"tag_name":' | sed -E 's/.*"v([^"]+)".*/\1/')
- wget https://github.com/hadolint/hadolint/releases/download/v${VERSION}/hadolint-Linux-x86_64 && chmod +x hadolint-Linux-x86_64
# NB: hadolint will always exit with 0 exit code
- ./hadolint-Linux-x86_64 -f json $DOCKERFILE > $ARTIFACT_FOLDER/hadolint_results.json || exit 0
artifacts:
when: always # return artifacts even after job failure
paths:
- $ARTIFACT_FOLDER/hadolint_results.json
Dockle:
# Analysing best practices about docker image (users permissions, instructions followed when image was built, etc.)
stage: scan
image: docker:git
after_script:
- cat $ARTIFACT_FOLDER/dockle_results.json
script:
- export VERSION=$(wget -q -O - https://api.github.com/repos/goodwithtech/dockle/releases/latest | grep '"tag_name":' | sed -E 's/.*"v([^"]+)".*/\1/')
- wget https://github.com/goodwithtech/dockle/releases/download/v${VERSION}/dockle_${VERSION}_Linux-64bit.tar.gz && tar zxf dockle_${VERSION}_Linux-64bit.tar.gz
- ./dockle --exit-code 1 -f json --output $ARTIFACT_FOLDER/dockle_results.json $DOCKERIMAGE
artifacts:
when: always # return artifacts even after job failure
paths:
- $ARTIFACT_FOLDER/dockle_results.json
Trivy:
# Analysing docker image and package dependencies against several CVE bases
stage: scan
image: docker:git
script:
# getting the latest Trivy
- apk add rpm
- export VERSION=$(wget -q -O - https://api.github.com/repos/knqyf263/trivy/releases/latest | grep '"tag_name":' | sed -E 's/.*"v([^"]+)".*/\1/')
- wget https://github.com/knqyf263/trivy/releases/download/v${VERSION}/trivy_${VERSION}_Linux-64bit.tar.gz && tar zxf trivy_${VERSION}_Linux-64bit.tar.gz
# displaying all vulnerabilities w/o failing the build
- ./trivy -d --cache-dir $TRIVYCACHE -f json -o $ARTIFACT_FOLDER/trivy_results.json --exit-code 0 $DOCKERIMAGE
# write vulnerabilities info to stdout in human readable format (reading pure json is not fun, eh?). You can remove this if you don't need this.
- ./trivy -d --cache-dir $TRIVYCACHE --exit-code 0 $DOCKERIMAGE
# failing the build if the SHOWSTOPPER priority is found
- ./trivy -d --cache-dir $TRIVYCACHE --exit-code 1 --severity $SHOWSTOPPER_PRIORITY --quiet $DOCKERIMAGE
artifacts:
when: always # return artifacts even after job failure
paths:
- $ARTIFACT_FOLDER/trivy_results.json
cache:
paths:
- .cache
Report:
# combining tools outputs into one HTML
stage: report
when: always
image: python:3.5
script:
- mkdir json
- cp $ARTIFACT_FOLDER/*.json ./json/
- pip install json2html
- wget https://raw.githubusercontent.com/shad0wrunner/docker_cicd/master/convert_json_results.py
- python ./convert_json_results.py
artifacts:
paths:
- results.html必要に応じて、保存した画像を.tarアーカイブとしてスキャンすることもできます(ただし、YAMLファイルのユーティリティの入力パラメータを変更する必要があります)。
NB: Trivy rpm git. RedHat-based .
2.ファイルをリポジトリに追加した後、構成ファイルの指示に従って、GitLabは自動的にビルドおよびスキャンプロセスを開始します。 [CI / CD]→[パイプライン]タブで、手順の進行状況を確認できます。
その結果、4つのタスクがあります。それらのうちの3つはスキャンを直接処理し、最後の(レポート)はスキャン結果とともに散在するファイルから単純なレポートを収集します。
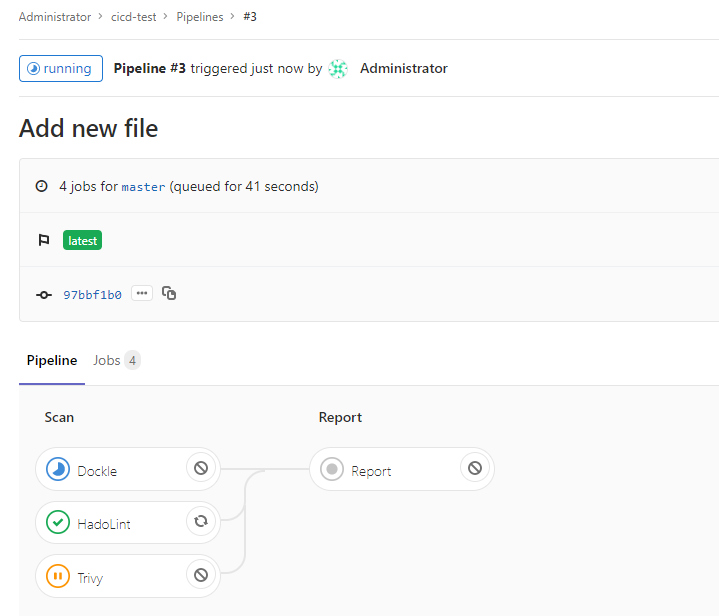
デフォルトでは、画像または依存関係に重大な脆弱性が見つかった場合、Trivyは実行を停止します。同時に、Hadolintは常にSuccess実行コードを返します。これは、実行の結果として常にコメントがあり、ビルドの停止につながるためです。
特定の要件に応じて、これらのユーティリティが特定の重大度の問題を検出したときにビルドプロセスも停止するように、終了コードを構成できます。この場合、ビルドは、Trivyが.gitlab-ci.ymlのSHOWSTOPPER変数で指定した重大な脆弱性を検出した場合にのみ停止します。
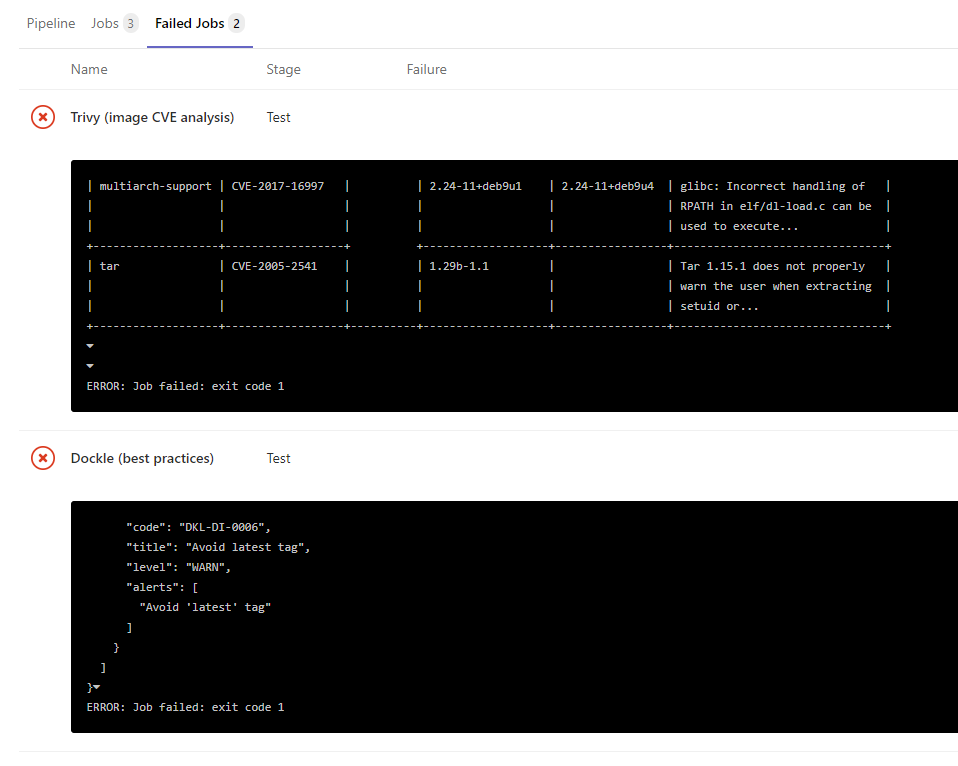
各ユーティリティの操作の結果は、各スキャンタスクのログ、アーティファクトセクションのjsonファイル、または単純なHTMLレポート(詳細は以下)で確認できます
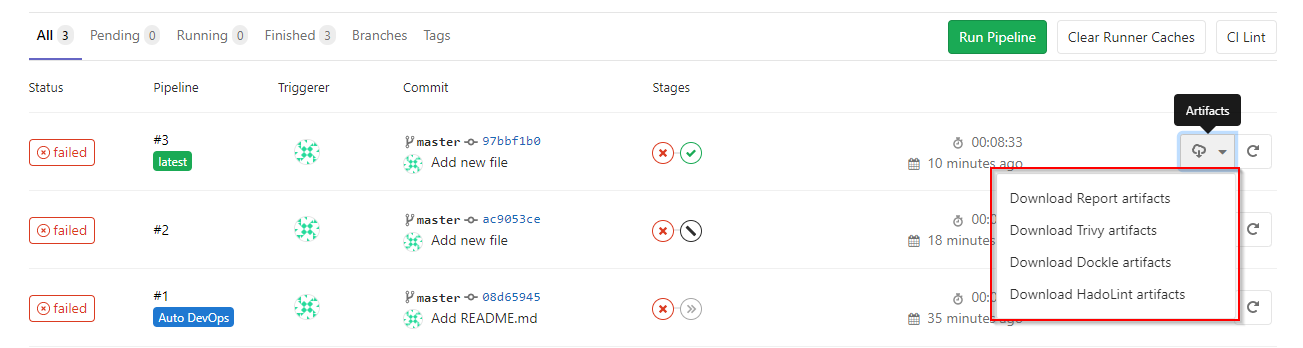
。3。ユーティリティレポートをもう少し人間が読みやすい形式で表示するには、小さなPythonスクリプトを使用します。 3つのjsonファイルを欠陥のテーブルを持つ1つのHTMLファイルに変換します。
このスクリプトは別のレポートタスクによって起動され、その最終的なアーティファクトはレポートを含むHTMLファイルです。スクリプトのソースもリポジトリにあり、ニーズや色などに合わせて調整できます。
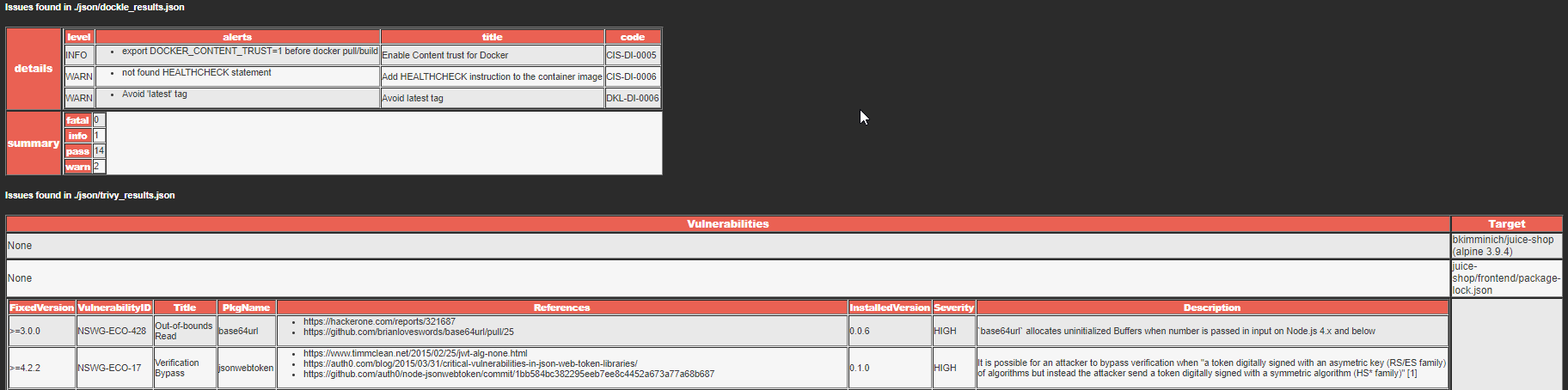
シェルスクリプト
2番目のオプションは、CI / CDシステムの外部でDockerイメージをチェックする必要がある場合、またはホスト上で直接実行できる形式ですべての命令を用意する必要がある場合に適しています。このオプションは、クリーンな仮想(または実際の)マシンで実行できる既製のシェルスクリプトでカバーされています。スクリプトは、上記のgitlab-runnerと同じ手順に従います。
スクリプトが正常に機能するには、Dockerがシステムにインストールされており、現在のユーザーがdockerグループに属している必要があります。
スクリプト自体は次の場所で取得できます。docker_sec_check.sh
ファイルの先頭で、変数を使用して、スキャンする画像と、指定されたエラーコードでTrivyユーティリティを終了させる重要度の欠陥を設定します。
スクリプトの実行中は、すべてのユーティリティはにダウンロードされますdocker_toolsのディレクトリに- 、自分の仕事の結果をdocker_tools / JSONのディレクトリ、およびレポートとHTMLがになりますresults.htmlファイル。
サンプルスクリプト出力
~/docker_cicd$ ./docker_sec_check.sh
[+] Setting environment variables
[+] Installing required packages
[+] Preparing necessary directories
[+] Fetching sample Dockerfile
2020-10-20 10:40:00 (45.3 MB/s) - ‘Dockerfile’ saved [8071/8071]
[+] Pulling image to scan
latest: Pulling from bkimminich/juice-shop
[+] Running Hadolint
...
Dockerfile:205 DL3015 Avoid additional packages by specifying `--no-install-recommends`
Dockerfile:248 DL3002 Last USER should not be root
...
[+] Running Dockle
...
WARN - DKL-DI-0006: Avoid latest tag
* Avoid 'latest' tag
INFO - CIS-DI-0005: Enable Content trust for Docker
* export DOCKER_CONTENT_TRUST=1 before docker pull/build
...
[+] Running Trivy
juice-shop/frontend/package-lock.json
=====================================
Total: 3 (UNKNOWN: 0, LOW: 1, MEDIUM: 0, HIGH: 2, CRITICAL: 0)
+---------------------+------------------+----------+---------+-------------------------+
| LIBRARY | VULNERABILITY ID | SEVERITY | VERSION | TITLE |
+---------------------+------------------+----------+---------+-------------------------+
| object-path | CVE-2020-15256 | HIGH | 0.11.4 | Prototype pollution in |
| | | | | object-path |
+---------------------+------------------+ +---------+-------------------------+
| tree-kill | CVE-2019-15599 | | 1.2.2 | Code Injection |
+---------------------+------------------+----------+---------+-------------------------+
| webpack-subresource | CVE-2020-15262 | LOW | 1.4.1 | Unprotected dynamically |
| | | | | loaded chunks |
+---------------------+------------------+----------+---------+-------------------------+
juice-shop/package-lock.json
============================
Total: 20 (UNKNOWN: 0, LOW: 1, MEDIUM: 6, HIGH: 8, CRITICAL: 5)
...
juice-shop/package-lock.json
============================
Total: 5 (CRITICAL: 5)
...
[+] Removing left-overs
[+] Making the output look pretty
[+] Converting JSON results
[+] Writing results HTML
[+] Clean exit ============================================================
[+] Everything is done. Find the resulting HTML report in results.htmlすべてのユーティリティを備えたDockerイメージ
3番目の方法として、2つの単純なDockerfileをコンパイルして、セキュリティユーティリティを使用してイメージを作成しました。1つのDockerfileは、リポジトリからイメージをスキャンするためのセットを構築するのに役立ちます。2つ目(Dockerfile_tar)は、イメージを含むtarファイルをスキャンするためのセットを構築します。
1.対応するDockerファイルとスクリプトをリポジトリhttps://github.com/Swordfish-Security/docker_cicd/tree/master/Dockerfileから取得します。
2.組み立てのために実行します。
docker build -t dscan:image -f docker_security.df .
3.アセンブリの終了後、画像からコンテナを作成します。同時に、関心のあるイメージの名前を使用してDOCKERIMAGE環境変数を渡し、分析するDockerfileをマシンからファイル/ Dockerfileにマウントします(このファイルへの絶対パスが必要であることに注意してください)。
docker run --rm -v $(pwd)/results:/results -v $(pwd)/docker_security.df:/Dockerfile -e DOCKERIMAGE="bkimminich/juice-shop" dscan:image
[+] Setting environment variables
[+] Running Hadolint
/Dockerfile:3 DL3006 Always tag the version of an image explicitly
[+] Running Dockle
WARN - DKL-DI-0006: Avoid latest tag
* Avoid 'latest' tag
INFO - CIS-DI-0005: Enable Content trust for Docker
* export DOCKER_CONTENT_TRUST=1 before docker pull/build
INFO - CIS-DI-0006: Add HEALTHCHECK instruction to the container image
* not found HEALTHCHECK statement
INFO - DKL-LI-0003: Only put necessary files
* unnecessary file : juice-shop/node_modules/sqlite3/Dockerfile
* unnecessary file : juice-shop/node_modules/sqlite3/tools/docker/architecture/linux-arm64/Dockerfile
* unnecessary file : juice-shop/node_modules/sqlite3/tools/docker/architecture/linux-arm/Dockerfile
[+] Running Trivy
...
juice-shop/package-lock.json
============================
Total: 20 (UNKNOWN: 0, LOW: 1, MEDIUM: 6, HIGH: 8, CRITICAL: 5)
...
[+] Making the output look pretty
[+] Starting the main module ============================================================
[+] Converting JSON results
[+] Writing results HTML
[+] Clean exit ============================================================
[+] Everything is done. Find the resulting HTML report in results.html結果
Dockerアーティファクトをスキャンするための基本的なツールセットを1つだけ取り上げました。これは、私の意見では、イメージセキュリティ要件のかなりの部分を非常に効果的にカバーしています。同じチェックを実行したり、美しいレポートを作成したり、純粋にコンソールモードで作業したり、コンテナ管理システムをカバーしたりできる無料および有料のツールは他にもたくさんあります。これらのツールの概要と統合方法については、少し後で説明します。
この記事で説明されている一連のツールの良い面は、すべてオープンソースコードに基づいて構築されており、それらや他の同様のツールを試して、要件やインフラストラクチャ機能に正確に適合するものを見つけることができることです。もちろん、発見されるすべての脆弱性は、特定の条件での適用可能性について調査する必要がありますが、これは将来の大きな記事のトピックです。
このチュートリアル、スクリプト、およびユーティリティがお役に立てば、コンテナ化の分野でより安全なインフラストラクチャを作成するための出発点になることを願っています。